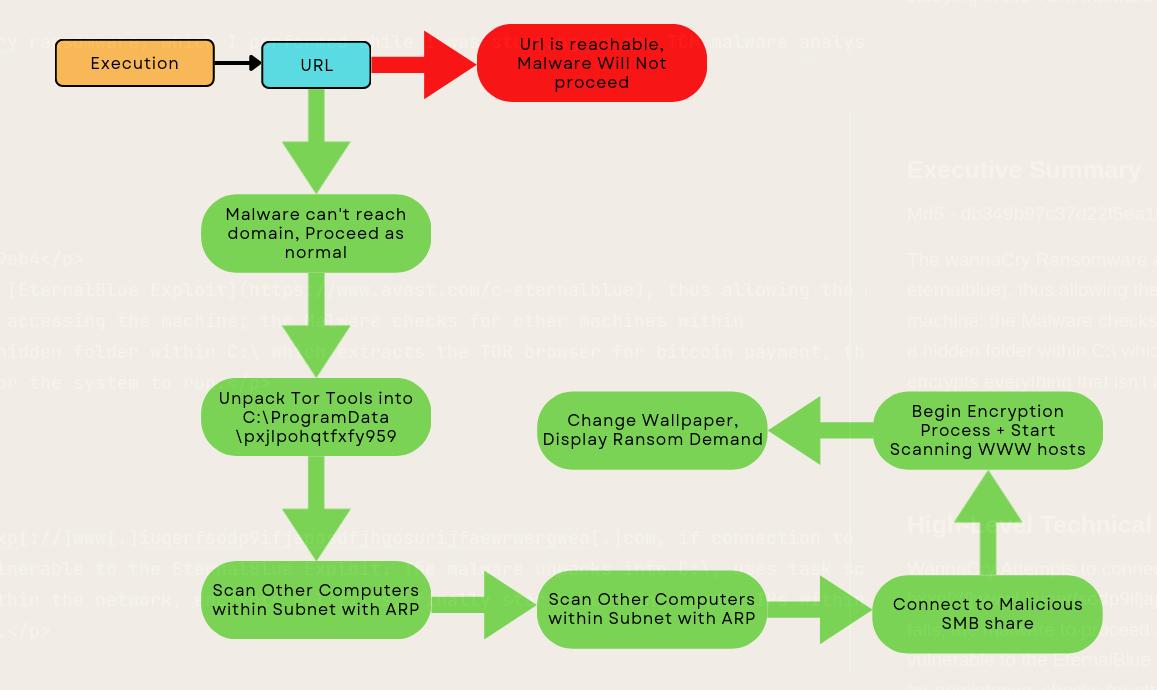
This was my analysis on the Wanna-cry ransomware, which I performed while I was studying in the TCM malware analysis lab.

Executive Summary
Md5 - db349b97c37d22f5ea1d1841e3c89eb4
The wannaCry Ransomware abuses the EternalBlue Exploit, thus allowing the malware to gain administrator privileges upon accessing the machine; the Malware checks for other machines within the subnet with ARP calls, creates a hidden folder within C:\ which extracts the TOR browser for bitcoin payment, than encrypts everything that isn’t in SYSTEM32 or essential for the system to run.
High-Level Technical Summary
WannaCry Attempts to connect to hxxp[://]www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com, if connection to this url fails, the malware to proceed as normal, encrypting and trying to spread to other host vulnerable to the EternalBlue Exploit. The malware unpacks into C:\, uses task scheduler for persistence, checks for other host within the network, encrypts all files, finally starts scanning random IPs within the WWW for host with this same vulnerability.
Basic Static Analysis
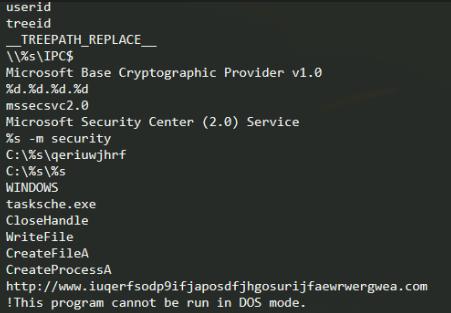 Url In plain string text
Url In plain string text
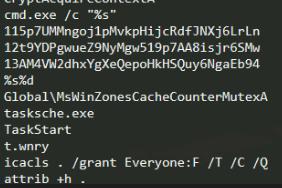 icacls command is executed to a file with a hidden attribute
icacls command is executed to a file with a hidden attribute
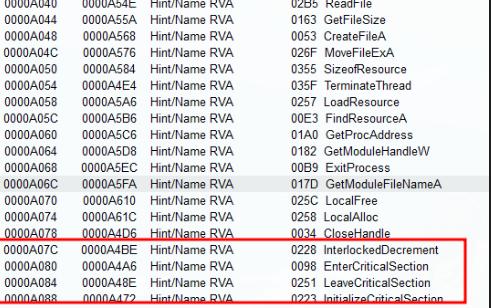 Multiple IAT’s from the kernel32.api is called
Multiple IAT’s from the kernel32.api is called
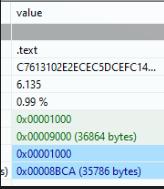 Virtual Size and Raw Size are similar, file may not be compressed
Virtual Size and Raw Size are similar, file may not be compressed
Dynamic Analysis
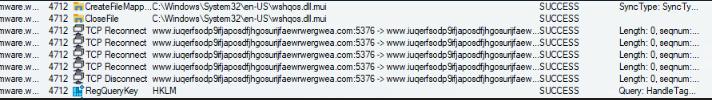 Checks if it can connect to this url, if it can, it will not execute, if not, execute as normal
Checks if it can connect to this url, if it can, it will not execute, if not, execute as normal
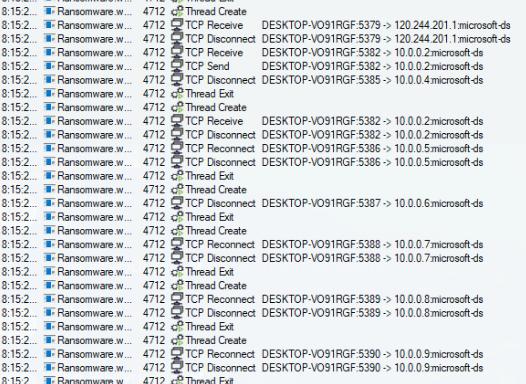 Check other devices within subnet, vulnerability check on local network
Check other devices within subnet, vulnerability check on local network
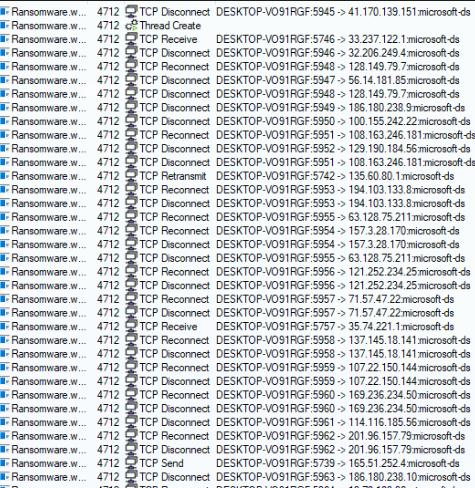 Start scanning for hosts on the WWW, allowing it to spread to another host if the vulnerability is found
Start scanning for hosts on the WWW, allowing it to spread to another host if the vulnerability is found
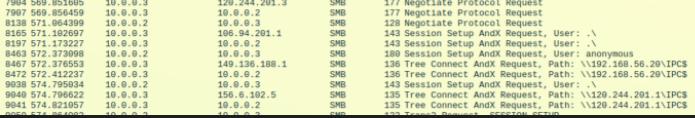 Connect to a malicious and a local SMB using anonymous creds
Connect to a malicious and a local SMB using anonymous creds
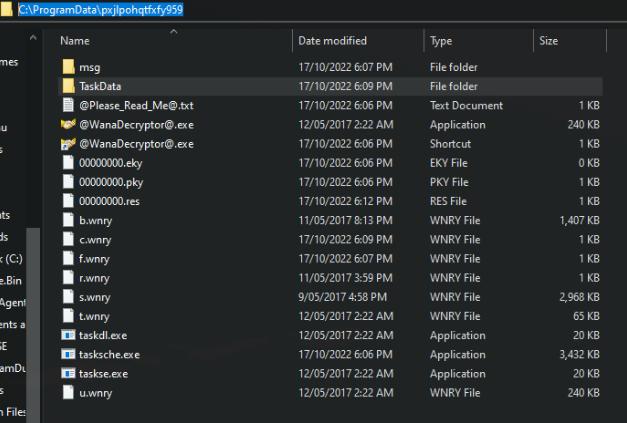 Unpacks Tor files here along with ransom notes demanding ransom
Unpacks Tor files here along with ransom notes demanding ransom
Advanced Static Analysis
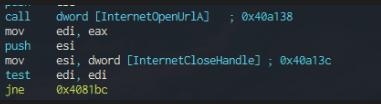 Check if it can connect to url, if not continue… confirmed when I switched the “Jump if Not Equal” instruction, and it executed with the opposite condition
Check if it can connect to url, if not continue… confirmed when I switched the “Jump if Not Equal” instruction, and it executed with the opposite condition
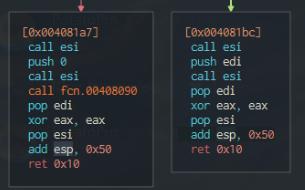 Left graph displays instructions if the binary can’t connect to the url, Right graph is if it can connect to the url
Left graph displays instructions if the binary can’t connect to the url, Right graph is if it can connect to the url
Yara Rule
rule Wannacry {
meta:
last_updated = "2022-10-24"
author = "Potatech"
description = "Were da Wannacry at tho"
strings:
$strings1 = "iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea" ascii
$strings2 = "WINDOWS"
$strings3 = "tasksche.exe"
$PE_magic_byte = "MZ"
condition:
$PE_magic_byte at 0 and
($strings1 and $strings2) or
($strings1 and $strings3)
}